8 Best Data Protection Software for 2023 (Paid & Free)

Data protection software covers a wide range of services. Within this category, you will find data management systems, sensitive data protection tools, data loss prevention services, vulnerability scanners, and threat detection. The ideal data protection package will include all or most of these elements.
The information that your company needs as source material falls into several categories. You have reference data, transactional data, and research data. The transactions and research that your company performs are based on reference data. Within the reference data category, you have information about your customers, suppliers, employees, and associates.
Here is our list of the eight best data protection software packages:
- Files.com
EDITOR’S CHOICE
A secure file transfer and storage system that supports the implementation of a centralized data control strategy and allows users to decide on the permission levels that others get when accessing files. This service removes the need to mail out many copies of a file, thus retaining control. Try it with a 7-day free trial.
- ManageEngine RecoveryManager Plus
(FREE TRIAL)
This package provides backup services for Active Directory, Azure AD, Microsoft 365, Exchange Server, SharePoint, OneDrive, and Google Workspace. Runs on Windows Server. Get a 30-day free trial.
- N-able Cove Data Protection A data security system that prepares for unexpected data loss by managing backups of all data to provided cloud storage space. This is a cloud-based service.
- ManageEngine DataSecurity Plus A bundle of services that categorizes data by sensitivity, identifies vulnerabilities and protects files from tampering. Available for Windows Server.
- ThreatLocker This package of system security services lets you fence resources and restrict access to files, applications, entire servers, and USB storage devices. This is a SaaS package.
- Trellix Helix A cloud-based threat management system that includes log file monitoring and protection.
- Acronis Cyber Protect A package that includes backups, vulnerability scanning, and data loss prevention. Runs as a virtual appliance.
- Azure Information Protection This service from the well-known cloud platform tracks your sensitive data no matter where it is – it doesn’t have to be on an Azure server.
The information you hold on associated companies needs to be protected because it is probably covered by some contractual obligation. For example, a supplier may have given you a tailored price list, which they wouldn’t want their competitors or other customers to know about. Similarly, your sales team has probably stored the special deals that it has agreed to win the business of a new customer and they wouldn’t want their existing clients to know about that. Other important internal business data that needs to be protected are the salaries paid to employees and intellectual property.
The reference data in your system that pertains to individuals is covered by legislation and you could face fines if that information gets disclosed. Those individuals whose information is leaked also have the right to sue your company. Laws also govern how you use that data, which is called Personally Identifiable Information (PII), and even where you store it.
Data protection priorities
When conducting data protection, you need to consider three areas of concern:
- Data loss
- Data disclosure
- Data misuse
Ensuring that you put in place software to prevent these three types of events will give you a data protection strategy.
Mục lục bài viết
Data loss
Within the IT industry “data loss” usually means data theft. In this guide, we use the term to mean accidental or environmental events that cause data to be no longer accessible. So, a server being ruined by a burst pipe or an IT technician accidentally wiping a disk would be two examples of this. In other words, the data is lost and cannot be recovered.
It should be assumed that the only reason you hold each piece of information is that your business needs it to operate. Imagine if all of your system’s customer accounts suddenly got wiped or if you lost all of the work in progress that your company’s consultants and engineers have stored while working on client accounts.
The consequences of the actual unrecoverable loss of data would be catastrophic. While the loss of all data of a particular type would be disastrous, so would even the loss of part of the data. This type of data protection forms part of company continuity procedures and relies on backup and recovery systems.
Data disclosure
Data disclosure refers to non-authorized access to data. This might be through theft or through sharing. In the case of data sharing by authorized users, this could be accidental or intentional. Intentional data disclosure could be driven by resentment against the company, as a power play by rival employees, or as a whistleblowing act.
Protecting data from disclosure is carried out through data loss prevention systems and threat detection.
Data misuse
Data misuse is usually intentional. For example, a company might use contact information for clients of one division to launch a promotion campaign for the launch of a new division. Data is held for a purpose and must not be spread around to benefit unrelated activities. Holding incorrect data is classified as data misuse because it incorrectly labels a customer. These types of events can be prevented through data governance and data protection compliance packages.
As incorrect information is classified as misuse, unauthorized alteration to records is another form of misuse that needs to be guarded against. Changes that render stored information incorrect can be performed accidentally or intentionally by employees, by company management to cover up a misdemeanor or improve a financial or by an intruder to cover up activity or to slur a rival. This type of data misuse can be guarded against by file integrity monitoring (FIM) systems.
The best data protection software
When looking for the best data protection software, we are aiming for packages that can cover as many of the damaging events that can impact data integrity. Data protection standards, such as PCI DSS and HIPAA understand that some data disclosure events are unavoidable. However, in these cases, the standards expect that companies should spot the data disclosure, loss, or damage with speed and notify all of those affected by the event as quickly as possible. The data attacks should also be reported to the relevant authorities as quickly as possible, while remediation attempts to recover data or prevent a similar attack from happening are also expected.
What should you look for in a data protection system?
We reviewed the market for data protection software and analyzed the options based on the following criteria:
- An off-site system or virtual appliance that is systemically protected from events on the network
- A data persistence service that enables backups to be managed and changes to be rolled back
- A method to identify sensitive data and implement graded protection measures
- Integrated vulnerability and risk management
- Action logging for compliance auditing
- A demo or a free trial for a no-cost assessment
- Value for money offered by bundles that discount each function when compared to the cost of buying them individually
As well as following those guidelines, we looked for tools that would cover as many aspects of data protection as possible and specialized systems that are geared towards achieving excellence in specific aspects of data protection.
Files.com is a cloud service that operates as a secure file store and transfer manager. You can improve data protection by centralizing all file storage in one place on this cloud storage system. Uploads to the service are protected by encryption as files at rest on the server.
Key Features:
- User controls for file access
- Cloud platform
- Access by invitation
- Permission levels
- Integrates with Microsoft 365
Why do we recommend it?
Files.com protects data in motion and at rest with AES-256 encryption. That is the strongest encryption system around and it is used by the banking industry and the US military. The Files/com system is a data-sharing platform that can be used for collaboration over the creation of files through an integration with Microsoft 365. It is a secure storage space that can be used for business continuity in case of an environmental disaster on your site and it is also a good choice as a hub for distributed teams. Store files for distribution and mail out invite links for in-place access rather than by sending attachments.
Files.com gives you several data management strategies. You can institute a working practice that requires all files to be created and saved on the cloud platform. This service integrates with Microsoft 365, so by removing endpoint software, you get better control over where files are saved. Each user gets an individual account, which enables all actions on files to be tracked. There is also an administrator account for each plan, which has several file-tracking services built into it.
When all files are on the Files.com server, users can distribute or share files by sending out a link to the file on the server. Permissions can be restricted to read-only, controlling the number of copies that are issued for each file and tightening data protection.
Who is it recommended for?
The Files.com system is recommended for any size or type of business. Small businesses cut costs by removing the need to buy a files server and large businesses get unlimited, extendable storage space that is secure and can link together distributed teams.
Pros:
- Saves space by providing extra file directories
- Manages large files
- Cuts down file copying by keeping one version in one place
- Provides access to external file viewers
- Substitutes links for email attachments
Cons:
- The free trial is only seven days
You can assess Files.com on a 7-day free trial.
Files.com
Access 7-day FREE Trial
ManageEngine RecoveryManager Plus is a software package that backs up the Microsoft systems that run on Windows Server or SaaS packages provided by Microsoft, such as Microsoft 365. It can also back up Google Workspace accounts. This tool is particularly important for backing up Active Directory and Azure AD.
Key Features:
- Runs on premises
- Backs up on-site and cloud systems
- Get cloud drives backed up
- Free edition available
Why do we recommend it?
ManageEngine RecoveryManager Plus is an important purchase for any business that runs on Microsoft products. It is particularly essential for those companies that use Active Directory, either on Windows Server or on Azure, for their access rights management system. The service is also very good a backing up SaaS packages.
As well as copying over the data held on your cloud services, this system backs up settings for those cloud systems and for Active Directory in its many different forms. The service spots changes in your AD instances and copies over just those updates, which is a very efficient strategy that places minimum load on the network.
The backup and recovery system can operate while the Microsoft tools are still in use – you don’t have to kick users off to recover data This is particularly important in the case of Active Directory where a recovery could otherwise require all users to be booted off the system.
Local and cloud syncing presents a complication for backup systems because the same file can exist in several locations and copying over all instances wastes space. So, for example, if you are synching to OneDrive, you just back up the OneDrive system, which will automatically take care of local copies because the Microsoft service will update local versions once files are restored.
The movement and storage of data can present security risks. The ManageEngine system compresses data to save space and it also protects files with AES-256 encryption both at rest and in motion. This encryption cipher is impossible to crack and it is the system used by the US military and most of the world’s banking system.
The coverage of all AD types – on Windows Server, for Exchange, for SharePoint, etc., means replication and SSO systems are coordinated within the backup system. You won’t get your replication out-of-synch, so there is no worry about corruption or users getting shut out of some of their services due to uncoordinated data restoration in AD.
Who is it recommended for?
The ManageEngine system is a good choice for businesses that are all Microsoft and it also covers Google Workspace, so those companies that are heavily reliant on these cloud systems are the primary market for RecoveryManager Plus. Small businesses will be drawn to the package’s free edition because it covers all of the systems that the paid version backs up but with a few capacity restrictions.
Pros:
- Strong data protection with AES-256 encryption
- Coordination between AD instances
- Lightweight backup process and unintrusive recovery
- Compression for backups
Cons:
- Doesn’t include repository storage space
The ManageEngine gives you complete control over your backup storage strategy because that element is not included in the package – you need to arrange your own storage locations. There also isn’t any choice over which operating system the software runs on because it is only available for Windows Server. You can test the RecoveryManager Plus system with a 30-day free trial.
ManageEngine RecoveryManager Plus
Start a 30-day FREE Trial
N-able offers a range of services that support Managed Service Providers (MSPs). However, these tools can also be useful for in-house IT departments, especially those that manage multiple sites. The N-able Cove Data Protection system is based in the cloud, so it can automate the backup services of any site anywhere. Backups created by this system can be used for migration or replication as well as for restoring lost data to the same location.
Key Features:
- Cloud-based
- Designed for managed service providers
- File backup
- Secure storage space
Why do we recommend it?
N-able Cove Data Protection is a backup and recovery system that is designed for use by managed service providers (MSPs). The service is one of the tools offered on the N-able platform, which are all meant for use by MSPs. The central package on that platform is a remote monitoring and management (RMM) bundle and Cove Data Protection enables MSPs to add data protection to their regular work of system administration. Backup repositories are protected by AES-256 encryption.
Data needs to be uploaded to the N-able cloud servers for storage. However, this is not a security risk because transfers are protected with strong encryption. This involves the AES cipher with a 256-bit key, which is considered uncrackable. Data is compressed for transmission, which speeds up the storage process and also makes the restore phase quicker.
While on the N-able server, backups are also protected by 256-bit key AES encryption. N-able has data centers around the globe and will store your backups in a location closest to your site to make transfer paths shorter. Data held on the N-able servers is also mirrored on another server, so there is no risk that the backups that you save can be lost or damaged.
If your business is hit by environmental damage that renders your premises inoperable, N-able Cove Data Protection enables you to get up and running as soon as you have started up the alternative site that your business continuity plan designated. The backup system can populate your new servers with your old data, meaning that the business can continue to run with minimum disruption.
The N-able Cove Data Protection system can manage the contents of virtual servers as well as physical servers. Servers can be backed up down to the operating system – even including the OS. The service has special backup routines for Microsoft Exchange Server, Sharepoint, and MySQL. It is also possible to backup OneDrive with N-able Cove Data Protection. Updates can be versioned, creating timed archives, any one of which can be used in full or partially to restore files. This is an important function to recover from unauthorized file tampering, which might not be discovered before many backup cycles have occurred.
N-able Cove Data Protection includes all of the storage space you need to hold copies of your important data. The Backup system is automated and can cover data held on any site. The system creates efficiency by running constantly in the background, performing incremental backups and its off-site location means the processes of the Backup service won’t be impacted by any environmental damage or system hijacking that could be the cause of your data loss or tampering.
Who is it recommended for?
The audience for Cove Data Protection is MSPs and the package is more likely to appeal to existing users of the N-able RMM service. This system would also be good for large, multi-site businesses.
Pros:
- A backup and recovery service that includes cloud storage space
- Transfers and files at rest are protected by AES-256 encryption
- Also backs up SharePoint, MS Exchange Server, and SQL Server databases
- Backups can be used for migration
Cons:
- Can be used by in-house IT Operations Departments but better for MSPs
N-able Cove Data Protection can operate restore actions to bare metal servers, physical-to-virtual, or virtual-to-virtual. The N-able Cove Data Protection system can be assessed on a 30-day free trial.

ManageEngine DataSecurity Plus includes File Server Auditing, Data Leak Prevention, and Data Risk Assessment. The facilities in this bundle include sensitive data discovery, data classification, file integrity monitoring, and vulnerability scanning.
Key Features:
- Data risk assessment
- File integrity monitoring
- USB device control
Why do we recommend it?
ManageEngine DataSecurity Plus is a sensitive data management system. It provides a sensitive data discovery and classification system that regularly rescans your servers for new instances. The service also implements data movement tracking and blocking, which includes the control of peripheral devices, such as USB memory sticks.
The service tracks down all of your data stores, whether they be on one of your sites or a cloud server. The tool will categorize data, identifying PII and other sensitive data that requires extra security and tracking. The system analyzes file permissions and access rights to devices and folders, identifying weaknesses and recommending changes.
Other services in the DataSecurity Plus package include File Integrity Monitoring (FIM). This is tamper protection that tracks changes to files, noting who made those changes and when. This service can be linked to a restore system to wipe out unauthorized changes. The service will raise an alert if a protected file is changed or deleted.
The DataSecurity Plus service monitors USB slots and blocks memory sticks from attaching. It is possible to log all file movements onto USB drives and selectively block some files from being copied. Similar controls are available for email attachments.
Who is it recommended for?
One feature of the ManageEngine DataSecurity Plus package is that it is offered as four separate packages, so you can buy just one or all four. That makes the system more accessible because if you only need some of the functionality you don’t have to pay out for services that you will never use. This package is only available for installation on Windows Server.
Pros:
- Discovers incidences of PII and categorizes them
- Enables the creation of a graded security policy that allows or restricts data access
- Can block data movements outside the network
Cons:
- No cloud version
ManageEngine DataSecurity Plus is an on-premises package that installs on Windows Server. You can get it on a 30-day free trial for assessment.
ThreatLocker offers a package of security measures that a system administrator can use to assemble a range of protection strategies. It is possible to use Network Access Control to selectively permit access to file servers. Then you can fence off directories or individual files and reserve access to them.
Key Features:
- Restricts access to servers
- Allows micro-segmentation
- Provides application whitelisting
- Extensive activity logging
Why do we recommend it?
ThreatLocker implements the separation of resources into separate access rights zones. This strategy is called micro-segmentation and it can be applied to resources, such as files, or to applications. It is also possible to set activity logging on all data access events, which is needed for compliance reporting.
The main service in the ThreatLocker platform is its Allowlisting package. This automatically blocks all programs from running on a protected endpoint. With that software disabling strategy, ransomware, malware, and remote access Trojans are completely blocked, which helps preserve the confidentiality, integrity, and availability of your company’s data.
The system administrator sets up an “allow list” and the software in that list is allowed to run. Thus, your users get to use authorized software while all other programs are unable to run. Further data protection comes from the Application Fencing feature of the ThreatLocker platform. This restricts the resources that can be accessed by an approved application.
You should only use applications that have their own access rights credentials requirements. This stipulation gets around what is probably the biggest weak point in the ThreatLocker package, which is that it doesn’t include a native access rights manager. You would set up activity logging within the approved application to create data protection audit trails. This is important for compliance reporting that is needed for PCI DSS, HIPAA, and GDPR.
Storage Control is one more data protection module in the ThreatLocker platform. This blocks all USB ports on a protected computer. The system manager can unblock a port on request and that access is only allowed to a specific user. All file movements on and off the USB storage device are logged and the activation of that port can be easily revoked.
Who is it recommended for?
The ThreatLocker package is suitable for use by businesses that use cloud-based SaaS packages as well as on-site resources. This system enables you to expand the definition of your network out across the internet and create a virtual network.
Pros:
- Resource access restrictions that can be used for servers, directories, or files
- Logging of data access events for compliance reporting
- Option to feed logs through to a SIEM for security threat hunting
- Controls over USB storage devices
Cons:
- Doesn’t have a PII discovery and classification service
You don’t get PII discovery and classification with this package so you would have to already know which files or directories need special protection before building your data protection security policy. You can assess ThreatLocker by booking a demo.
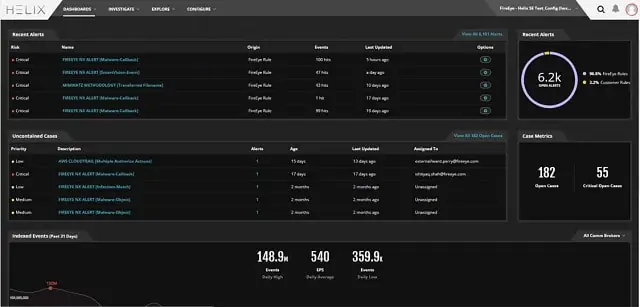
Trellix Helix is a next-generation SIEM service that includes a threat intelligence feed. This service is a good choice to protect your entire IT system and all data from theft or other malicious activity. The service doesn’t just block intruders. It includes a system called User and Entity Behavior Analytics (UEBA) that can identify unusual activities performed by authorized accounts. This anomalous behavior may indicate a hijacked account or an insider threat. Account hijacking can be identified by illogical login activity, such as an account of a user being used in a different country. The system will track the activities of those suspicious accounts, particularly concerning data access.
Key Features:
- Cloud-based SIEM
- Detects threats
- Spots anomalous behavior
Why do we recommend it?
Trellix Helix is a new name in cybersecurity but it has a very strong history in the field. This is FireEye, which has changed its name to Trellix, due to a series of splits, mergers, and takeovers. So, the company is still establishing its brand but Trelix already has a solid track record of service. You can protect your data with this SIEM system and be sure that its threat hunting is up to date, thanks to the high-quality threat intelligence feed that Trellix provides.
You can set up your Helix system to perform by a specific data protection standard. The service operates with “playbooks” which are workflows that get triggered by a particular combination of events. It is also possible to create your playbooks. The service is hosted in the cloud and the dashboard is accessed through any standard Web browser. Those dashboard screens can also be customized.
Who is it recommended for?
Helix is hosted by Trellix on its cloud platform, so anyone can use this package, regardless of operating system. Small businesses will find this package a little too much, but mid-sized and large businesses need the comprehensive threat identification offered by Trellix. This is a general data protection service and doesn’t have sensitive data discovery or compliance reporting.
Pros:
- Establishes a baseline of normal activity per device and per communicator
- Can implement automated workflows to block intrusion
- Collects and files log messages for compliance auditing
Cons:
- No price list
Integrations in the Helix package will exchange data and interact with other applications if you activate them. This makes it easier for the security system to extract activity reports from other services and also implement remediation through coordinating with other systems.
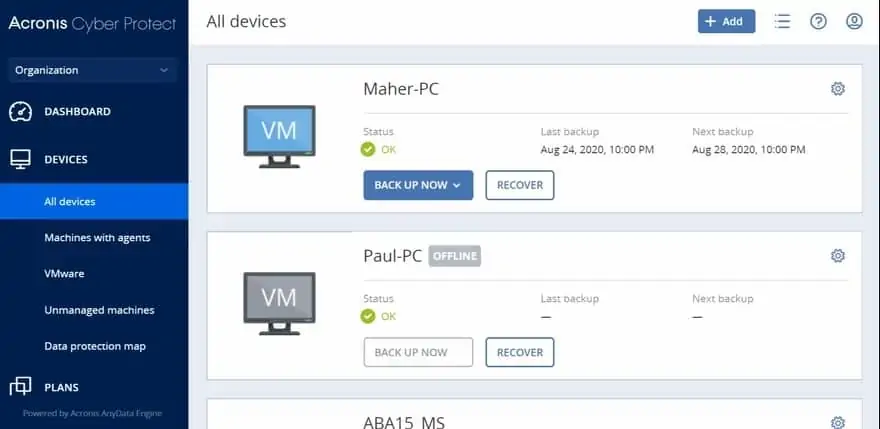
Acronis Cyber Protect is a bundle of security and data management services. It includes a backup system, a vulnerability scanner, and a threat-protection system.
Key Features:
- Backup system
- Vulnerability scanner
- Threat detection
Why do we recommend it?
Acronis Cyber Protect is a very useful combination of malware protection and backup. It will even scan each file before it is uploaded into the backup repository to prevent your backups from getting infected. Thus, this is the perfect system for ransomware protection. The antimalware will spot the ransomware before it does too much damage. However, it is likely that a few files will be encrypted before you spot the infection. However, those files can be deleted and replaced from the backup, so you will never have to pay the ransom.
The backup service can also be used to replicate servers, enabling you to set up new hardware quickly if your premises get destroyed. This can protect servers running Windows Server and Linux. The backup service will operate on virtualizations as well as physical systems.
Backups can be made to other devices on-premises or to cloud storage systems. Acronis offers a cloud storage facility but this is not included in the price of the Cyber Protect system and the two systems are not glued together, so the choice of platform is up to you.
Who is it recommended for?
All businesses need antimalware and backup systems, so getting both of these vital data protection services in one package is a great acquisition time saver. Acronis offers Cyber Protect in many editions that are suitable for different sizes of enterprises from home offices to multinational organizations.
Pros:
- A malware protection system that includes ransomware detection
- Cloud backup with pre-scans of files before upload
- Vulnerability scanning and patch management
Cons:
- You might need to buy extra cloud storage space
The controller for the system is based in the cloud and one agent on your site will manage all of the system and data protection services on the Cyber Protect bundle. Acronis offers this system on a 30-day free trial.
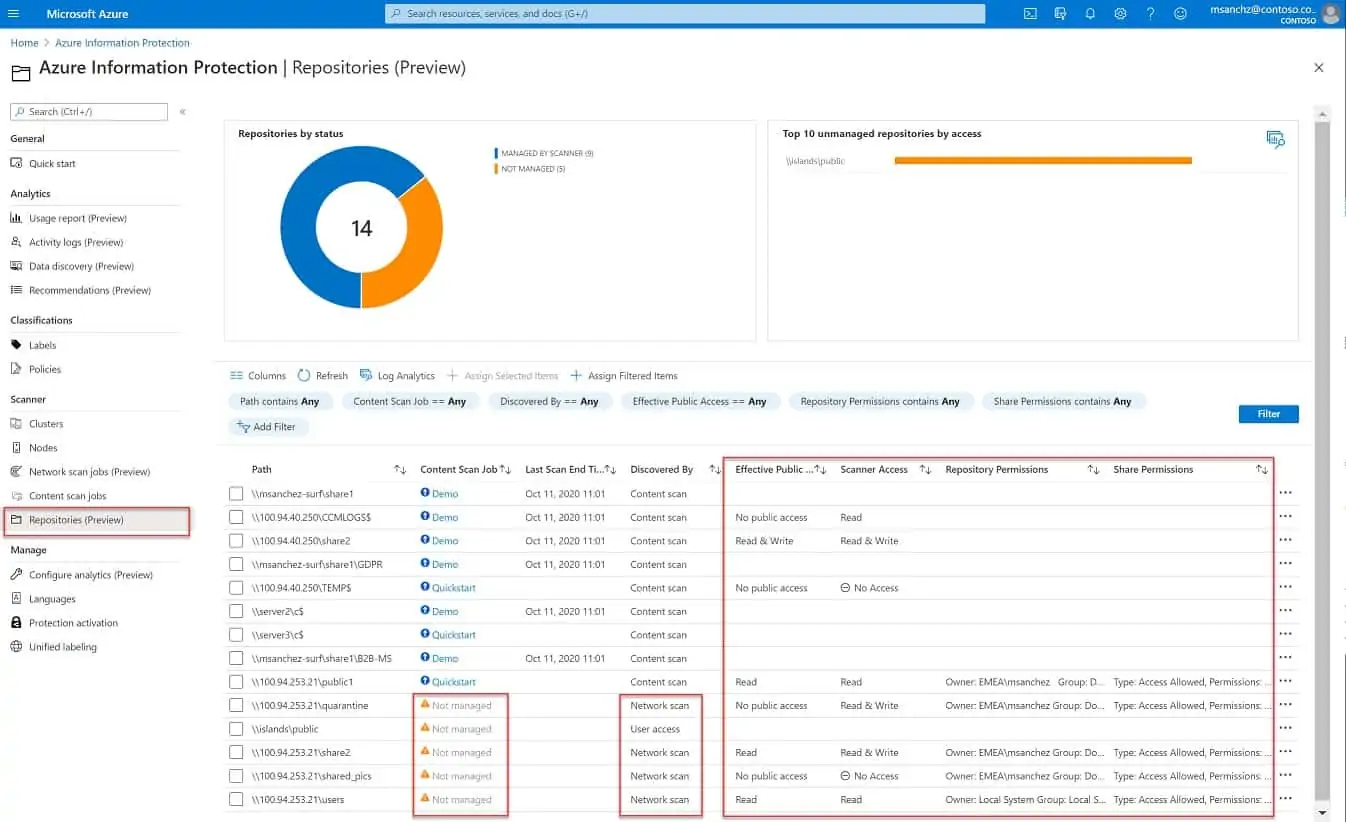
Azure Information Protection will search all of your data stores and categorize files by sensitivity. This action can be applied to any site and also to cloud servers. The cloud data management capabilities are not restricted to Azure accounts – the data can be located on any cloud platform.
Key Features:
- Hosted on Azure
- Good for hybrid systems
- GDPR, PCI DSS, and HIPAA compliance
Why do we recommend it?
Azure Information Protection is a bundle of data protection services that are delivered from the Azure platform. This is a Microsoft service, so it is well integrated into the Azure platform and is good at interacting with other Microsoft systems, such as Active Directory. However, it isn’t limited to operating on data held on the Azure system, so you can use it to protect your data anywhere – even on AWS.
The monitoring service operates continuously, catching new files as they get saved and including them in the grading and control service. The classification of data as sensitive relies on the settings you put into the system. This enables the service to tailor its protection services according to data standards, such as GDPR, PCI DSS, or HIPAA.
It is possible to block sensitive files from being copied or transferred. You can also prevent their contents from being printed and those files can also be prevented from attaching to emails.
Who is it recommended for?
Azure Information Protection has services that are suitable for many different data management scenarios. For example, it has data discovery and classification for standards compliance and can be tuned to PCI DSS, HIPAA, and GDPR. You also get copy tracking for document distribution through watermarking.
Pros:
- Identifies and classifies sensitive data
- Creates graded access rights with transfer blocking for highly sensitive files
- Will link to Active Directory
Cons:
- Doesn’t work as well if you don’t use Active Directory
The Azure Information Protection service includes an encryption service to protect files on your server and in transit. You can link the Azure Information Protect service to your Active Directory implementation for access rights management.











