Best SIEM Tools | Security Information & Event Management
1
ManageEngine Log360


Visit website
Log360 is a SIEM solution that helps combat threats on premises, in the cloud, or in a hybrid environment. It also helps organizations adhere to several compliance mandates. You can customize the solution to cater to your unique use cases.
It offers real-time log collection, analysis, correlation, alerting and archiving abilities. You can monitor activities that occur in your Active Directory, network devices, employee workstations, file servers, Microsoft 365 and more. Try free for 30 days!
Learn more about ManageEngine Log360
2
Graylog


Visit website
Graylog is a log management and SIEM that is easier, faster, more affordable than most solutions. It is a scalable, flexible cybersecurity platform that combines SIEM, security analytics, industry-leading anomaly detection capabilities with machine learning that adapts to your environment and grows with your business. Built by practitioners for practitioners, Graylog Security flips the traditional SIEM application on its head by stripping out the complexity, alert noise, and high costs.
Learn more about Graylog
Mục lục bài viết
Comparison of the Top SIEM Tools & Software
Top Tier
These vendors stand above the rest in the mature cybersecurity space.
CompanyProductEstHQExabeamExabeam Fusion2013Foster City, CAIBMSecurity QRadar SIEM1911Armonk, NYLogRhythmLogRhythm SIEM Platform2003Boulder, COSecuronixNext-Gen SIEM2008Addison, TXSplunkSplunk Enterprise Security2003San Francisco, CA

Exabeam Fusion
Exabeam Fusion is the company’s threat detection, investigation, and response (TDIR) solution bringing together automated, next-generation SIEM and XDR capabilities. Beyond centralized log management, Exabeam Fusion includes a stack of security features to aid in an era of advanced threats. Companies can connect existing security tools with an extensive integration ecosystem or replace and condense security functions via Fusion’s capabilities.
Exabeam Fusion Features
- User and entity behavior analytics (UEBA) for insider and zero-day threats.
- Full indexing for log ingestion and advanced search capabilities.
- Smart timelines gather and present evidence for incident timelines.
- Access to hundreds of playbooks and dashboards for compliance reporting.
- Integration options for over 500 security and IT tools in TDIR space.
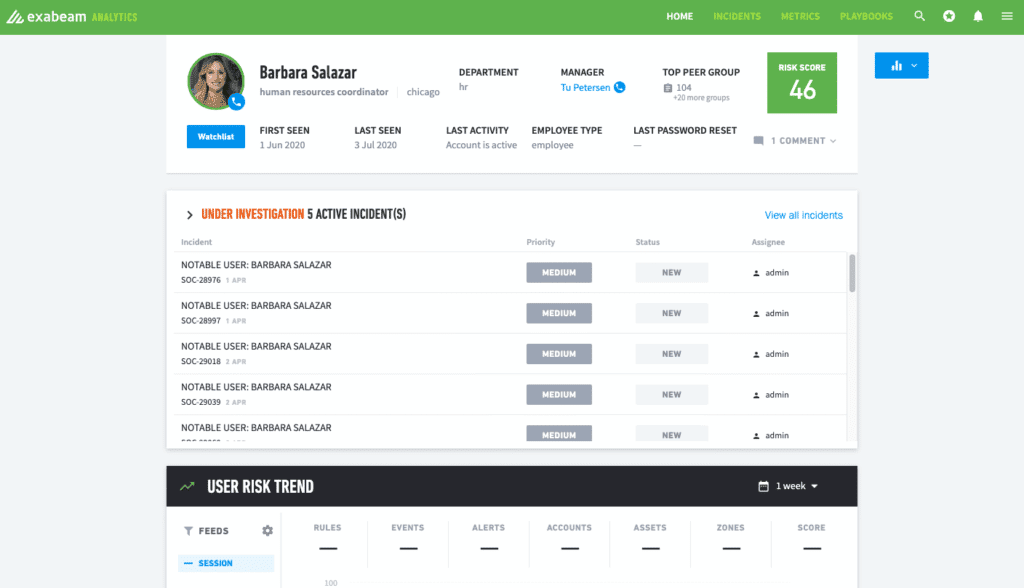 A screenshot of a network user’s profile and active incidents under investigation on Exabeam.
A screenshot of a network user’s profile and active incidents under investigation on Exabeam.
IBM Security QRadar SIEM
The IBM Security QRadar Security Information and Event Management is an enterprise favorite that’s adapted with the evolution of the SIEM market. IBM’s solution utilizes artificial intelligence (AI) to accelerate the detection of threats alongside user behavior analytics (UBA) and network flow insights. Following rigorous frameworks for compliance and reporting, QRadar SIEM is one of the safest bets for enterprise companies.
IBM Security QRadar SIEM Features
- Continuous monitoring of on-premise and cloud environments throughout the kill chain.
- IBM’s Security X-Force and STIX/TAXII feed to inform threat intelligence.
- Compliance resources for HIPAA, SOX, ISO, PCI, NIST, GLBA, GDPR, and CCPA.
- Deploy as a hardware appliance, software, or VM for on-prem and IaaS environments.
- Access to 450 integrations, APIs, and a software development kit (SDK) for more.
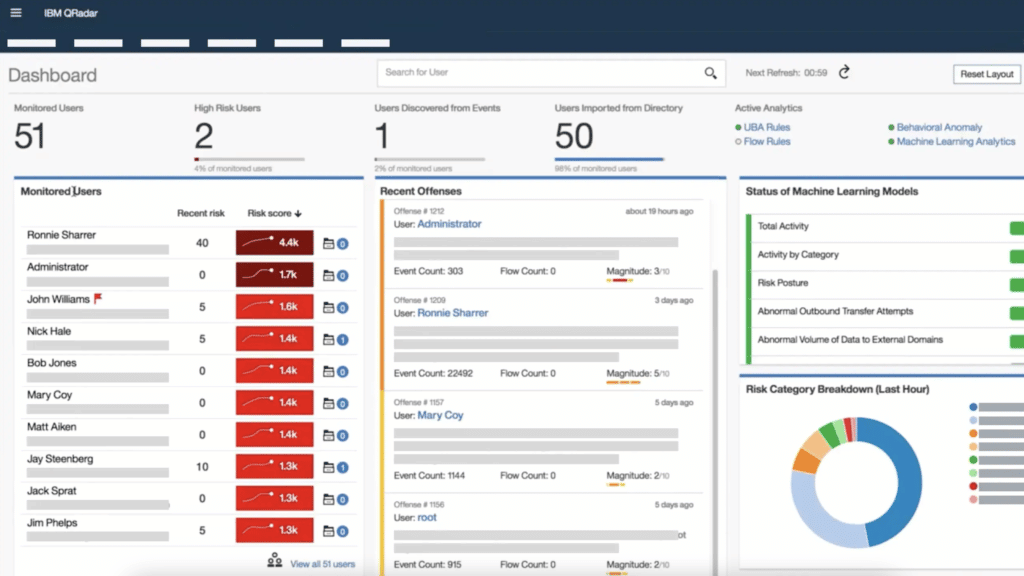 A screenshot of the IBM Security QRadar dashboard showing monitoring data for network users.
A screenshot of the IBM Security QRadar dashboard showing monitoring data for network users.
LogRhythm SIEM Platform
The eponymous LogRhythm is an undisputed industry leader in the SIEM space with a cybersecurity solution portfolio that extends to security, orchestration, automation and response (SOAR), UEBA, and network detection and response (NDR). The vendor’s flagship product, the LogRhythm SIEM Platform, is available as a hardware appliance, software, cloud, or hybrid solution with scalability for enterprise organizations. As full-featured as any SIEM solution, LogRhythm is a favorite among customers.
LogRhythm SIEM Platform Features
- Advanced analytics to detect malicious activity via compliance and security contexts.
- Prebuilt playbooks, including alert triage, threat context, and case grouping.
- Accelerated threat detection and response with automated workflows for remediation.
- Threat intelligence and defensive analysis from LogRhythm Labs.
- Access to 950+ third-party data sources and 1,100 preconfigured correlation rule sets.
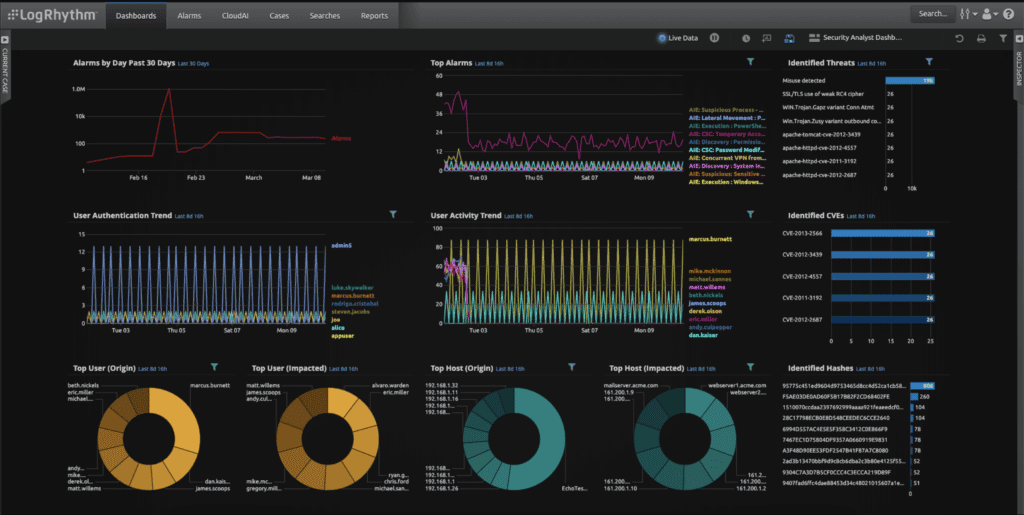 A screenshot of the LogRhythm SIEM dashboards displaying platform data like alarms, user activity trends, and hosts.
A screenshot of the LogRhythm SIEM dashboards displaying platform data like alarms, user activity trends, and hosts.
Read more: An Investment Firm Built Its Own SIEM. Here’s How.

Splunk Enterprise Security
Almost two decades after its launch, the analytics-first Splunk offers plenty to consider in security and observability offerings. Splunk Enterprise Security deployed on-premises or in multi-cloud environments, is designed to detect threats fast and offer teams a flexible route to investigation and remediation. For SIEM capabilities, Splunk Enterprise Security is a scalable platform with over 2,800 apps to connect workflows and data.
Splunk Enterprise Security Features
- Risk classification by users and systems against security and compliance frameworks.
- Scalable platform for ingesting data from structured and unstructured sources.
- Built-in threat intelligence via Splunk Intelligence Management team.
- Deployable as cloud-hosted, IaaS, software, hardware appliance, or hybrid solution.
- Access to 700+ detections for frameworks like MITRE, NIST, Kill Chain, and CIS 20.
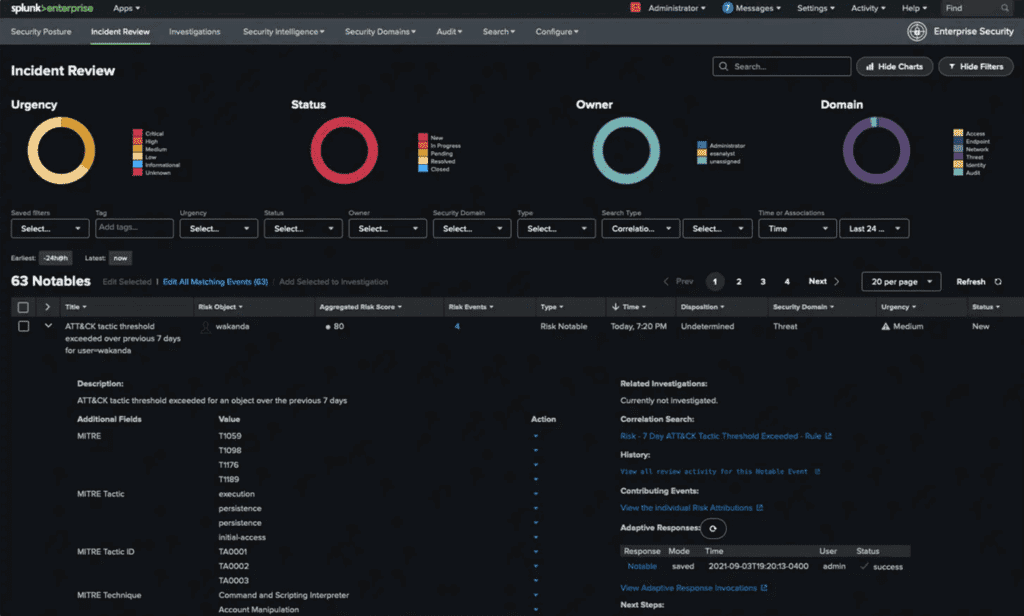 A screenshot of the Splunk Enterprise platform’s dashboard for reviewing incidents.
A screenshot of the Splunk Enterprise platform’s dashboard for reviewing incidents.
Securonix Next-Gen SIEM
Texas-based Securonix continues its streak near the industry top with a stack that includes a next-generation SIEM, UEBA, SOAR, and an open XDR connecting security events and context, incident response, machine learning (ML) detection, and threat intelligence. The Securonix Next-Gen SIEM includes built-in advanced analytics, risk scoring, and threat chain modeling based on MITRE ATT&CK and US-CERT frameworks. With an integrated SOAR, teams can accelerate incident response and reduce response time with playbooks and workflow recommendations.
Securonix Next-Gen SIEM Features
- Ingestion for cloud-based, on-premises, and hybrid environments on a central console.
- Long-term search capabilities for slower threats spanning historical data.
- Cloud-native platform with on-demand scalability and SaaS subscription pricing.
- Access to 350+ cloud connectors for data collection and API-based cloud integrations.
- Use case content and investigation workbench to create cases with industry examples.
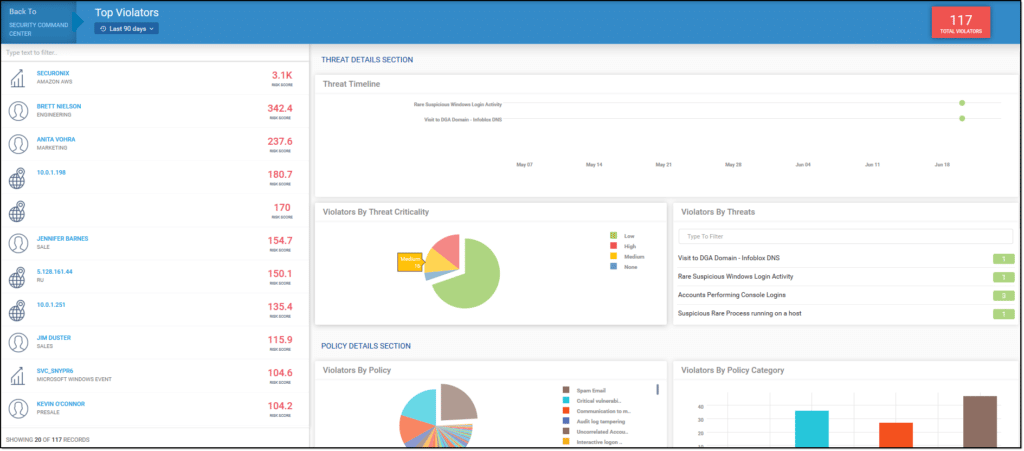 A screenshot of the Securonix SIEM dashboard for recent top violators and corresponding threats.
A screenshot of the Securonix SIEM dashboard for recent top violators and corresponding threats.
Also read: Implementing and Managing Your SIEM Securely: A Checklist
Market Players
Next in line are a few familiar names with robust solutions still serving small businesses and enterprise organizations.
CompanyProductEstHQFortinetFortiSIEM2000Sunnyvale, CALogPointLogPoint SIEM2001Copenhagen, DenmarkMicro FocusArcSight Enterprise Security Manager1976London, UKRapid7Rapid7 SIEM2000Boston, MATrellixSecOps and Analytics2022Milpitas, CA

Fortinet FortiSIEM
Industry-recognized firewall vendor Fortinet offers plenty for small businesses to enterprise organizations. Only one part of an extensive cybersecurity portfolio, Fortinet’s Security Operations includes products for SIEM, SOAR, XDR, and advanced detection and protection like NDR, deception systems, and inline sandbox analysis. Available as a hardware appliance, virtual machine, or cloud-based solution, FortiSIEM offers the most comprehensive array of specs to consider.
Fortinet FortiSIEM Features
- ML-based user and entity behavior analysis to identify insider and incoming threats.
- Real-time monitoring of system performance, availability, and changes.
- Risk scoring for users and devices to evaluate entities and correct behavior.
- Configurable dashboards, shareable reports, and layered analytics.
- Built-in support for vendor APIs and Windows and Linux agents.
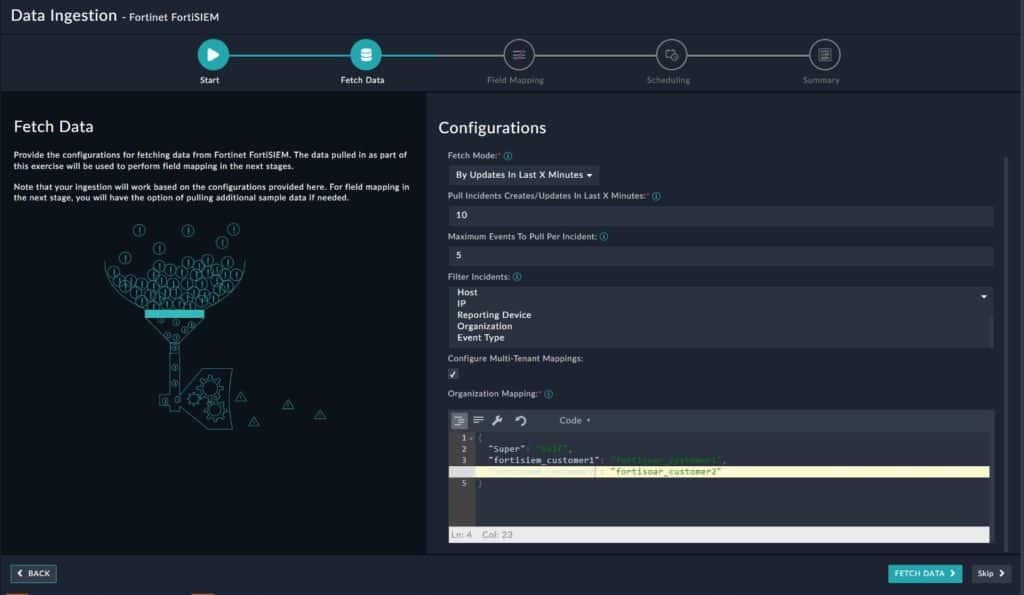 A screenshot of FortiSIEM’s engine for building data ingestion rules.
A screenshot of FortiSIEM’s engine for building data ingestion rules.
LogPoint Converged SIEM
SIEM specialist LogPoint has over twenty years of experience building a security platform that features UEBA, SOAR, and a converged SIEM combining the trio. With focuses on cybersecurity, business analytics, IT operations, and compliance, the Converged LogPoint SIEM is a comprehensive cloud-based solution designed for enterprise or MSSP deployments. LogPoint holds expertise in monitoring infrastructure for compliance via its business-critical application security (BCAS) capabilities for SAP clients.
LogPoint Converged SIEM Features
- Central cloud-based console for data ingestion, event reporting, and analysis.
- Alert aggregation and triage prioritized by severity for analyst review.
- AI-based profiling of normal behavior and patterns to identify suspicious activity.
- Workflow and playbook automation to enable investigation and remediation.
- Integrations for identity-access management (IAM), threat intel, EDR, and cloud APIs.
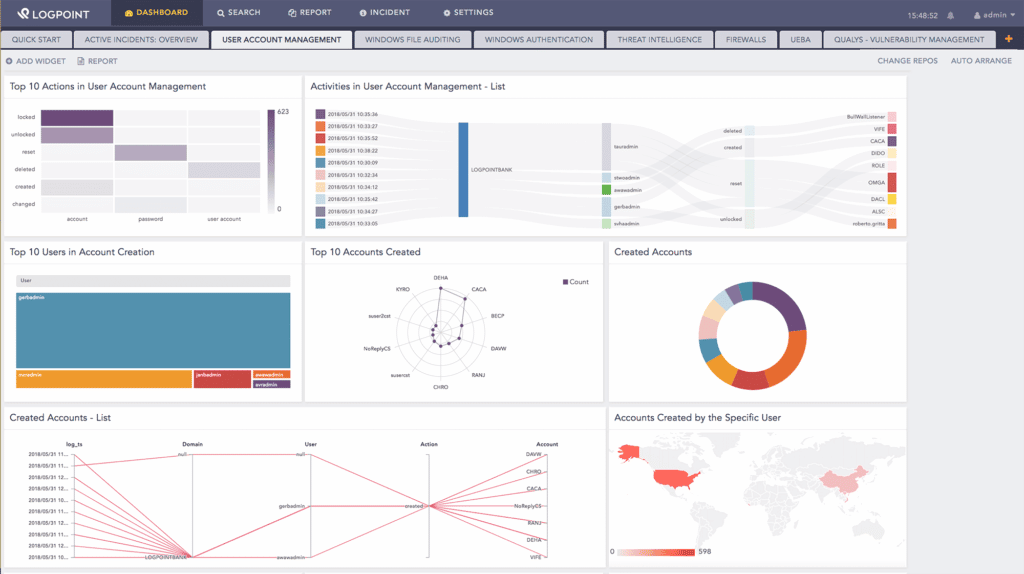 A screenshot of the User Account Management dashboard on LogPoint.
A screenshot of the User Account Management dashboard on LogPoint.
Learn more about EDR with: Top Endpoint Detection & Response Solutions

Trellix SecOps and Analytics
The merger of FireEye and McAfee Enterprise in 2022 created a new brand with a portfolio that includes solutions for endpoints, databases, networks, email, and cloud infrastructure. Previously a part of the McAfee Enterprise Security Manager and FireEye, the industry-leading SIEM is now available under the newly formed Trellix as its Security Operations and Analytics solution. The SecOps and Analytics stack includes Helix for next-gen SIEM integration, Trellix Insights for threat intelligence, and Trellix ePO for on-premises and cloud endpoint orchestration.
Trellix SecOps and Analytics Features
- ML-based user and entity behavior analytics to identify and correlate risks.
- An investigative workbench for alert management, search, and analysis.
- Access to 650 data sources for out-of-the-box integrations and connectors.
- Proactive and preemptive action informed by the Advanced Threat Research team.
- Threat intelligence exchange and advanced threat protection for effective sandboxing.
 A screenshot of the MVISION Mobile dashboard on the Trellix SIEM platform.
A screenshot of the MVISION Mobile dashboard on the Trellix SIEM platform.
Micro Focus ArcSight Enterprise Security Manager (ESM)
The Micro Focus CyberRes business line includes solutions for application security, data protection, IAM, and security operations through the ArcSight Enterprise Security Manager (ESM). ArcSight ESM combines SIEM and SOAR to alleviate the manual workloads of analysts and implement layered analytics across security tools. In 2017, Micro Focus merged with HPE’s software division extending its market position and portfolio of DevOps, security, risk management, analytics, and hybrid IT solutions.
Micro Focus ArcSight ESM Features
- Unified storage of logs capable of big-data searches and visualizing analytics.
- Active scanning for reconnaissance, initial access, persistence, and more.
- Native SOAR capabilities to automate, orchestrate, and enable incident response.
- Real-time correlations and hypothesis-based threat hunting to identify risks.
- Threat monitoring content packages covering MITRE ATT&CK techniques and tactics.
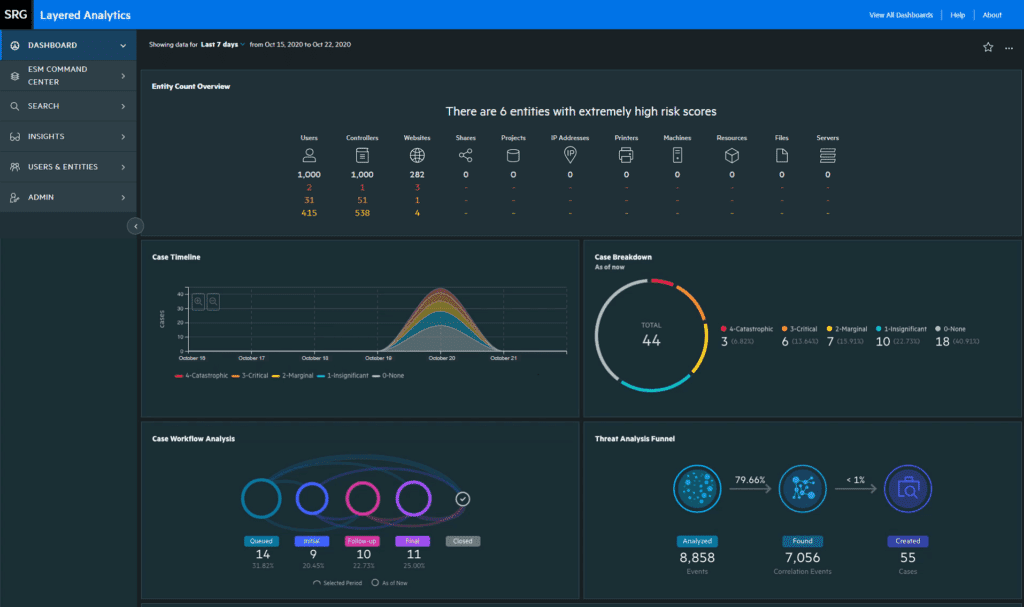 A screenshot of the ArcSight SIEM displaying case data by timeline, type, workflow, and more.
A screenshot of the ArcSight SIEM displaying case data by timeline, type, workflow, and more.
Rapid7
Rapid7 is one of the strongest picks with its flagship SIEM-XDR hybrid solution, InsightIDR. Teams can use InsightIDR to automate repetitive tasks, alert triage, and responses to threat behavior. Alongside products like InsightVM for vulnerability management, Rapid7’s SIEM solution includes EDR, network traffic analysis (NTA), UEBA, threat intelligence, and deception technology.
Rapid7 Features
- Deployable Insight agents for any asset in the cloud or on-premises environments.
- Execute containment actions across Active Directory, IAM, EDR, and firewalls.
- Enhanced endpoint telemetry for historical investigations into activity.
- File integrity monitoring meets compliance frameworks like GDPR, HIPAA, and PCI.
- Access to 300+ plugins for connecting IT and security systems.
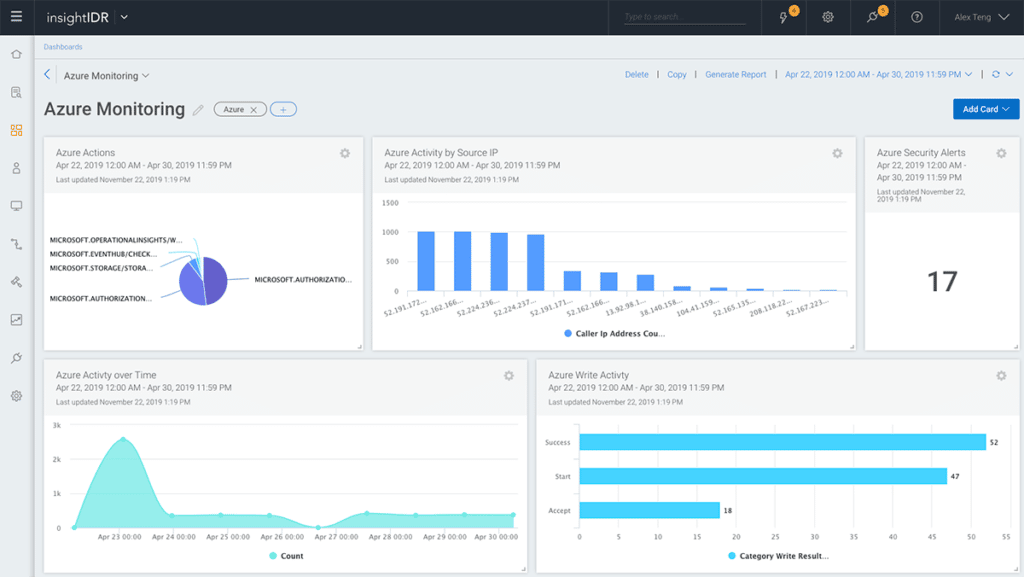 A screenshot of Rapid7 insightIDR dashboard for Azure monitoring data.
A screenshot of Rapid7 insightIDR dashboard for Azure monitoring data.
Also read: SIEM vs. SOAR vs. XDR: What Are The Differences?
Best of the Rest
CompanyProductEstHQAT&TAlienVault USM Anywhere1983Dallas, TXElasticElastic Security2012Mountain View, CAManageEngineLog3601996Pleasanton, CANetWitnessNetWitness Platform1997Bedford, MASumo LogicCloud SIEM2010Redwood City, CA

AT&T AlienVault USM Anywhere
AT&T Cybersecurity and the AlienVault Unified Security Management (USM) go beyond the traditional SIEM solution with a similar stack of advanced capabilities needed for enterprise security. These built-in capabilities include EDR, vulnerability assessment, incident response, and monitoring for file integrity and cloud infrastructures like AWS, Azure, G Suite, and Office 365. Back by a reputable threat intelligence unit with Alien Labs, the USM Anywhere solution remains a top choice for small businesses to enterprise organizations.
AT&T Features
- Utilize kill chain taxonomy to identify behavior in five understandable categories.
- Filter searches by event name, IP address, and more for diving into data.
- Determine vulnerabilities to critical-business assets and prioritize remediation.
- Orchestration rules for select action alarms and raw data related to alarm activity.
- Built-in continuous threat intelligence via a unified management console.
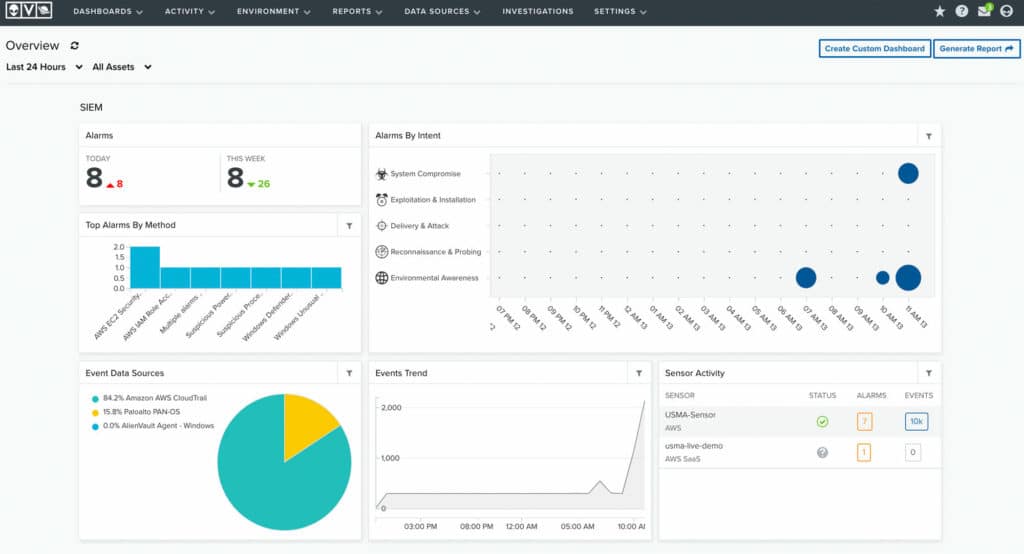 A screenshot of the AlienVault USM platform with recent security event data.
A screenshot of the AlienVault USM platform with recent security event data.
Elastic Security SIEM
Founded a decade ago in Amsterdam, Elastic rose quickly within the SIEM space with the Elastic Stack (formerly the ELK stack) for infrastructure monitoring, application performance, logging, and more. With acquisitions like Endgame in 2019, Elastic Security continues to extend its automated threat protection, incident response, and continuous monitoring capabilities. While Elastic SIEM alone is a considerable solution, Elastic also offers XDR, endpoint security, and cloud security.
Elastic Features
- Uniform analysis from different data sources using the Elastic Common Schema (ECS).
- Block malware, zero-day threats, and ransomware and conduct remote actions.
- Attack detection using MITRE ATT&CK knowledge base to identify adversary behavior.
- ML-enabled anomaly detection, analytics, and insights for threat hunters.
- Interactive timelines for visualizing and working through case management.
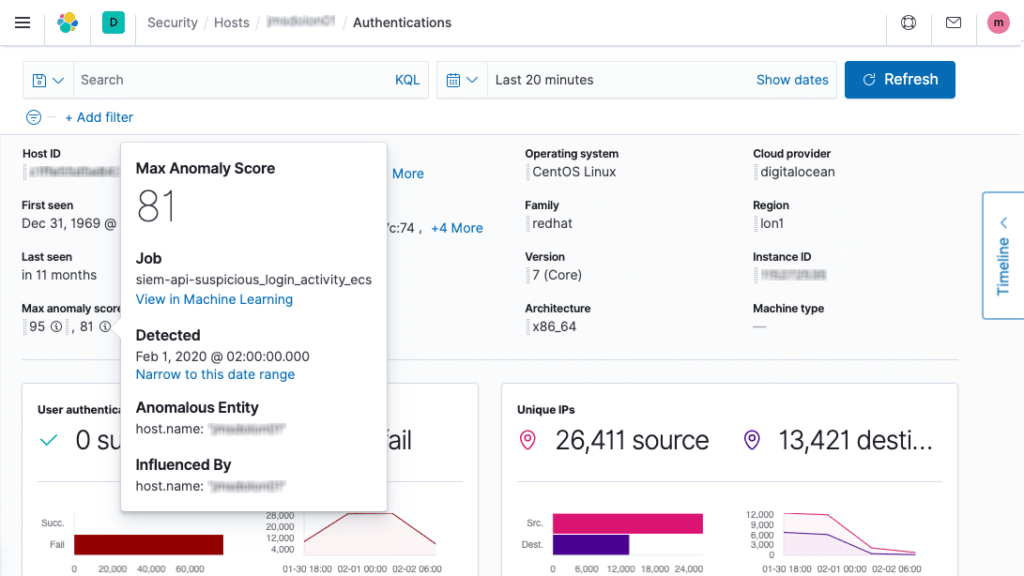 A screenshot showing an anomaly score breakdown on Elastic Security SIEM.
A screenshot showing an anomaly score breakdown on Elastic Security SIEM.
ManageEngine Log360
Twenty years after the launch of ManageEngine, the multi-dimensional IT solutions provider has a portfolio covering identity and access management, IT service management, EDR, and low-code app development. ManageEngine’s stack of SIEM solutions includes on-premises tools for security auditing, log and compliance management, and its flagship Log360 SIEM for cloud or on-premises deployment.
ManageEngine Features
- Integrated DLP, UEBA, and CASB capabilities to detect and respond to threats.
- Collect logs from IDPS, AV, firewalls, servers, networks, and end-user devices.
- Monitor and audit Active Directory with change management and threat tracking.
- Threat intel from STIX/TAXII-based feeds for blocked IP address and URL activity.
- Advanced threat analytics to inspect log data and detect suspicious behavior.
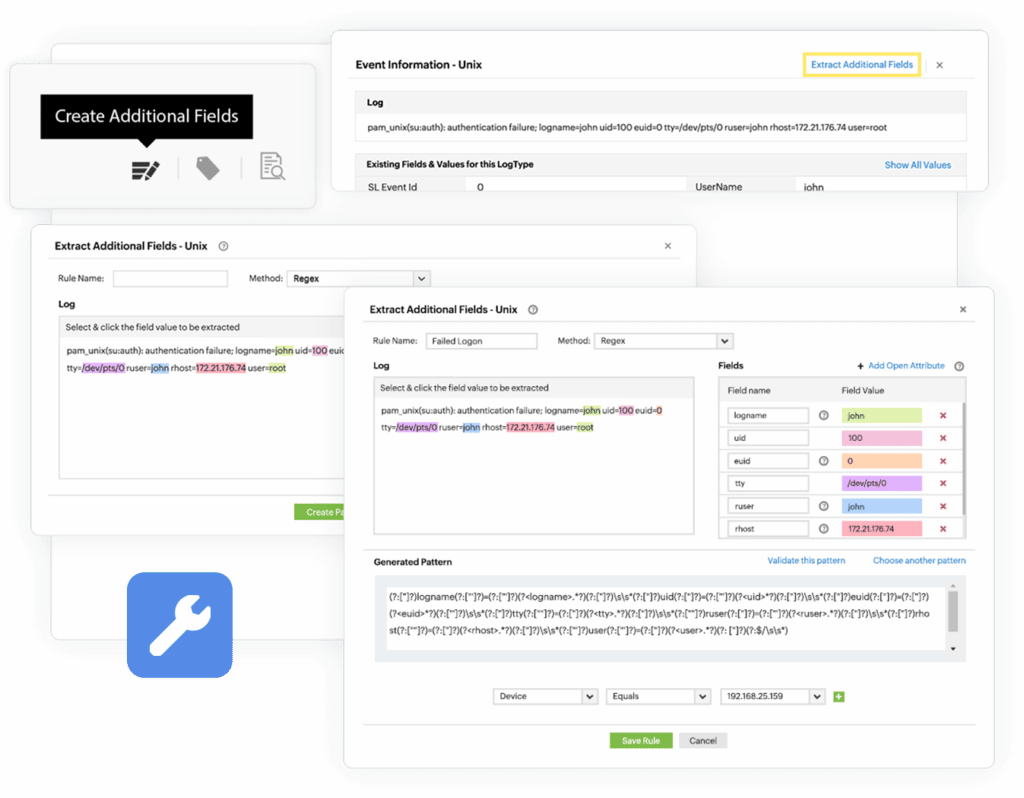 An infographic showing how users can use ManageEngine’s custom log parser.
An infographic showing how users can use ManageEngine’s custom log parser.
Read more: Managed SIEM: A Faster Way to Great Security

RSA NetWitness Platform
NetWitness, the longtime cybersecurity unit within RSA Security, emphasizes an evolved SIEM in an era of expanding attack surfaces and increasingly sophisticated threat actors. Through the NetWitness Platform, teams can centralize all monitoring data for events, endpoints, and networks, with threat intelligence and detection analytics. Features like NetWitness Detect AI offer an adaptive machine learning algorithm to detect and inform security analysts about threats.
RSA NetWitness Features
- User and entity behavior analytics to monitor and identify malicious behavior.
- Deployment options include virtual, on-premises, or cloud (AWS, Azure, and Google).
- Orchestrator for automating security operations and easing SOC analyst workflows.
- Unified taxonomy across data sources to accelerate detection of threats.
- Threat intelligence via industry research, business context, and client data sources.
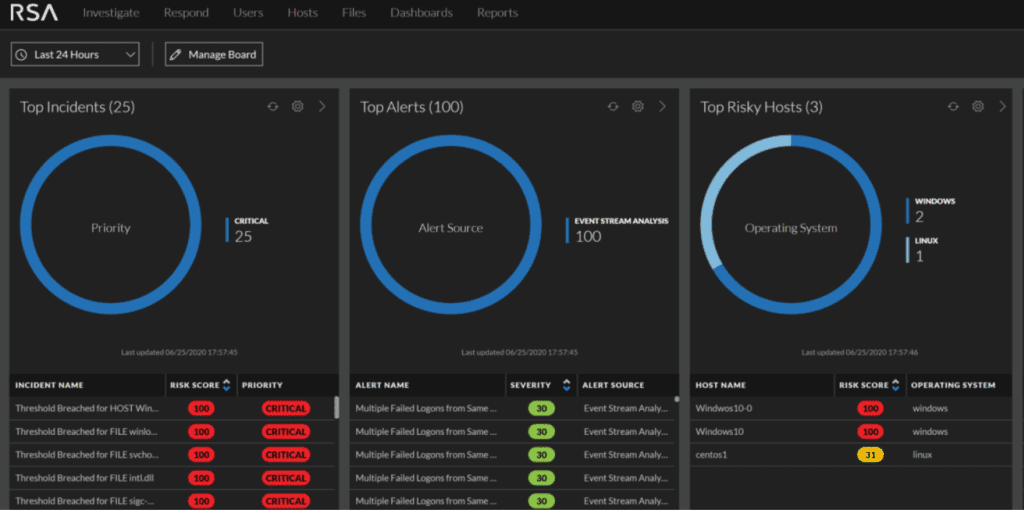 A screenshot of the NetWitness platform visualizes incidents, alerts, and risky hosts.
A screenshot of the NetWitness platform visualizes incidents, alerts, and risky hosts.
Sumo Logic Cloud SIEM Enterprise
Sumo Logic’s portfolio of observability and security products covers needs for infrastructure monitoring, cloud logs, and application development environments. For security solutions, Sumo Logic excels in cloud security, offering monitoring, analytics, audit, and SOAR tools alongside its SIEM. The Cloud SIEM Enterprise solution can cover millions of security-related data across multi-cloud, on-premises, and hybrid environments while mitigating the traditional manual workload for security analysts.
Sumo Logic Features
- Correlation-based detection to cluster and prioritize signal and relevant context.
- Automated alert triage and analysis to inform security analyst decision-making.
- Adaptive Signal Clustering (ASC) engine groups related calls for human review.
- Security monitor with deep packet inspection, which reassembles flows into insights.
- API integration options, including AWS GuardDuty, Office 365, Okta, and Carbon Black.
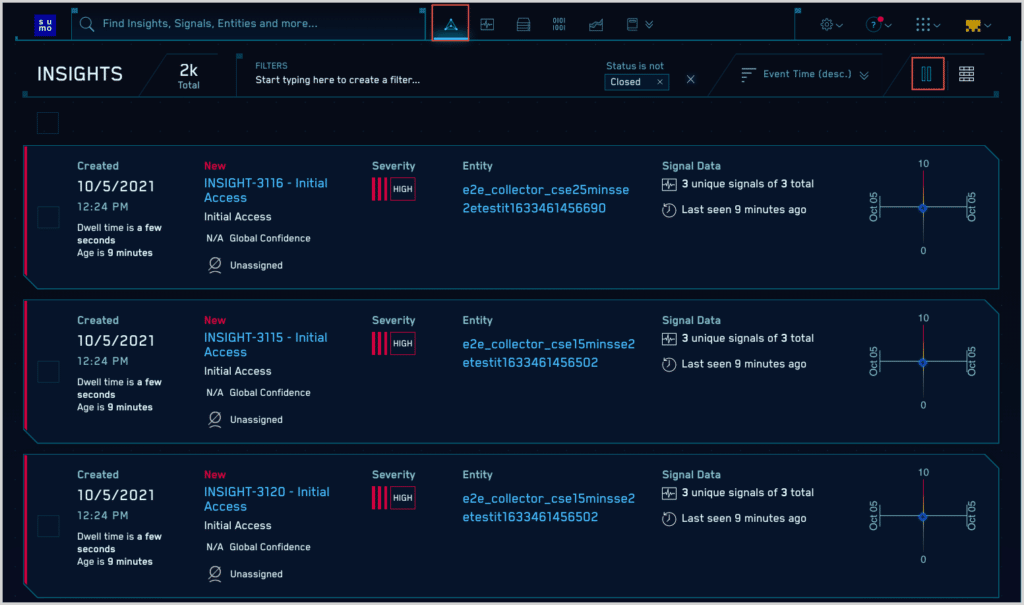 A screenshot of the Insights dashboard on the Sumo Logic SIEM platform.
A screenshot of the Insights dashboard on the Sumo Logic SIEM platform.
Also read: Best Zero Trust Security Solutions
Honorable Mention SIEM Solutions
BlumiraDatadogDevoGraylogGuruculHanSightHelpSystemsHuaweiMicrosoftNetmonasteryNetsurionOdysseySolarWindsStellar CyberVenustech
What is SIEM Software?
SIEM software ingests log and event data from various sources, such as security software and appliances, network infrastructure devices, applications, and endpoints, such as servers and PCs, to give IT security teams a centralized tool for spotting and responding to security incidents.
SIEM Features
Our analysis of the SIEM software market includes over two dozen features and capabilities, including:
- Intrusion detection and prevention systems (IDPS)
- Endpoint detection and response (EDR)
- Advanced threat detection
- User and entity behavior analytics (UEBA)
- Monitoring for databases, apps, networks, email, file integrity, and vulnerabilities
- Threat hunting, digital forensics, and incident response
- Unified management, asset discovery, and compliance reporting
- Automated correlation, risk prioritization, IoC, and responses
- Integration with ERP, SOAR, big data, IAM, and threat intelligence platforms
- Deployable via on-premises, cloud, hybrid, or virtual environments
Read more: Top SD-WAN Solutions for Enterprise Security
How SIEM Works
A SIEM has two closely related purposes: to collect, store, analyze, investigate and report on logs and other data for incident response, forensics, and regulatory compliance purposes; and to analyze the event data it ingests in real time to facilitate the early detection of targeted attacks, advanced threats, and data breaches.
SIEM software works by ingesting and interpreting all that data and incorporating threat intelligence and advanced analytics to correlate events that could signal a cyberattack is underway. The system then alerts security teams of the threat. It suggests responses to mitigate the attack, such as shutting down access to data or machines and applying a missing patch or update.
An example of correlation might be to connect a port scan with access to sensitive data, perhaps in multiple locations, thus adding context to what might otherwise seem to be unrelated events.
Why is SIEM Important?
To get an idea of how vital a SIEM is, consider the scale of the security incidents and data involved. A large enterprise may generate more than 25,000 events per second (EPS) and require 50 TB or more of data storage.
A SIEM’s ability to filter through all the data and prioritize the most critical security issues makes security more manageable. An effective SIEM tool will pay for itself in staff time saved, even as the system itself requires management and tuning.
Also read: Best Third-Party Risk Management (TPRM) Tools
How to Choose a SIEM
SIEM tools are differentiated by cost, features, and ease of use. Generally, the more you pay, the greater the capabilities and range of coverage, so buyers must weigh their needs, budget, and expertise as they decide on a SIEM system.
Small businesses might focus on automation, ease of use, and cost. In contrast, an enterprise with a sophisticated security operations center (SOC) might focus on the breadth of threats and assets covered and machine learning capabilities for discovering new and emerging threats. Regardless of an organization’s size, deploying and integrating such a complex technology can take time, so the help of consultants and services firms is often needed.
Despite its relative maturity, the growth of the SIEM market remains strong. A significant trend is the growing use of behavioral analytics, automation, and cognitive computing to filter out less urgent alerts so security teams can focus on the most significant threats, with advanced UEBA and SOAR capabilities becoming increasingly common.
Analysts see the cloud as a growing means of delivery for SIEM services, both for SMBs and for hybrid organizations seeking more manageable ways to keep track of their complex environments.
Methodology
We gather information from various IT industry sources for our top security products articles. We interview company officials, users, and impartial experts, scouring data sheets and aggregating all information to best inform our content and readers. Our most frequently used sources have been analyst firms Gartner and Forrester, industry testing scores, and user review sites like Gartner Peer Reviews.
This article was written by Paul Shread on January 6, 2021, and updated by Sam Ingalls on August 12, 2022.
Read more: Choosing a Managed Security Service: MDR, Firewalls & SIEM











