15 Best SIEM Tools in 2023: Vendors & Solutions Ranked (Paid & Free)

SIEM stands for Security Information and Event Management. SIEM tools provide real-time analysis of security alerts generated by applications and network hardware.
There are 50+ SIEM solutions on the market and this guide will help you identify the right one for your organization.
Mục lục bài viết
Here is our list of the best SIEM tools:
- Datadog Security Monitoring
EDITOR’S CHOICE
A cloud-native network monitoring and management system that includes real-time security monitoring and log management. Comes with over 600 vendor integrations out-of-the-box. Start on a 14-day free trial. - SolarWinds Security Event Manager
(FREE TRIAL)
One of the most competitive SIEM tools on the market with a wide range of log management features. - Logpoint
(ACCESS DEMO)
This on-premises SIEM solution is able to orchestrate with other security tools on the network to gather activity data and implement threat remediation.
- Graylog
(FREE PLAN)
This log management package includes a SIEM service extension that is available in free and paid versions and has a cloud option. - ManageEngine EventLog Analyzer
(FREE TRIAL)
A SIEM tool that manages, protects, and mines log files. This system installs on Windows, Windows Server, and Linux.
- ManageEngine Log360
(FREE TRIAL)
This SIEM package collects logs from on-premises and cloud systems and also uses a threat intelligence feed. Runs on Windows Server.
- Exabeam Fusion This cloud platform offers a security solution that could be regarded as a next-gen SIEM or a next-gen XDR.
- Elastic Security This package applies SIEM rules to the Elastic Stack group of products and provides live threat detection plus historical analysis. Available as a SaaS package or for installation on Windows, macOS, or Linux.
- Fortinet FortiSIEM This security package from a highly respected provider can be combined with other Fortinet products and is offered as a hardware appliance, a virtual appliance, or as a service on AWS.
- Splunk Enterprise Security This tool for Windows and Linux is a world leader because it combines network analysis with log management together with an excellent analysis tool.
- Rapid7 InsightIDR This combined XDR and SIEM operates threat hunting in the cloud based on data collected by site agents.
- LogRhythm NextGen SIEM Platform Cutting-edge AI-based technology underpins this traffic and log analysis tool for Windows and Linux.
- Trellix Helix This cloud-based system provides advanced persistent threat protection and uses SOAR to activate your existing security products for threat responses.
- AT&T Cybersecurity AlienVault Unified Security Management Great value SIEM that runs on Mac OS as well as Windows.
- IBM Security QRadar SIEM Market-leading SIEM tool that runs on Windows environments.
What is Security Information and Event Management (SIEM)?
SIEM is an umbrella term for security software packages ranging from Log Management Systems to Security Log / Event Management, Security Information Management, and Security Event correlation. More often than not these features are combined for a 360-degree view.
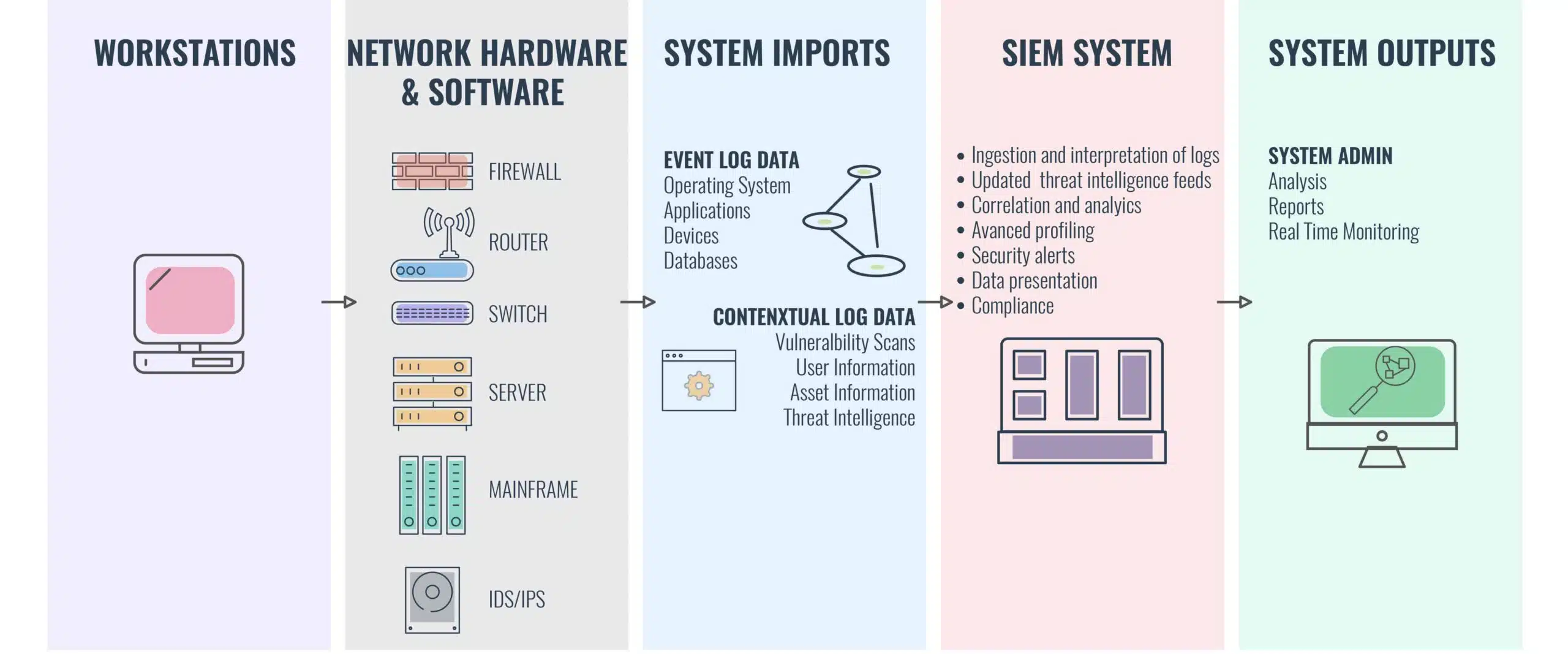
While a SIEM system isn’t foolproof, it’s one of the key indicators that an organization has a clearly defined cybersecurity policy. Nine times out of ten, cyber attacks don’t have any clear tells on a surface level. To detect threats, it’s more effective to use the log files. The superior log management capabilities of SIEMs have made them a central hub of network transparency.
Most security programs operate on a micro-scale, addressing smaller threats but missing the bigger picture of cyber threats. An Intrusion Detection System (IDS) alone can seldom do more than monitor packets and IP addresses. Likewise, your service logs only show user sessions and configuration changes. SIEM puts these systems and others like it together to provide a complete overview of any security incident through real-time monitoring and the analysis of event logs.
What is Security Information Management (SIM)?
Security Information Management (SIM) is the collection, monitoring, and analysis of security-related data from computer logs. Also referred to as log management.
What is Security Event Management (SEM)?
Security Event Management (SEM) is the practice of network event management including real-time threat analysis, visualization, and incident response.
SIEM vs SIM vs SEM – what’s the difference?
SIEM, SIM, and SEM are often used interchangeably but there are some key differences.
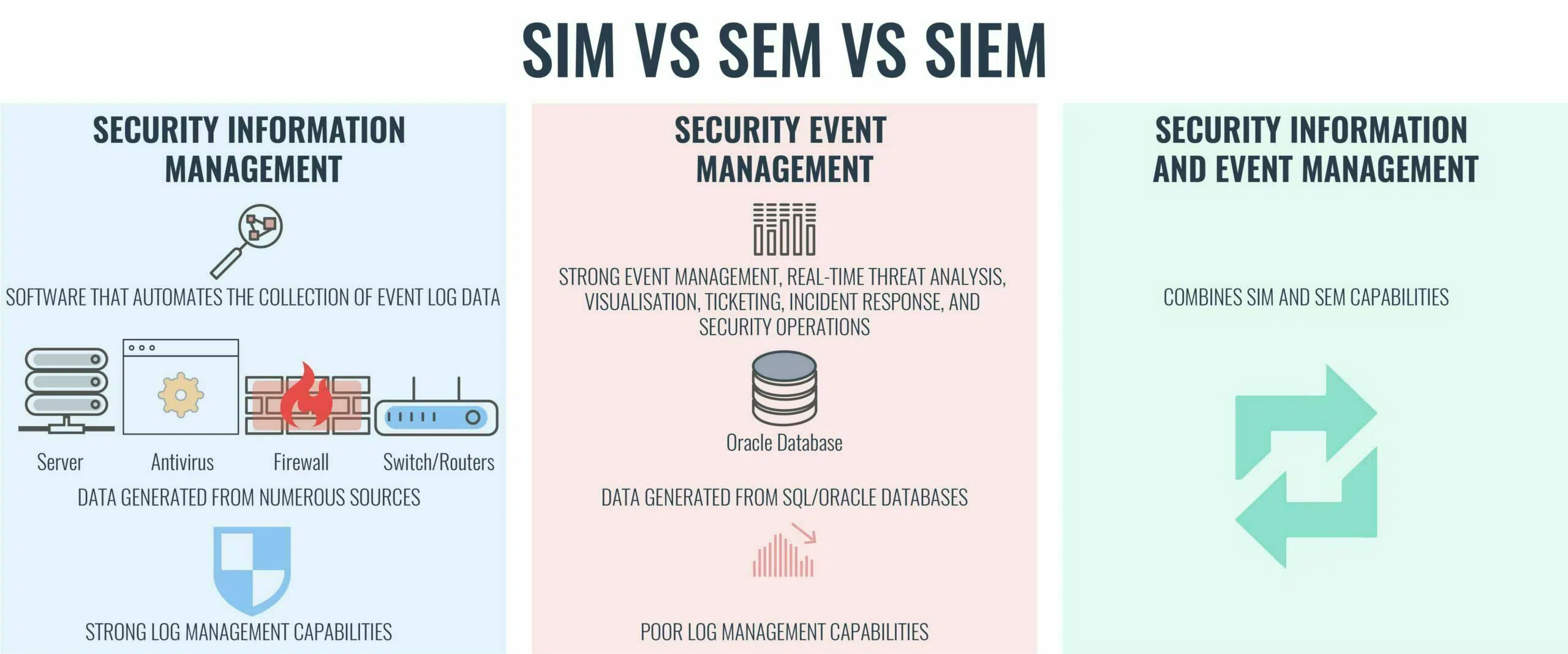
Security Information Management (SIM)Security Event Management (SEM)Security Information and Event Management (SIEM)
OverviewCollection and analysis of security-related data from computer logs.Real-time threat analysis, visualization and incident response.SIEM, as the name suggests, combines SIM and SEM capabilities.
FeaturesEasy to deploy, strong log management capabilities.More complex to deploy, superior at real-time monitoring.More complext to deploy, complete functionality.
Example ToolsOSSIMNetIQ SentinelSolarWinds Log & Event Manager
SIEM capabilities
SIEM’s basic capabilities are as follows:
- Log Collection
- Normalization – Collecting logs and normalizing them into a standard format)
- Notifications and Alerts – Notifying the user when security threats are identified
- Security Incident Detection
- Threat response workflow – Workflow for handling past security events
SIEM records data from across a users’ internal network of tools and identifies potential issues and attacks. The system operates under a statistical model to analyze log entries. SIEM distributes collection agents and recalls data from the network, devices, servers, and firewalls.
All this information is then passed to a management console where it can be analyzed to address emerging threats. It’s not uncommon for advanced SIEM systems to use automated responses, entity behavior analytics and security orchestration. This ensures that vulnerabilities between cybersecurity tools can be monitored and addressed by SIEM technology.
Once the necessary information reaches the management console, it is then viewed by a data analyst who can provide feedback on the overall process. This is important because feedback helps to educate the SIEM system in terms of machine learning and increasing its familiarity with the surrounding environment.
Once the SIEM software system identifies a threat, it then communicates with other security systems on the device to stop the unwanted activity. The collaborative nature of SIEM systems makes them a popular enterprise-scale solution. However, the rise of pervasive cyber threats has made many small- and mid-sized businesses consider the merits of a SIEM system as well.
This change has been relatively recent because of the substantial costs of SIEM adoption. Not only must you pay a sizeable amount for the system itself; you need to allocate one or two members of staff to oversee it. As a result, smaller organizations have been less enthusiastic about SIEM adoption. But that has begun to change as SMEs can outsource to managed service providers.
Why is SIEM Important?
SIEM has become a core security component of modern organizations. The main reason is that every user or tracker leaves behind a virtual trail in a network’s log data. SIEM systems are designed to use this log data in order to generate insight into past attacks and events. A SIEM system not only identifies that an attack has happened, but allows you to see how and why it happened as well.
As organizations update and upscale to increasingly complex IT infrastructures, SIEM has become even more critical in recent years. Contrary to popular belief, firewalls and antivirus packages are not enough to protect a network in its entirety. Zero-day attacks can still penetrate a system’s defenses even with these security measures in place.
SIEM addresses this problem by detecting attack activity and assessing it against past behavior on the network. A SIEM system has the ability to distinguish between legitimate use and a malicious attack. This helps to increase a system’s incident protection and avoid damage to systems and virtual property.
The use of SIEM also helps companies to comply with a variety of industry cyber management regulations. Log management is the industry-standard method of auditing activity on an IT network. SIEM systems provide the best way to meet this regulatory requirement and provide transparency over logs in order to generate clear insights and improvements.
Not all SIEM systems are built the same. As a result, there is no one-size-fits-all. A SIEM solution that’s right for one company may be incomplete to another. In this section, we break down the core features needed for a SIEM system.
- Log Data Management As mentioned above, log data management is a core component of any enterprise-scale SIEM system. A SIEM system needs to pool log info from a variety of different data sources, each with their own way of categorizing and recording data. When looking for a SIEM system, you want one that has the ability to normalize data effectively (you might need a third-party program if your SIEM system isn’t managing disparate log data well).
Once the data is normalized, it is then quantified and compared against previously recorded data. The SIEM system can then recognize patterns of malicious behavior and raise notifications to alert the user to take action. This data can then be searched by an analyst who can define new criteria for future alerts. This helps to develop the system’s defenses against new threats.
- Compliance Reporting In terms of convenience and regulatory requirements, having a SIEM with extensive compliance reporting features is very important. In general, most SIEM systems have some kind of onboard report generating system that will help you to conform to your compliance requirements.
The source of requirements of the standards that you need to conform to will be a major influence on which SIEM system you install. If your security standards are dictated by customer contracts, you don’t have much leeway on which SIEM system you choose — if it doesn’t support the required standard, then it won’t be any you’re used to. You may be required to demonstrate compliance to PCI DSS, FISMA, FERPA, HIPAA, SOX, ISO, NCUA, GLBA, NERC CIP, GPG13, DISA STIG or one of many other industry standards.
Threat Intelligence
If a breach or attack occurs, you can generate a report that details how it happened extensively. You can then use this data to refine internal processes and make adjustments to your network infrastructure to make sure it doesn’t happen again. This uses SIEM technology keeps your network infrastructure evolving to address new threats.
- Fine Tuning Alert Conditions Having the ability to set the criteria for future security alerts is essential for maintaining an effective SIEM system through threat intelligence. Refining alerts is the main way you keep your SIEM system updated against new threats. Innovative cyber-attacks are emerging every day, so using a system that’s designed to add new security alerts stops you from getting left behind.
You also want to make sure that you find a SIEM software platform that can limit the number of security alerts you receive. If you’re inundated with alerts your team is going to be unable to address security concerns in a timely manner. Without fining tuning alerts you’re going to be subjected to sifting through masses of events from firewalls to intrusion logs.
- Dashboard An extensive SIEM system is no good if you have a poor dashboard behind it. Having a dashboard with a simple user interface makes it much easier to identify threats. In practice, you’re looking for a dashboard with visualization. Straight away this allows your analyst to spot if any anomalies are occurring on the display. Ideally, you want a SIEM system that can be configured to show specific event data.
Before choosing a SIEM tool, it’s important to evaluate your goals. For example, if you’re looking for a SIEM tool to meet regulatory requirements, generating reports will be one of your foremost priorities.
On the other hand, if you want to use a SIEM system to stay protected against emerging attacks, you need one with high functioning normalization and extensive user-defined notification facilities. Below we take a look at some of the best SIEM tools on the market.
Our methodology for selecting a SIEM tool
We reviewed the SIEM market and analyzed tools based on the following criteria:
- A system that gathers both log messages and live traffic data
- A log file management module
- Data analysis utilities
- The ability to report to data protection standards
- Easy to install with an easy-to-use interface
- A trial period for assessment
- The right balance between functionality and value for money
Operating System: Cloud based
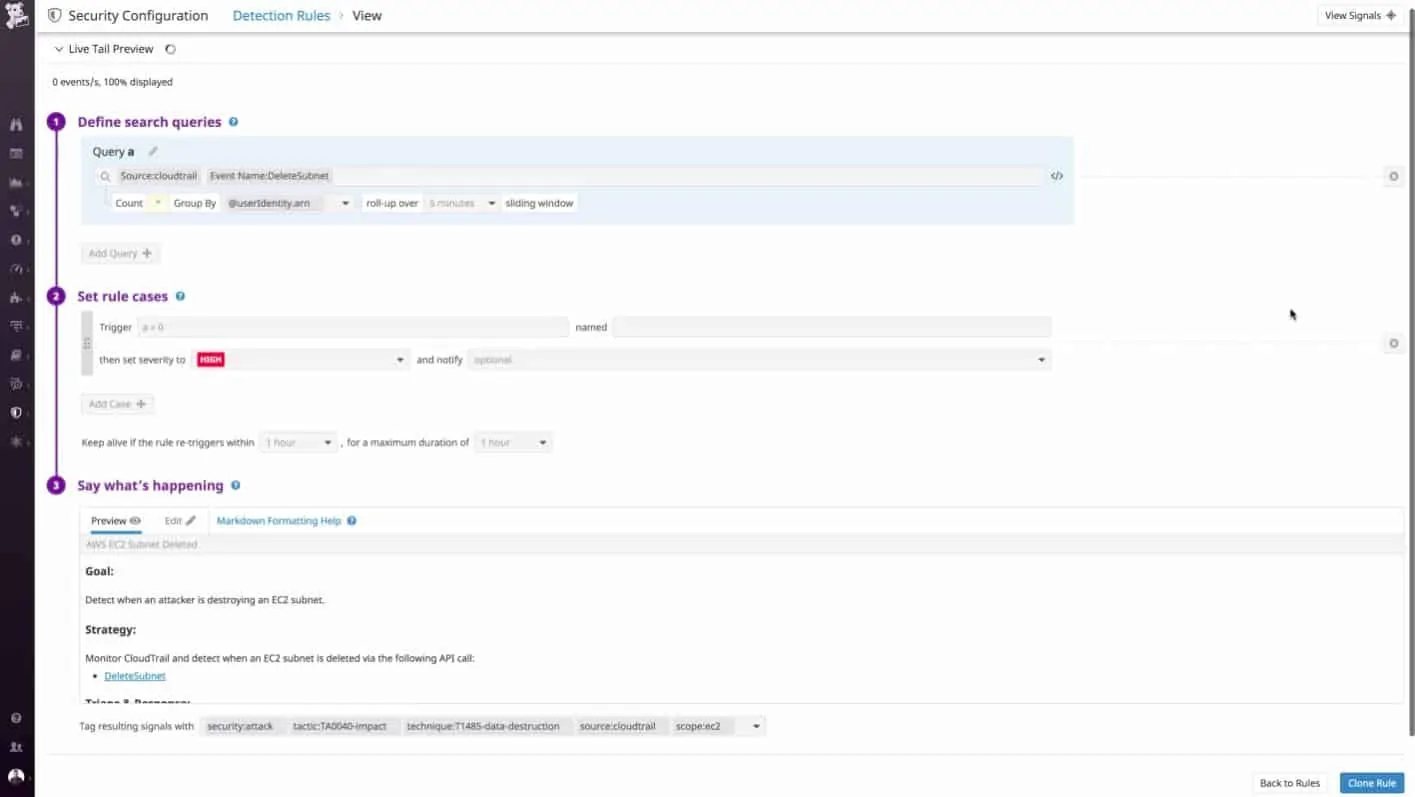
Datadog is a cloud-based system monitoring package that includes security monitoring. The security features of the system are contained in a specialized module. This is a full SIEM system because it monitors live events, but collects them as log file entries, so it operates both on log information and on monitoring data. The service collects local information through an agent, which uploads each record to the Datadog server. The security monitoring module then analyzes all incoming notifications and files them.
Key Features:
- Real-time security event detection
- Over 600 vendor integrations
- Observe metrics, traces, logs and more from one dashboard
- Solid out-of-the-box pre-configured detection rules
Why do we recommend it?
Datadog Security Monitoring is a cloud-based SIEM that is a great choice for multi-site businesses. The service is also able to gather activity data from cloud platforms, making it ideal for a hybrid system. The Datadog platform includes a range of tools that can extend the security monitoring of this package with other functions, such as log management and an audit trail service.
Security events trigger alerts in the console for the service. The console also gives access to all event records. Logged messages are indexed and retained for 15 months. They can be accessed for analysis through the Datadog console, or extracted in order to be imported into another analysis tool.
The offsite processing capabilities reduce the processing demands on your infrastructure. It also makes it very easy to monitor remote networks. The analysis service has a pre-defined set of rules that will automatically detect known attack vectors.
The pool of detection rules gets updated automatically by Datadog when new attack strategies are discovered. This means that the system administrators don’t need to worry about keeping security software up to date because that process happens automatically on the cloud server. It is also very easy for a systems administrator to create custom detection and mitigation rules.
Who is it recommended for?
This service is particularly useful for businesses that run applications and services on multiple sites and cloud platforms. The Datadog Cloud SIEM can collect log data from all platforms and consolidate them into a standard format for unified threat hunting.
Pros:
- Real-time threat detection
- Full security visibility with 500+ integrations
- Start detecting threats immediately with default rules mapped to MITRE ATT&CK framework
- Datadog scored 4.6/5 in Gartner survey of IT customers
- 14 day free trial
Cons:
- Wealth of functionality can be a little overwhelming initially
Datadog is available on a 14-day free trial.
EDITOR’S CHOICE
Datadog is our top choice. It offers a menu of specialist modules and all of them can be deployed individually or as a suite. You get greater functionality by combining modules, which are all able to share data about the monitored system.
Get 14 Day Free Trial: datadoghq.com/product/security-monitoring/
OS: Cloud-native
Operating System: Windows
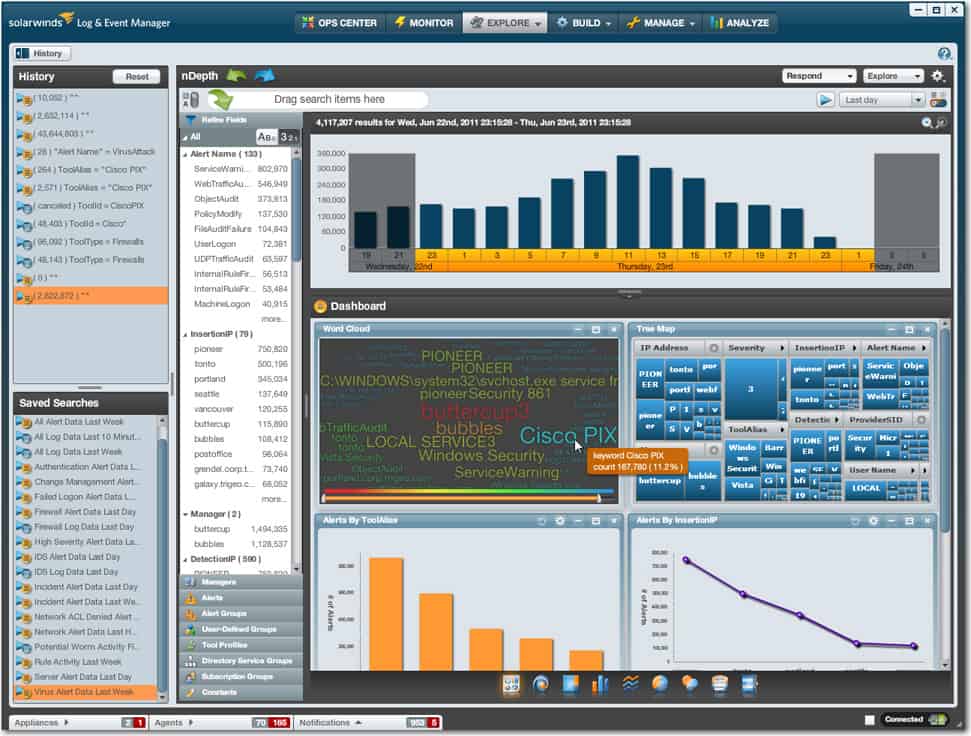
In terms of entry-level SIEM tools, SolarWinds Security Event Manager (SEM) is one of the most competitive offerings on the market. The SEM embodies all the core features you’d expect from a SIEM system, with extensive log management features and reporting. SolarWinds’ detailed real-time incident response makes it a great tool for those looking to exploit Windows event logs to actively manage their network infrastructure against future threats.
Key Features:
- Automated log searches for breaches
- Live anomaly detection
- Historical analysis
- System alerts
- 30-day free trial
Why do we recommend it?
The SolarWinds Security Event Manager is an on-premises service that is able to reach out to cloud platforms as well. This service can unify the monitoring of multiple sites and cloud services from its base on one of your servers.
One of the best things about the SEM is its detailed and intuitive dashboard design. The simplicity of the visualization tools makes it easy for the user to identify any anomalies. As a welcome bonus, the company offers 24/7 support, so you can contact them for advice if you run into an error.
Who is it recommended for?
This is a solution for large corporations that don’t want to risk having to rely on SaaS packages. Although cloud services are now in the ascendency, not everyone likes them.
Pros:
- Enterprise focused SIEM with a wide range of integrations
- Simple log filtering, no need to learn a custom query language
- Dozens of templates allow administrators to start using SEM with little setup or customization
- Historical analysis tool helps find anomalous behavior and outliers on the network
Cons:
- SEM Is an advanced SIEM product build for professionals, requires time to fully learn the platform
Good-looking interface with lots of graphical data visualization fronts a powerful and comprehensive SIEM tool that runs on Windows Server. The real-time incident response makes it easy to actively manage your infrastructure and the detailed and intuitive dashboard makes this one of the easiest to use on the market.
Get 30-day Free Trial: solarwinds.com/security-event-manager/
OS: Windows
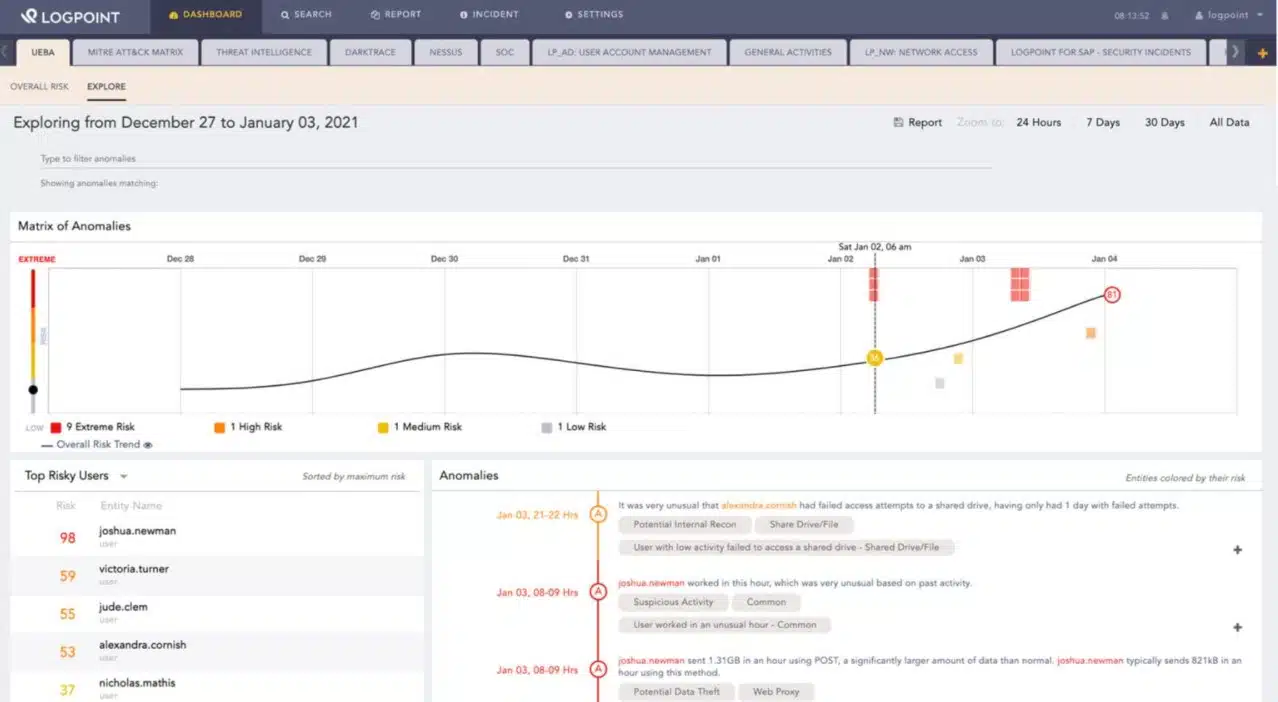
LogPoint is a cloud-based SIEM system that uses anomaly detection for its threat-hunting strategy.
The service uses machine learning processes to record the regular activity of each user and device. This establishes a baseline from which to identify unusual behavior, which triggers focused activity tracking. This technique is called user and entity behavior analytics (UEBA). The AI-based machine learning technique cuts down processing requirements because it limits intense investigations to just those accounts or devices that have raised suspicions.
Key Features:
- Efficient processing
- UEBA for activity baselining
- Account takeover detection
- Threat intelligence feed
Why do we recommend it?
Logpoint operates an anomaly-based threat-hunting strategy. That means it doesn’t rely on a database of malware signatures and so it can detect manual intrusion and zero-day attacks with ease.
The Logpoint system is informed by a database of typical attack strategies, which are called Indicators of Compromise (IoCs). This list of tricks is fairly static but whenever Logpoint identifies a new strategy, the company updates all of its SIEM system instances running on client sites around the world.
The triage strategy of Logpoint not only makes it low on CPU usage but it also makes the system fast. The threat detection indicators are stored centrally, so subsequent indicators that are identified will be correlated wherever they occur on the system.
Who is it recommended for?
Logpoint is a good solution for businesses that operate multiple sites and also use cloud platforms. This service can even operate well for companies that run a virtual office and rely entirely on cloud systems without any servers of their own.
Pros:
- Threat detection rules
- Orchestration with other tools
- Insider threat detection
- GDPR reporting
Cons:
- No free trial period
Logpoint is able to communicate with third-party tools to extract activity data and it collects that log message outputs from more than 25,000 different sources. The integration with other tools is called security orchestration, automation, and response (SOAR) and it can also send remediation instruction back to those other systems. There is a high degree of automation in the system, which includes the ability to generate tickets to feed into your Service Desk system.
Logpoint is a cloud-based SaaS package. There is no free trial. There is no free trial, but you can request a demo to assess the package
Logpoint
Access FREE DEMO
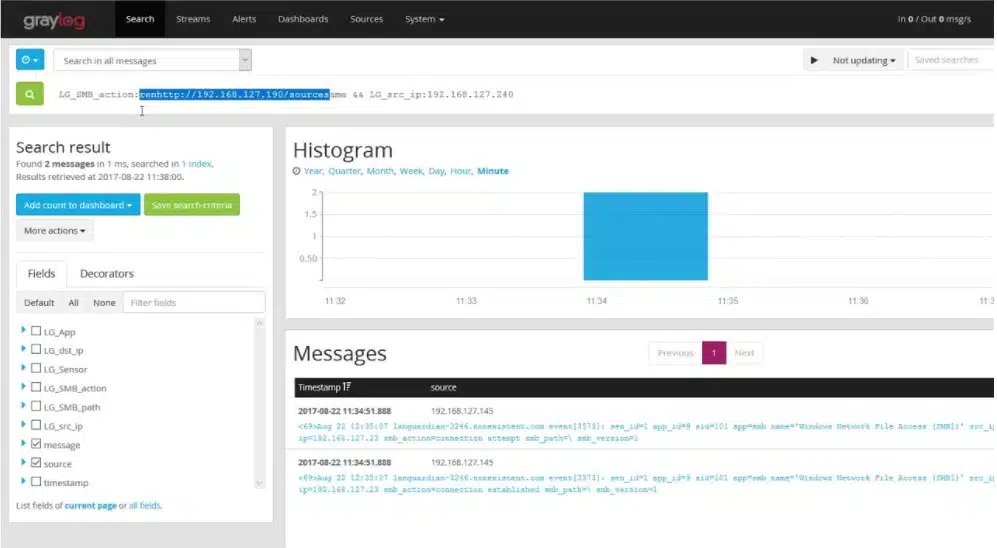
Graylog is a log management system that can be adapted for use as a SIEM tool. The package includes a data collector that picks up log messages that derive from operating systems. It is also able to catch log data from a list of applications with which the package has integrations. The two main formats that Graylog will capture are Syslog and Windows Events.
Key Features:
- Data collector
- Application integrations
- Syslog and Windows Events
- Consolidator
Why do we recommend it?
Originally a free, open-source system, Graylog has gathered a large and loyal user community through its years of operations. The more recent SIEM functions build on a solid log management tool.
The data collector passes log messages to a log server, where they are consolidated into a common format. The Graylog system calculates log throughput statistics and shows live tail records in the console as they arrive. The log server then files messages and manages a meaningful directory structure. Any of the logs can be called back into the data viewer for analysis.
The Graylog system includes pre-written templates for SIEM functions. These can be adapted and it is also possible to implement playbooks for automated responses on the detection of a threat.
Who is it recommended for?
The Free plan of Graylog is a great option for small businesses that don’t have a lot of cash to spend on security tools. Larger businesses opting for the paid SIEM system get an extra bonus of an excellent log management service.
Pros:
- Adaptable SIEM functions
- Orchestration with access rights managers and firewalls
- Ad-hoc query tool
- Report formats
Cons:
- Won’t install on Windows
There are four versions of Graylog. The original edition is called Graylog Open, which is a free, open-source package with community support. That package installs on Linux or over a VM. The two main versions are Graylog Enterprise and Graylog Cloud. The difference between these is that Graylog Cloud is a SaaS package and it includes storage space for log files. The Enterprise system runs over a VM. There is also a free version of Enterprise, called Graylog Small Business. That free plan is limited to processing 2 GB of data per day. You can get a demo of the full Graylog Cloud edition.
Graylog Small Business
Download – FREE up to 2GB/day
Operating System: Windows and Linux
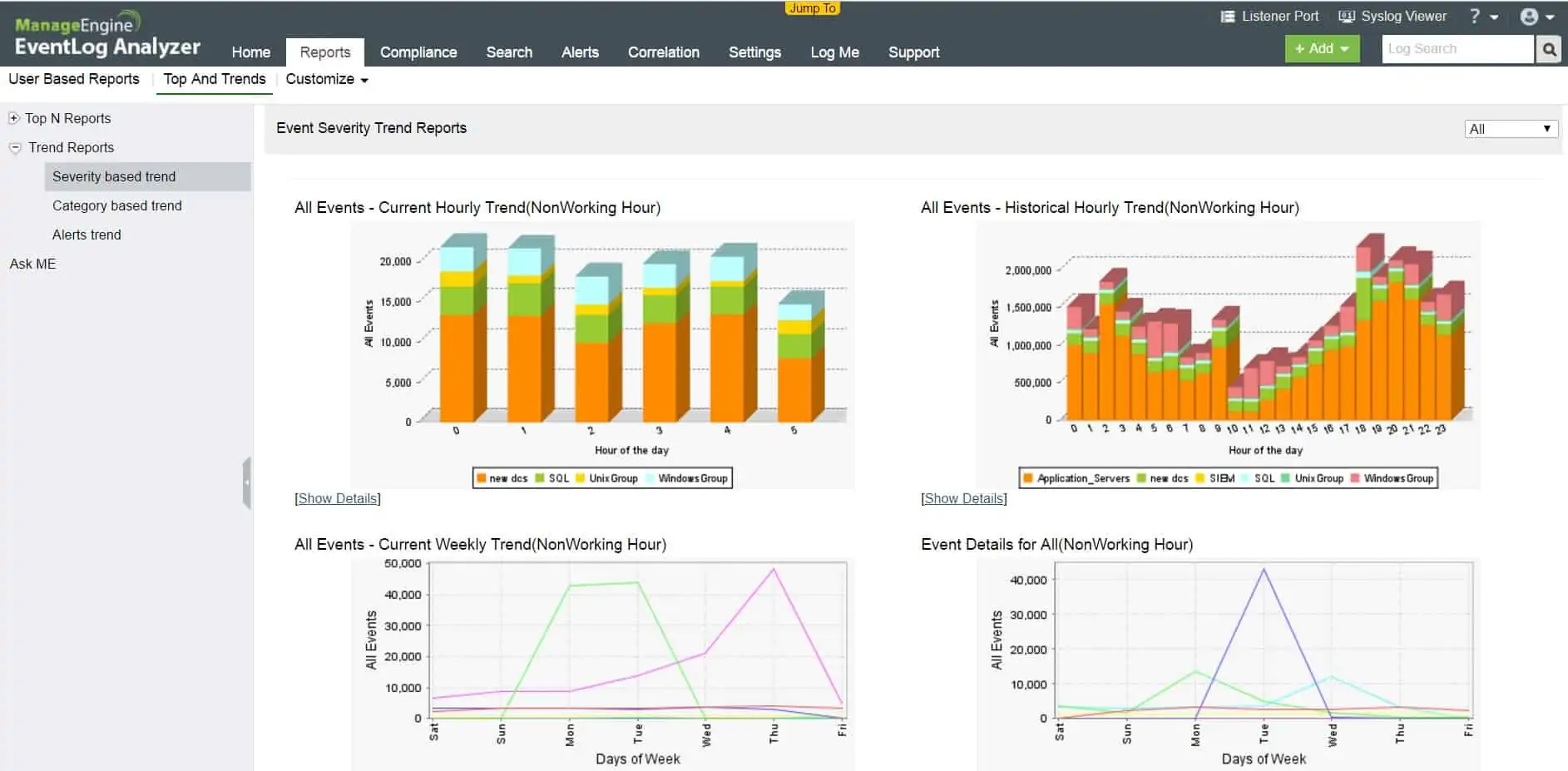
The ManageEngine EventLog Analyzer is a SIEM tool because it focuses on managing logs and gleaning security and performance information from them.
The tool is able to gather Windows Event log and Syslog messages. It will then organize these messages into files, rotating to new files where appropriate and storing those files in meaningfully-named directories for easy access. The EventLog Analyzer then protects those files from tampering.
Key Features:
- Gathers Windows Event logs and Syslog messages
- Live intrusion detection
- Log analysis
- Alert mechanism
Why do we recommend it?
EventLog Analyzer is available for Linux as well as for Windows Server, so this is a very good choice for businesses that run Windows endpoints but Linux servers because it can collect Windows Events while running on Linux.
The ManageEngine system is more than a log server, though. It has analytical functions that will inform you of unauthorized access to company resources. The tool will also assess the performance of key applications and services, such as Web servers, databases, DHCP servers, and print queues.
The auditing and reporting modules of the EventLog Analyzer are very useful for demonstrating data protection standards compliance. The reporting engine includes formats for compliance with PCI DSS, FISMA, GLBA, SOX, HIPAA, and ISO 27001.
Who is it recommended for?
The Free edition of EventLog Analyzer is a good option for small businesses. The paid version is recommended for large businesses that want to run their own log management and threat-hunting service instead of relying on SaaS packages.
Pros:
- Multi-platform, available for both Linux and Windows
- Supports compliance auditing for all major standards, HIPAA, PCI, FISMA, etc
- Intelligent alerting helps reduce false positives and makes it easy to prioritize specific events or areas of the network
- Includes a free version for testing
Cons:
- Is a very feature-dense product, new users who have never used a SIEM will need to invest time with the tool
There are four editions of ManageEngine EventLog Analyzer and the first of these is Free. That free version is limited to five log sources and has a limited set of functions. The cheapest paid package is the Workstation edition, which can collect logs from up to 100 nodes. For a larger network, you would need the Premium edition and there is a Distributed edition that will collect logs from multiple sites. All versions will run on Windows Server and Linux and you can get either of the paid editions on a 30-day free trial.
ManageEngine EventLog Analyzer
Download 30-day FREE Trial
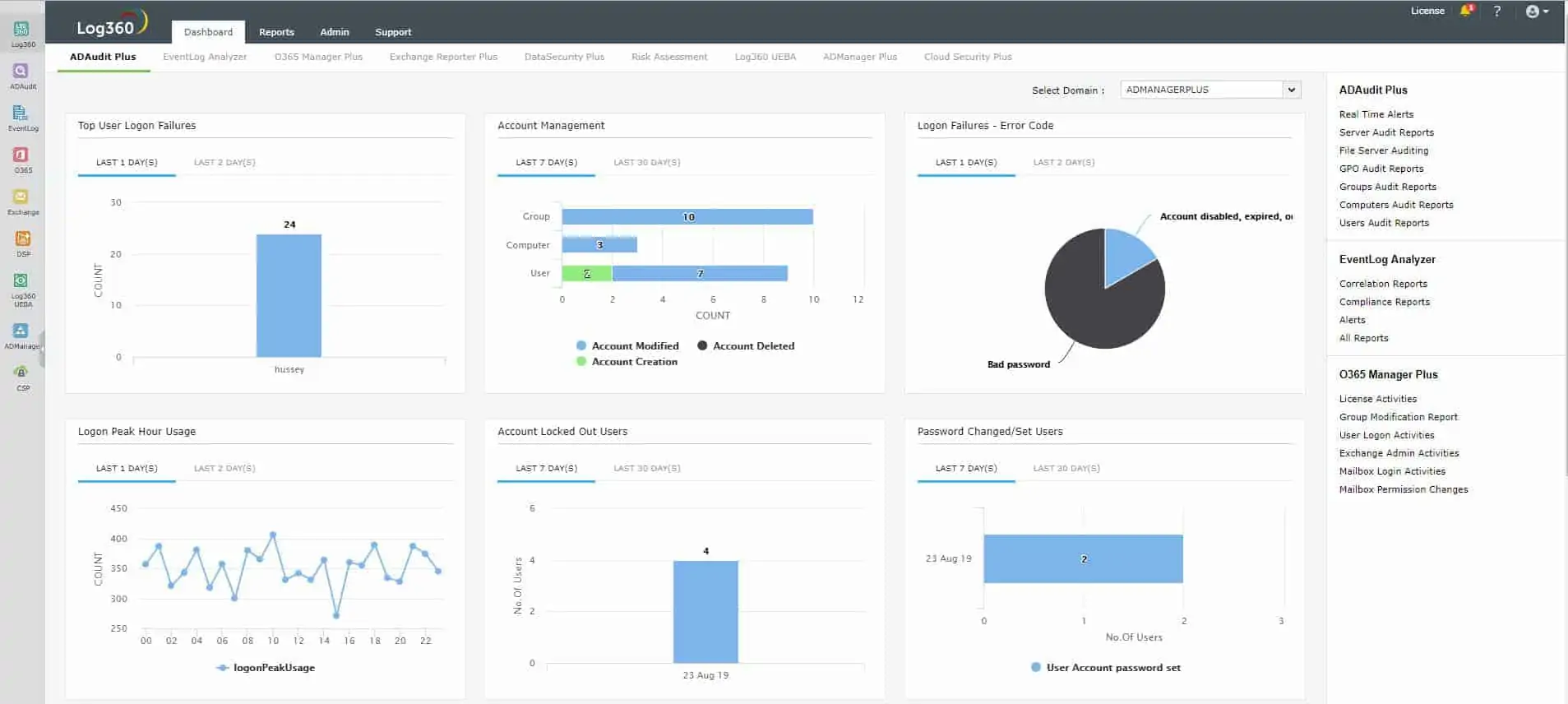
ManageEngine Log360 is an on-premises package that includes agents for different operating systems and cloud platforms. The agents collect log messages and send them to the central server unit. Agents integrate with more than 700 applications so they can extract information from them. They also process Windows Event and Syslog messages.
The log server consolidates log messages and displays them in a data viewer in the dashboard as they arrive. The tool also presents metadata about log messages, such as the arrival rate.
Key Features:
- Log collection from site and cloud systems
- Threat intelligence feed
- Alerts sent to service desk packages
Why do we recommend it?
ManageEngine Log360 is a package of ManageEngine tools, including the EventLog Analyzer. You get all of the log management and threat hunting in the EventLog Analyzer package plus user activity tracking, file integrity monitoring, and Active Directory controls.
This SIEM receives a threat intelligence feed, which improves the speed of threat detection. If suspicious activity is spotted, Log360 raises an alert. Alerts can be sent through service desk systems, such as ManageEngine ServiceDesk Plus, Jira, and Kayoko. The package also includes a compliance reporting module for PCI DSS, GDPR, FISMA, HIPAA, SOX, and GLBA.
Who is it recommended for?
The Log360 package is recommended for businesses that are in the market to tool up their Security Operations Centers from scratch and don’t already have any cybersecurity packages in place. This bundle gives you just about every monitoring service you need to block intruders, identify insider threats, and protect data.
Pros:
- File integrity monitoring
- Merges Windows Events and Syslog messages into a common format
- Manual data analysis tools
- Automated threat detection
- Log management and compliance reporting
Cons:
- Not available for Linux
ManageEngine Log360 runs on Windows Server and it is available for a 30-day free trial.
ManageEngine Log360
Download 30-day FREE Trial
Operating system: Cloud based
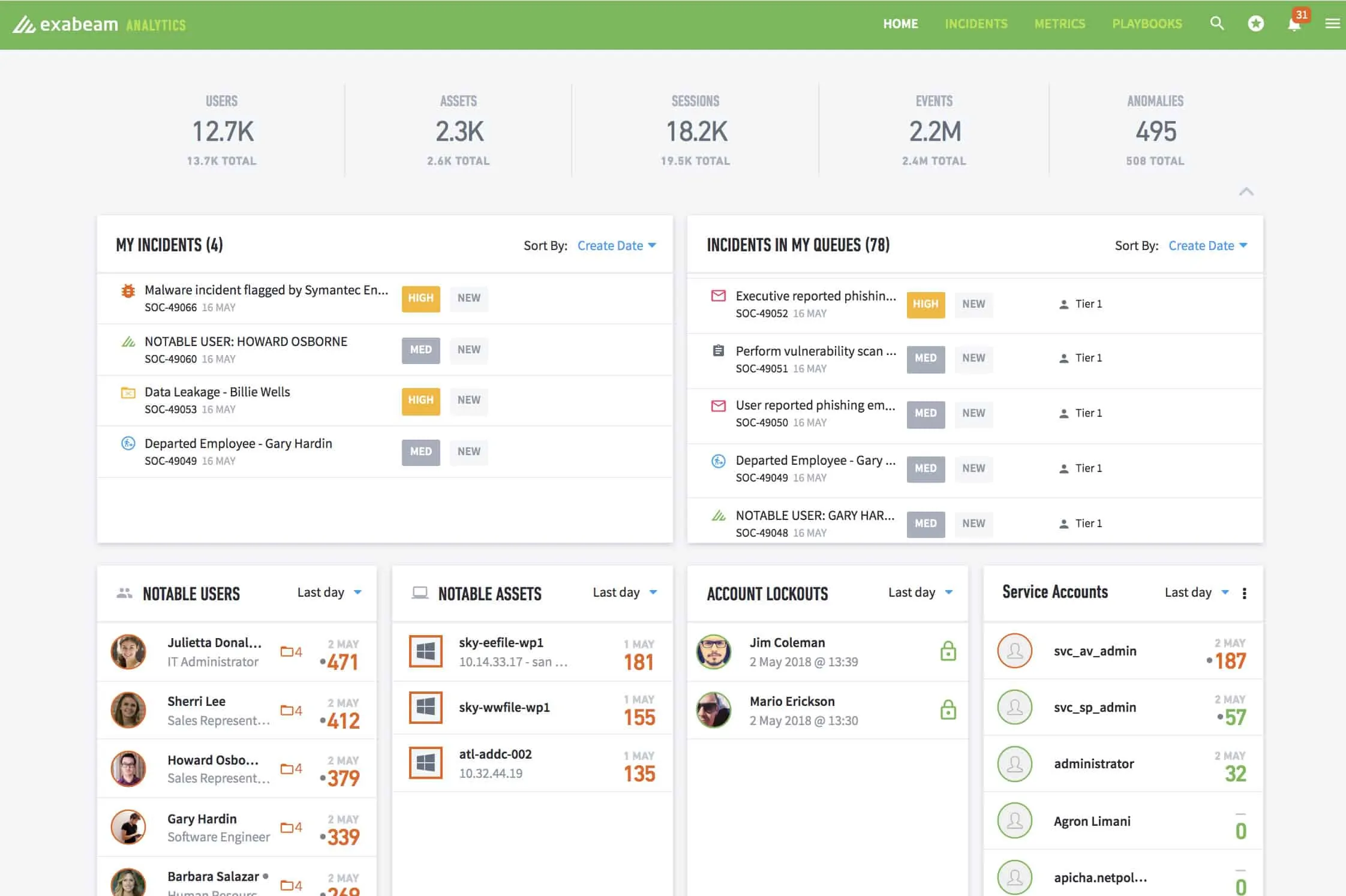
Exabeam Fusion is a subscription service. As a SaaS package, the system is hosted and includes the processing power of a cloud server and storage space for log data. The system needs source data for its threat-hunting routines and this is provided by agents that need to be installed on the networks that are to be protected by Exabeam.
Key Features:
- Adaptable baselining through UEBA
- SOAR for detection and response
- Cloud-based
Why do we recommend it?
The SOAR features in the Exabeam Fusion package enable this cloud-based system to get on-premises powers by manipulating the security measures that you already have in place, such as firewalls and access rights managers.
The on-site agents collect log messages and upload them to the Exabeam server. They also interact with on-site security packages, such as firewalls and anti-virus systems to extract more event information. This is security orchestration, automation, and response (SOAR), and the cooperation with third-party tools also works to shut down detected threats.
The Exabeam console also includes an analysis module. This enables technicians to track events and examine borderline anomalies that might be considered threats or could just be legitimate, infrequent actions. The analysis system presents a timeline of an attack, showing what chains of events lead to the decision to treat these activities as a threat.
Who is it recommended for?
Exabeam Fusion is ideal for large organizations that have multiple sites and so would benefit from the neutral cloud location of this SIEM system rather than an on-premises package.
Pros:
- A secure, off-site package that isn’t vulnerable to attack
- Automatic threat intelligence updates
- Automated responses to shut down attacks
Cons:
- No free trial
- No price list
Exabeam is an impressive security product with a list of high-profile users that includes banks, utilities, and tech firms. One problem with this system is that Exabeam doesn’t publish its price list and it doesn’t give a free trial. However, you can get a demo to explore the SIEM system.
Operating system: Windows, macOS, Linux, and cloud
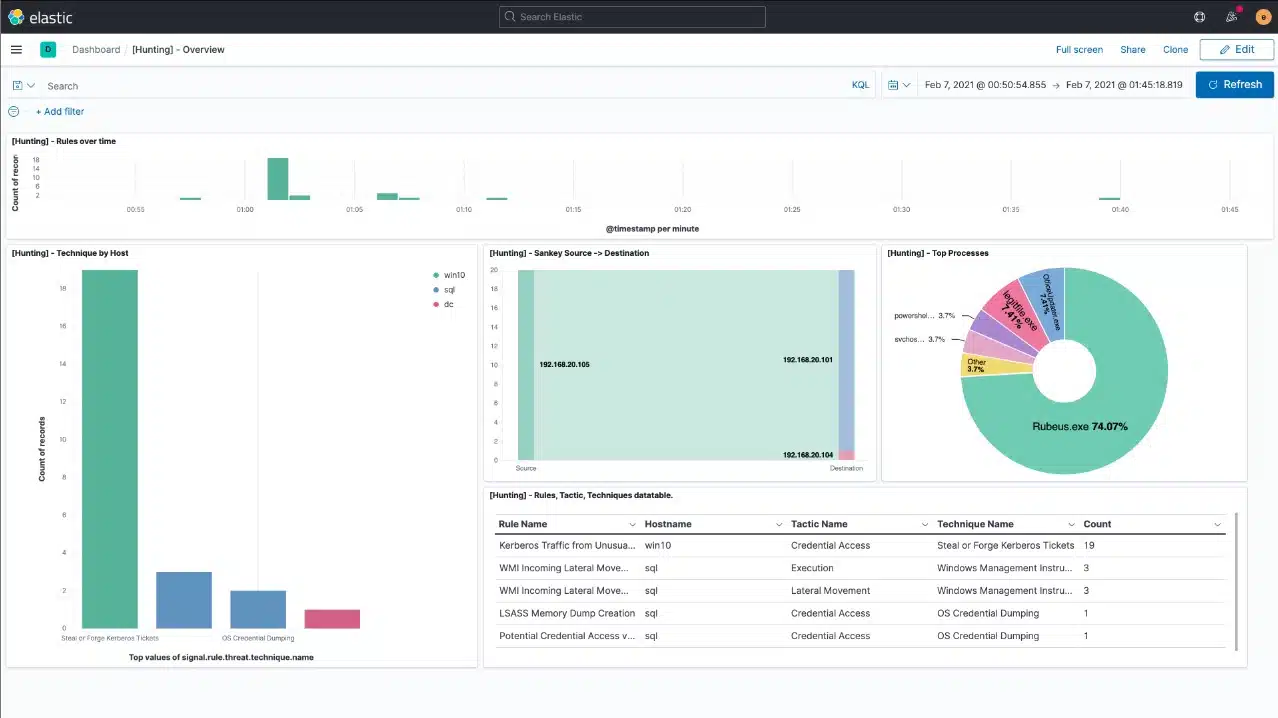
The Elastic Stack is a group of free tools that can be used to analyze any dataset. This is a very widely-used package that includes Logstash for log message collection, Elasticsearch for data assessments, and Kibana to display results. The group is also known as ELK. The problem most users will face when using ELK for security monitoring is that it takes a lot of work to set up your own search rules. However, Elastic Security is a paid package of all of the rules and settings that you need in order to make a SIEM system out of ELK.
Key Features:
- Deployment options
- Collects log messages
- Live and historical analysis
Why do we recommend it?
Although the Elastic Security package operates on your ELK installation, it doesn’t reserve the entire stack for its own use. You can still create your own data analysis tools alongside your constantly-running ELK SIEM system. This makes the Elastic Security service very good value for money.
You can adapt the Elastic Security package to take any source of data, such as application status reports as well as operating system log messages. The service isn’t limited to monitoring one site or platform, so you can channel source data into the SIEM from any site and also cloud services.
Who is it recommended for?
The ELK package by itself is a very good deal because the components are free to use on your own hosts. This makes the ELK system appealing to small businesses and those who don’t have the time or training to set up a custom-built SIEM will be happy to pay the fee for the Elastic Security add-on just to save time. This is also a good package for large businesses and the SaaS option will appeal to businesses that don’t want to run their own servers.
Pros:
- Provides log file management
- Out-of-the-box threat hunting
- Can be customized with extra data sources
Cons:
- Still requires some work to set up
Elastic Security is included in all of the paid plans for the Elastic Stack system and the price is the same whether you host the software yourself or access it on Elastic Cloud. There are five price points and all of the editions include performance monitoring as well as the security package. You can assess any of the plans on Elastic Cloud with a 14-day free trial.
Operating system: Hardware, VMware, Hyper-V, KVM, OpenStack, and AWS
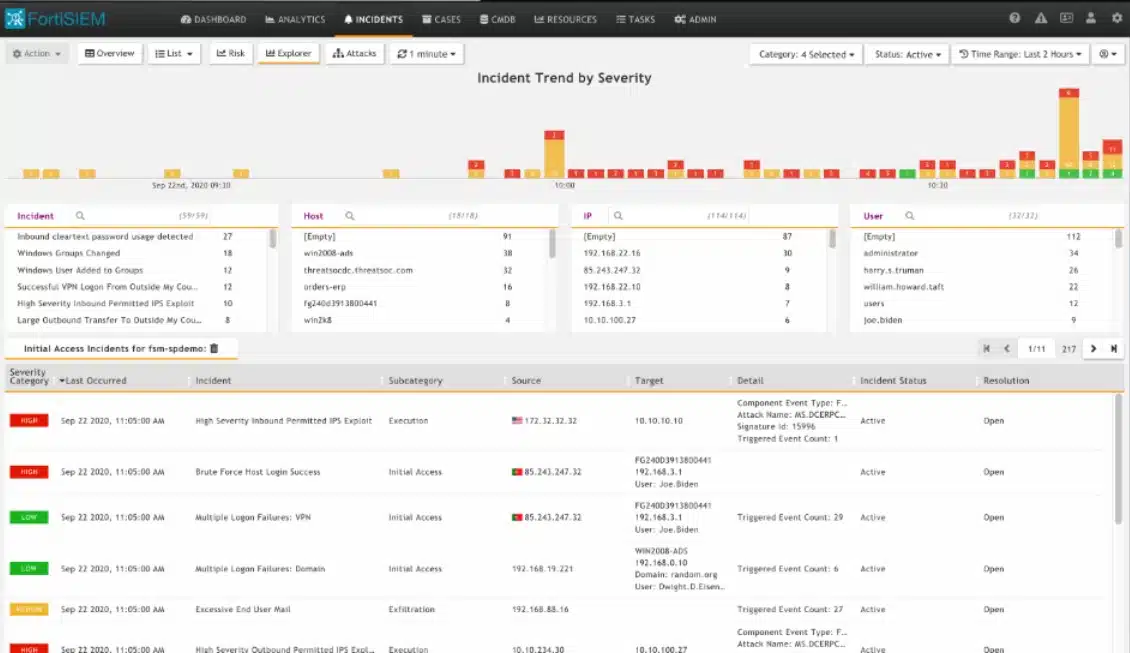
Fortinet FortiSIEM can be used as a standalone tool or combined with other Fortinet tools to create a full enterprise protection system, called the Fortinet Security Fabric. Fortinet has an excellent reputation in the field of cybersecurity and its hardware appliances are custom-built with specially designed microchips to provide high-speed data processing. The FortiSIEM can be included on a hardware device or you can run it as a virtual appliance. The system is also offered as a service on AWS.
Key Features:
- Choice of data processing volumes
- Includes attack responses
- Compliance reporting
Why do we recommend it?
Fortinet is a leading provider of system security solutions and so deserves to be included on any list of security service categories in which they have products. The inclusion of FortiSIEM as part of a SASE solution or added to the FortiGate firewall provides optimum security.
Fortinet FortiSIEM will collect and store log messages, which is an essential task for compliance with many data protection standards. FortiSIEM provides compliance reporting for PCI-DSS, HIPAA, GLBA, and SOX. Another important feature of this system is that it can be set up to implement automated responses to shut down the threats that it detects.
Who is it recommended for?
Fortinet’s reputation for the excellence of its hardware appliances sets this business as aiming for large corporations for its customer base. The advent of its virtual machine option brings down the cost of using Fortinet SIEM. However, the company still favors larger businesses with its product line.
Pros:
- Can be combined with a firewall and traffic shaping service
- Options to implement security for virtual networks
- Deploys user and entity behavior analytics (UEBA)
Cons:
- Prices are at the higher end of the market
The expansion of Fortinet’s implementation model to include virtual appliances enables the business to appeal to a wider audience than its original and still favored deployment system that is based on hardware appliances. The company offers a demo of its Fortinet SIEM and any of its other products.
Operating System: Windows and Linux
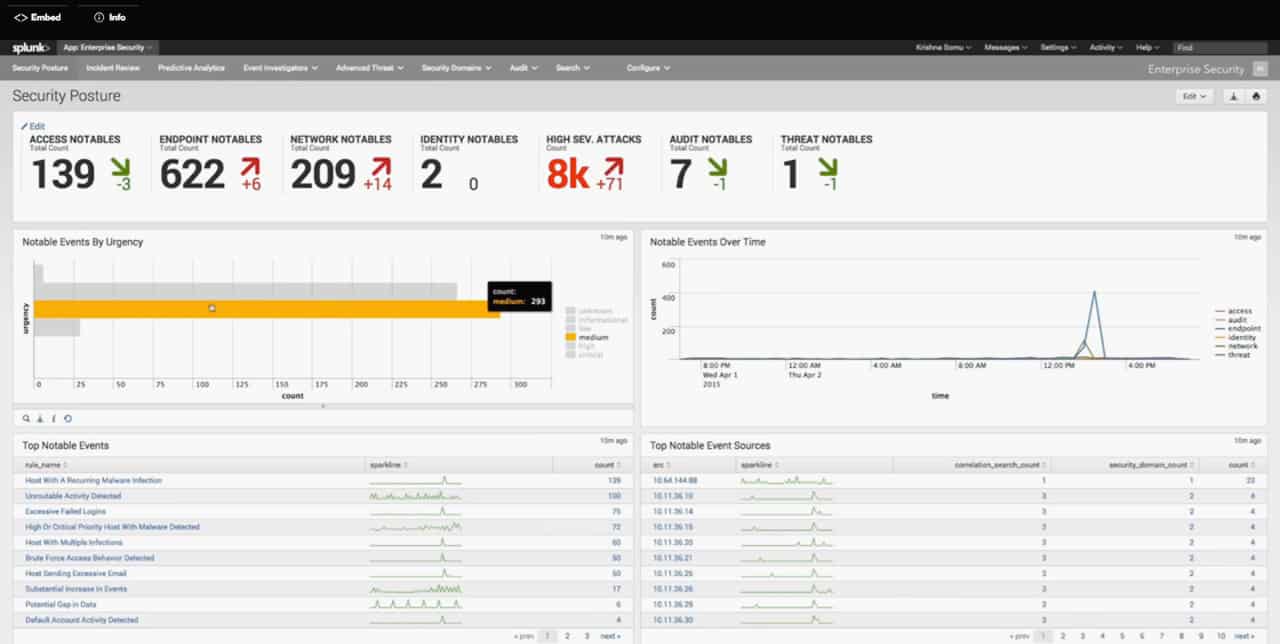
Splunk is one of the most popular SIEM management solutions in the world. What sets it apart from the competition is that it has incorporated analytics into the heart of its SIEM. Network and machine data can be monitored on a real-time basis as the system scours for potential vulnerabilities and can even point to abnormal behavior. Enterprise Security’s Notables function displays alerts that can be refined by the user.
Key Features:
- Real-time network monitoring
- Asset Investigator
- Historical analysis
Why do we recommend it?
Splunk Enterprise Security is a very flexible package and gets you the base Splunk package for data analysis as well. You can create your own threat hunting searches, analysis functions, and automated defense rules as well as using the out-of-the-box rules that are included with this plan.
In terms of responding to security threats, the user interface is incredibly simple. When conducting an incident review, the user can start with a basic overview before clicking through to in-depth annotations on the past event. Likewise, the Asset Investigator does a fine job of flagging malicious actions and preventing future damage.
Who is it recommended for?
Splunk Enterprise Security is recommended for businesses of all sizes. However, the cost and power of this package mean it is probably more attractive to large businesses than small enterprises.
Pros:
- Can utilize behavior analysis to detect threats that aren’t discovered through logs
- Excellent user interface, highly visual with easy customization options
- Easy prioritization of events
- Enterprise focused
- Available for Linux and Windows
Cons:
- Pricing is not transparent, requires quote from vendor
- More suited for large enterprises
- Uses Search Processing Language (SPL) for queries, steepening the learning curve
You need to contact the vendor for a quotation so it’s clear that this is a scalable platform designed with larger organizations in mind. There is also a SaaS version of this Splunk service available, called Splunk Security Cloud. This is available for a 15-day free trial. The trial version of the system is limited to processing 5 GB of data per day.
Operating system: Cloud-based
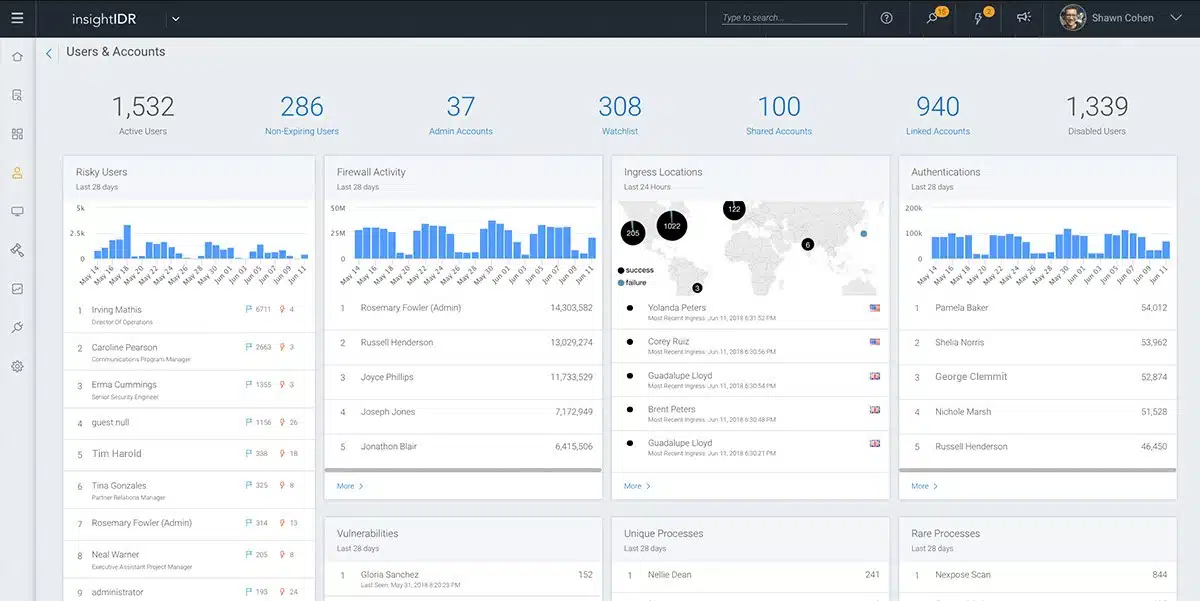
Rapid7 InsightIDR is headlined as both an XDR and a SIEM. This cloud-based system installs agents on your site to collect and upload activity data. The system is supported by a team of security analysts who supplement the insights of the detection software. The tool also gets a threat intelligence feed, which sharpens threat detection toward current attack vectors.
Key Features:
- Endpoint protection
- Network security scanning
- User and entity behavior analytics
Why do we recommend it?
InsightIDR is more of a “platform” than a “package” because it includes a collection of security systems. It provides multiple threat detection methods and also exploits the power of your existing security systems, such as firewalls and access rights managers. Threat response can be automated for immediate action.
This system combines several threat detection strategies. The threat intelligence feed provides indicators of compromise (IoCs), which are the foundations of a signature-based detection approach. The system also includes a user and entity behavior analytics (UEBA) module, which records a baseline of normal behavior for each user account and device – this is an anomaly-based detection method.
While collecting event data from each endpoint, this tool also gathers live network activity information. This combination provides the classic source data for a SIEM. The threat detection process is performed in the cloud on Rapid7 servers, thus lightening the processing burden on your servers.
Responses can be implemented through third-party tools. The InsightIDR service writes new firewall rules to block traffic from suspicious external sources and it can also instruct access rights managers to suspend accounts that seem to have been compromised.
The InsightIDR console helps system administrators create honeypots and traps to lure intruders into a dead end where they can be identified and blocked. The service is a time-saver and it creates fake data files and accounts with weak security as bait.
Who is it recommended for?
This system is complicated and comprehensive and, therefore, it is not cheap. The service is made for large organizations with extensive assets to protect. Grown mid-sized businesses would also benefit from the package. The Rapid7 platform also includes a vulnerability manager so that combination will attract businesses that are in the market for both prevention and live security systems.
Pros:
- Provides deception technology utilities
- Security orchestration, automation, and response (SOAR)
- Cloud-based threat hunting
- Automated threat response and action logging
Cons:
- Can’t protect systems that are disconnected from the internet
InsightIDR provides compliance auditing as well as threat protection. It collects and stores system log messages, retaining them live for three months and then keeping them in an archive for a further 10 months. Archived files can be revived for compliance auditing.
You can get a 30-day free trial of Rapid7 InsightIDR.
See also: The Best HIDS
Operating System: Windows, appliance, or cloud
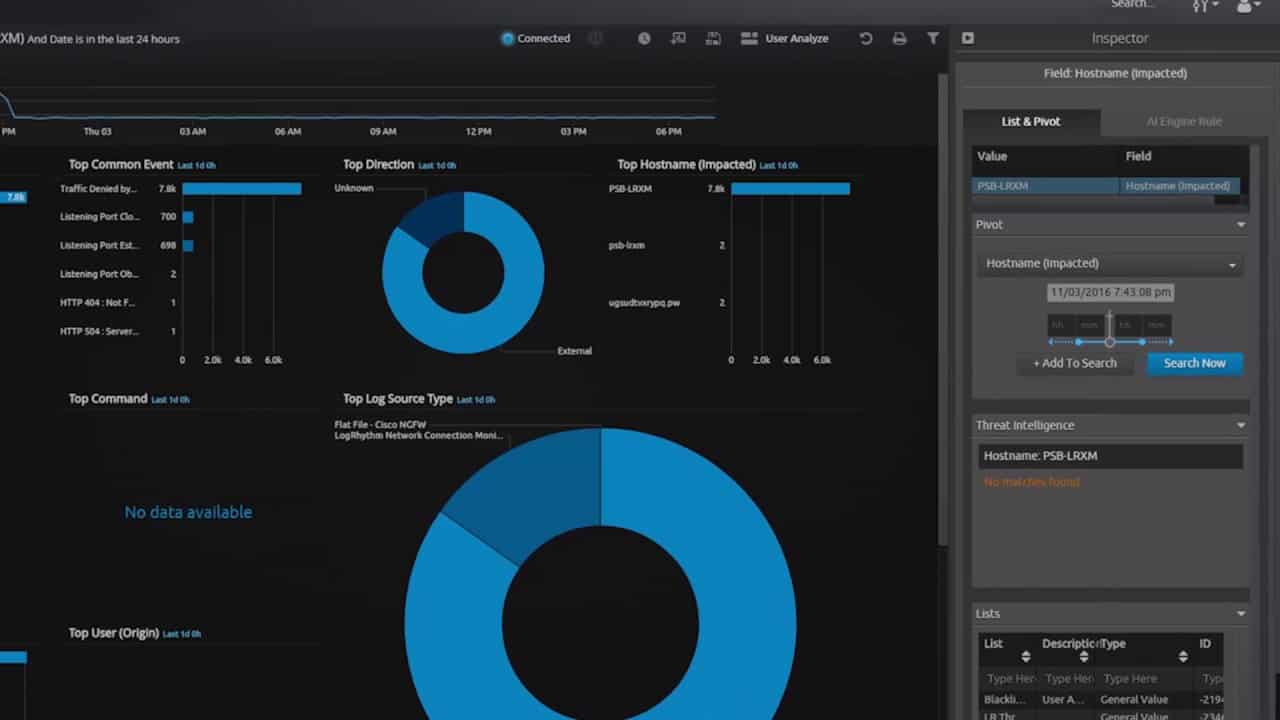
LogRhythm have long established themselves as pioneers within the SIEM solution sector. From behavioral analysis to log correlation and artificial intelligence for machine learning, this platform has it all.
Key Features:
- AI-based
- Log file management
- Guided analysis
Why do we recommend it?
LogRhythm NextGen SIEM is a cloud-based service and it is very similar to Datadog, Logpoint, Exabeam, AlienVault, and QRadar. This tool is equally proficient to its rivals and so we couldn’t leave it out of our list of recommendations.
The system is compatible with a massive range of devices and log types. In terms of configuring your settings, most activity is managed through the Deployment Manager. For example, you can use the Windows Host Wizard to sift through Windows logs.
This makes it much easier to narrow down on what is happening on your network. At first, the user interface does have a learning curve, but the extensive instruction manual helps. The icing on the cake is that the instruction manual actually provides hyperlinks to various features in order to aid you in your journey.
Who is it recommended for?
As it is a cloud-based system, LogRhythm is a good option for businesses that don’t want to load more systems onto their servers. This tool is a good option for large businesses that want to move their systems to the cloud.
Pros:
- Uses simple wizards to setup log collection and other security tasks, making it a more beginner-friendly tool
- Sleek interface, highly customizable, and visually appealing
- Leverages artificial intelligence and machine learning for behavior analysis
Cons:
- Would like to see a trial option
- Cross-platform support would be a welcomed feature
The price tag of this platform makes it a good choice for medium-sized organizations looking to implement new security measures.
Operating System: Cloud-based
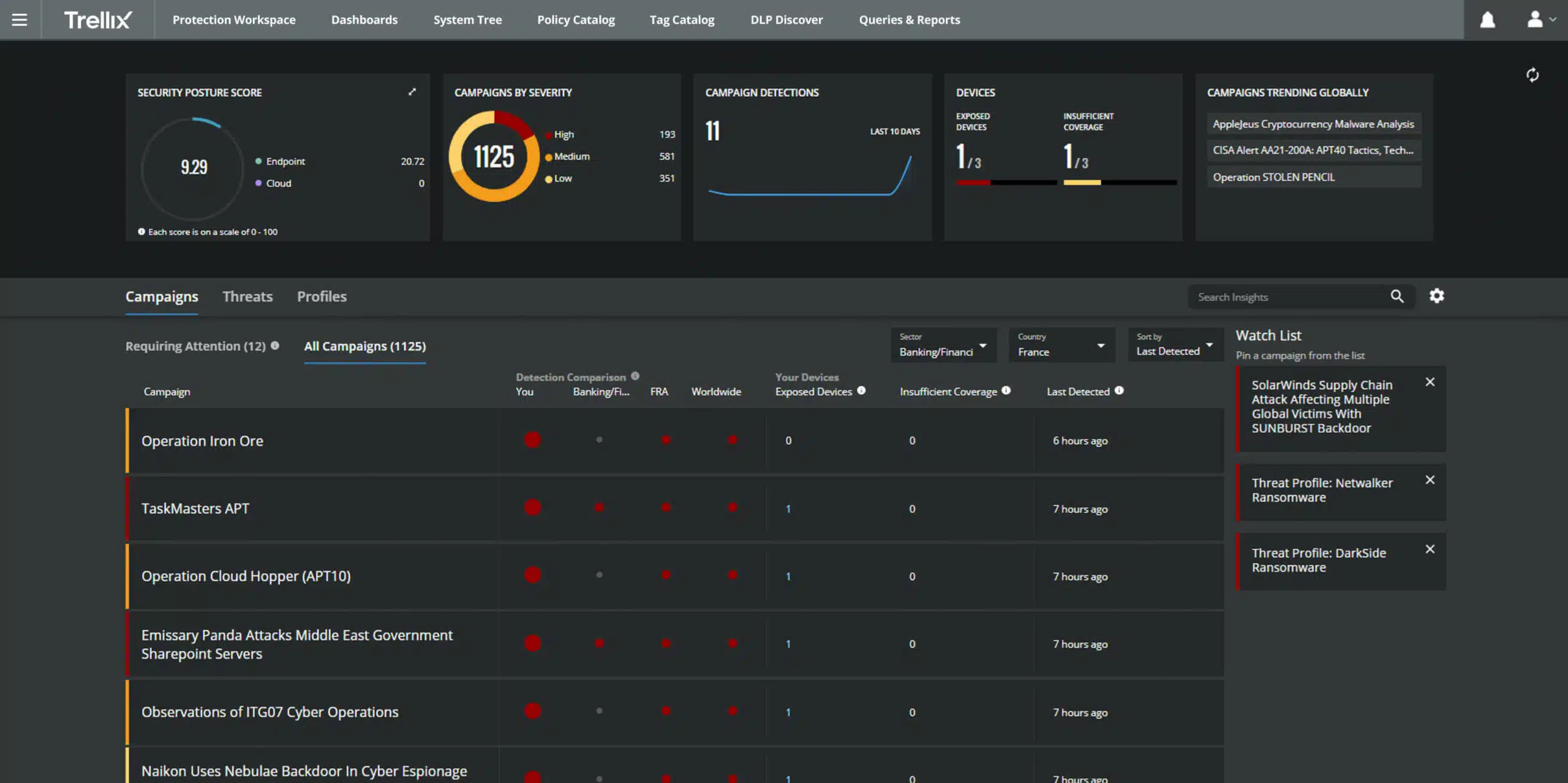
Trellix Helix is a SIEM service that is delivered from the cloud. The tool installs an agent on the network that is to be monitored and this collects data from endpoints and network devices. This system includes a number of extra features that qualify it for the status of next-generation SIEM.
Key Features:
- Cloud-based threat hunting
- Intelligence feed
- Integrates with third-party security systems
Why do we recommend it?
Trellix Helix is a competent cloud-based next-generation SIEM. This tool provides heavy processing power without the need for the buyer to invest in a host for the software. You get extra value out of your existing security tools because this SIEM extracts data from them and sends back threat remediation instructions.
Trellix is a new brand. However, the Helix system is older – it was originally developed by FireEye. The system generates user and entity behavior analytics (UEBA) to profile each device and user. It establishes a standard activity pattern for each identity and then implements anomaly-based security analysis. That is, any deviation from standard behavior is flagged as suspicious. The strategy is ideal for identifying insider threats and account takeovers.
The package also has a threat intelligence feed, which guides the threat detection system in its search through uploaded log messages and network activity records. The tool uses integrations to extract data from on-premises security tools.
Who is it recommended for?
This tool is a close competition to Rapid7 and LogRhythm. The three tools are almost identical and it is very difficult to choose between them. This system is suitable for large organizations or growing mid-sized enterprises. The service’s SOAR unit relies on the presence of other security tools on the protected site.
Pros:
- Provides value for money through security orchestration, automation, and response (SOAR)
- Adapts threat hunting according to current hacker attack campaigns
- Designed by a reliable security tools provider
Cons:
- Can’t operate if an attacker blocks the site’s internet connection
Tellix doesn’t offer a free trial of the Helix system, however, you can schedule a demo.
Operating System: Cloud-based
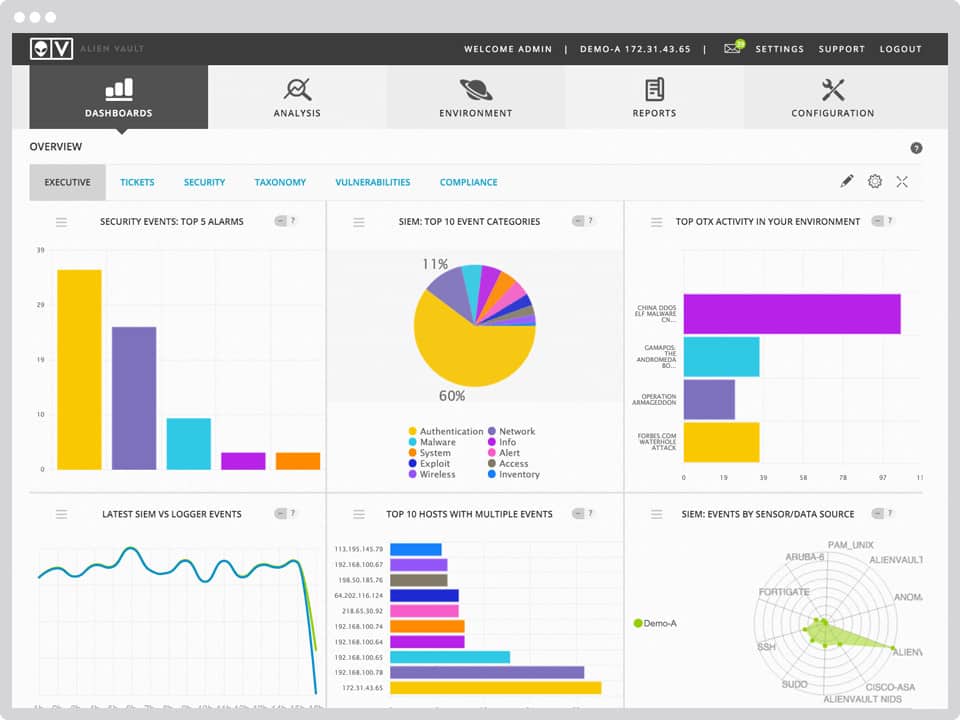
As one of the more competitively priced SIEM solutions on this list, AlienVault (now part of AT&T Cybersecurity) is a very attractive offering. At its core, this is a traditional SIEM product with built-in intrusion detection, behavioral monitoring, and vulnerability assessment. AlienVault has the onboard analytics you would expect from scalable platform.
Key Features:
- Intrusion detection
- Behavior monitoring
- Open Threat Exchange
Why do we recommend it?
AlienVault is a very reliable cloud-based SIEM system and its reasonable price makes it a great option. The crowd-sourced Open Threat Exchange is another facility in the alien Vault platform that makes this threat detection system attractive.
One of the more unique aspects of AlienVault’s platform is the Open Threat Exchange (OTX). The OTX is a web portal that allows users to upload “indicators of compromise” (IOC) to help other users flag threats. This is a great resource in terms of general knowledge and threats.
Who is it recommended for?
Businesses of all sizes would benefit from using AlienVault. Enterprises that don’t want to hire cybersecurity experts should consider the Alien Labs Managed Threat Detection and Response service.
Pros:
- Can scan log files as well as provide vulnerability assessment reports based on device and applications scanned on the network
- User powered portal allows customers to share their threat data to improve the system
- Uses artificial intelligence to aid administrators in hunting down threats
Cons:
- Would like to see a longer trial period
- Logs can be harder to search and read
- Would like to see more integration options into other security systems
The low price of this SIEM system makes it ideal for small to midsize businesses looking to upscale their security infrastructure. AT&T Cybersecurity offer a free trial.
Operating System: Linux, virtual appliance, and Cloud-based
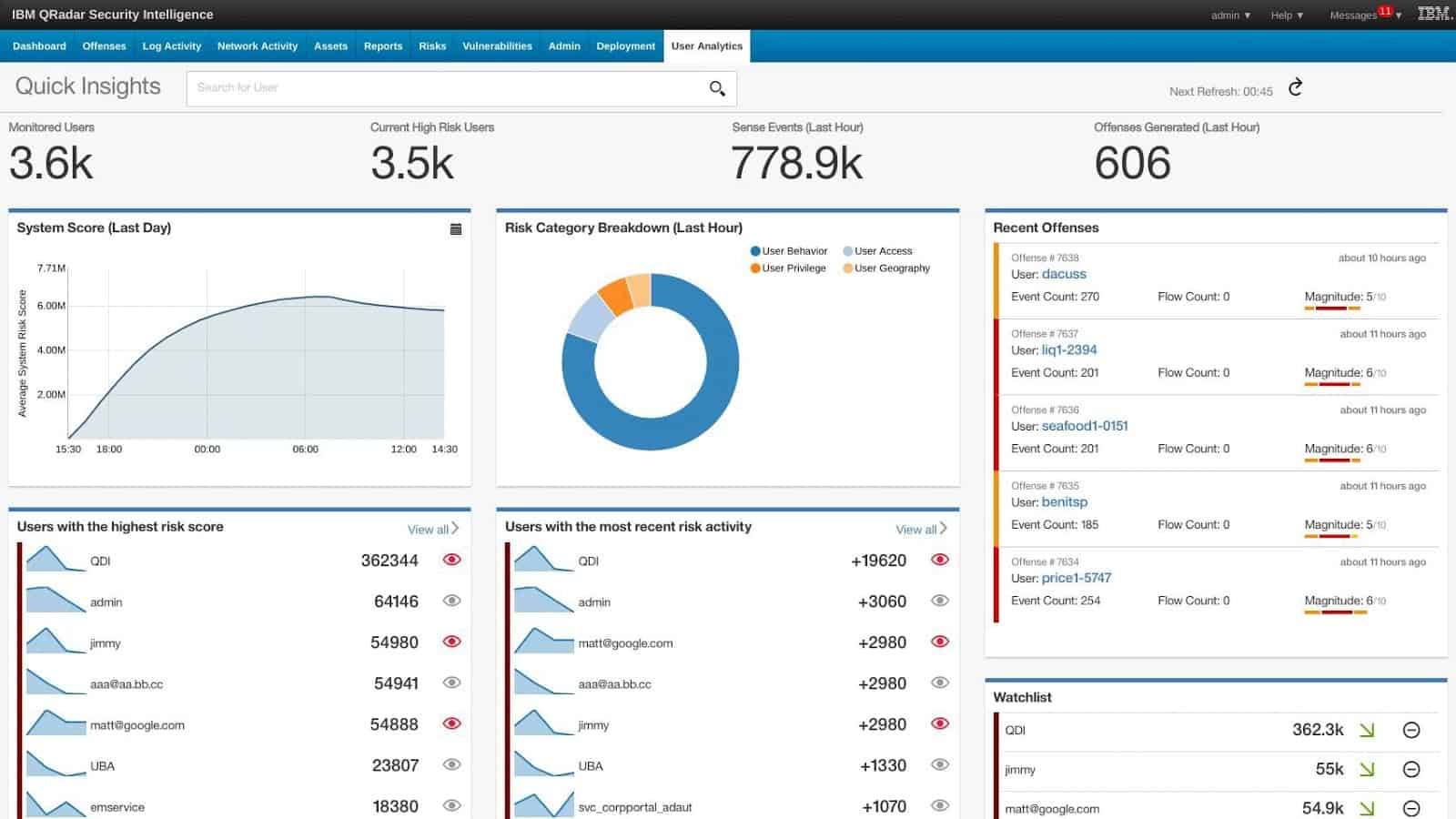
Over the past few years or so, IBM’s answer to SIEM has established itself as one of the best products on the market. The platform offers a suite of log management, analytics, data collection, and intrusion detection features to help keep your critical systems up and running. All log management goes through one tool: QRadar Log Manager. When it comes to analytics, QRadar is a near-complete solution.
Key Features:
- Log management
- Intrusion detection
- Analytical functions
Why do we recommend it?
IBM QRadar SIEM includes a very good log management service – but so do most of the other products on this list. What makes us recommend this SIEM is its analytics tools, specifically, its attack simulation module.
The system has risk modeling analytics that can simulate potential attacks. This can be used to monitor a variety of physical and virtual environments on your network. IBM QRadar is one of the most complete offerings on this list and is a great choice if you’re looking for a versatile SIEM solution.
Who is it recommended for?
The minimum price for this service applies for up to 100 workstations and 10 servers, so if you have a small company with less than those numbers of devices then you wouldn’t be getting the best value out of this tool. Bog companies will love this service and there are options to get the software package for self-hosting or get it as a SaaS deal.
Pros:
- Uses artificial intelligence to provide risk assessments
- Can judge the impact on a network based on simulated attacks
- Has a simple but effective interface
Cons:
- Lacks integrations into other SOAR and SIEM platforms
- Could use better flow analysis tools
This industry-standard SIEM system’s diverse functionality has made it the industry standard for many larger organizations.
The software for QRadar can be installed on Red Hat Enterprise Linux or it can be run as a virtual appliance over VMWare, Hyper-V, or KVM virtualizations. The system is also available as a cloud platform. IBM has created a free Community Edition of QRadar, which also functions as a trial version of the system.
Implementing SIEM
No matter what SIEM tool you choose to incorporate into your business, it’s important to adopt a SIEM solution slowly. There is no fast track way to implement a SIEM system. The best method to integrate a SIEM platform into your IT environment is to bring it in gradually. This means adopting any solution on a piece-by-piece basis. You should aim to have both real-time monitoring and log analysis functions.
Doing so gives you the ability to take stock of your IT environment and to fine-tune the adoption process. Implementing a SIEM system gradually will help you detect whether you’re leaving yourself open to malicious attacks. The most important thing is to make sure that you have a clear view of the goals you’re looking to fulfill when using a SIEM system.
Throughout this guide, you’ll have seen a variety of different SIEM providers offering vastly different end products. If you want to find the service that’s right for you, take the time to research the options available and find one that aligns with your organizational objectives. In the initial stages, you’ll want to prepare for the worst-case scenario.
Preparing for the worst-case scenario means you’re equipped to address even the harshest attacks. Ultimately, it’s better to be overprotected against cyber attacks than to be under-protected. Once you’ve chosen a tool you want to use, commit to updating. A SIEM system is only as good as its updates. If you fail to keep your logs updated and refine your notifications, you’re going to be unprepared when an emerging threat strikes.
If your organization is not ready to take on the challenges of deploying a SIEM tool, or if your budget strictly prohibits it, you can outsource your SIEM needs to a co-managed SIEM or a managed SIEM provider. Check out our post on the best managed SIEM solutions.
More SIEM Reviews & Alternatives
SIEM FAQ
What is the SIEM process?
The “SIEM process” refers to a company’s strategy towards data security. SIEM tools are an important element in that strategy, but the way in which the tools are integrated into working practices are dictated by data security standards compliance requirements.
What is SIEM as a Service?
Cloud-based software includes the server that runs the software and also storage space for log data and is called “Software as a Service” (SaaS). SIEM as a Service (SIEMaaS) is a SIEM form of SaaS and higher plans will include the provision of expert data analysts as well as the IT resources.
What is a security event?
A security event is an unexpected use of a system resource that indicates the unauthorized use of data or infrastructure. The individual event might seem harmless but could contribute to a security breach when combined with other actions.
What is log parsing in SIEM?
Log parsing restructures existing data for use in security analysis in SIEM. Key data will be extracted from regular log files that are sourced from different record-keeping systems, unifying the event information that arises from several sources.
How much does SIEM cost?
SIEM systems come in many configurations and range from open-source implementations for starting or medium businesses right through to multi-user license packages more suitable for larger enterprises.











