Razer Synapse Vulnerability Leads to Windows System Privileges Achievement
A Razer Synapse vulnerability was identified, Razer being a vendor of services in the financial area, consumer electronics, gaming devices, and a manufacturer of peripherals for computers. The technology company is most popular for the gaming keyboards and mouses they produce.
The zero-day has been discovered by researcher jonhat who announced it on Twitter and shared a video sample of how it works. This new bug permits Windows admin privileges achievement. How? With a Razer mouse or keyboard, simply plugging it into a computer. When such a device is connected to Windows 10 or 11, what happens next is that the Razer Synapse software starts to download and install.
Mục lục bài viết
How Does This Razer Synapse Vulnerability Work?
Finding about this Razer Synapse vulnerability and following the demonstration of the security researcher on Twitter, the BleepingComputer publication made a test to see how it works and shared its details. They used a Razer mouse they found. According to their conclusions, the bug works like this:
- They chose one of their computers that ran Windows 10 and possessed privileges that were non-admin.
- In the command prompt, they built a temporary ‘Test’ user.
- Then they plugged the Razer mouse into Windows 10.
- They saw how the automatic download and installation of Razer Synapse software and the driver began.
- System privileges were achieved by Razer’s installation software.
- This was because a Windows process that had system privileges was made use of to initiate the RazerInstaller.exe executable.
- What happens after the Razer Synapse program gets deployed?
- Well, you can choose the folder location where this can be installed because the wizard setup allows you to have this option and this is the moment when the exploitation might commence.
- A ‘Choose a Folder’ window will show when you alter the location of your folder.
- Then you can initiate an “Open Powershell here” by holding Shift and right-clicking on the window.
- In the Folder window, a Powershell prompt will be launched.
- This means that the Powershell prompt will have system privileges because it was opened via a process that possessed these.
- The PowerShell prompt can be opened, then the command ‘whoami” reveals that the console is one with system privileges.
- Following this step, any command can be initiated on the machine.
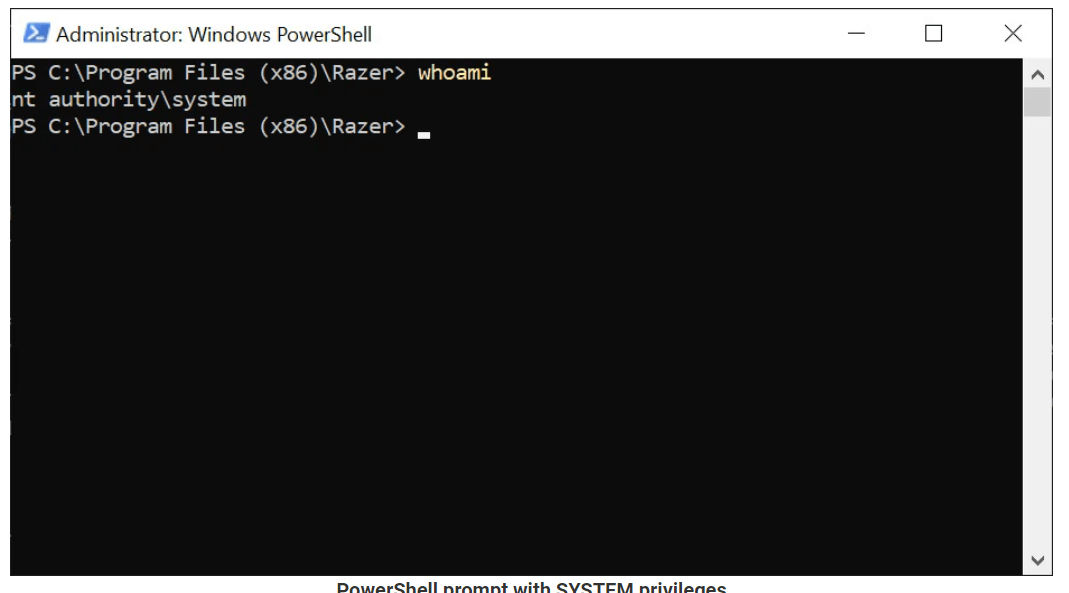
Image Source
What Did the Researcher Say About This?
The vulnerability in the Razer Synapse software was discovered, as I mentioned above, by security researcher jonhat. He initially reached out to the company, but he got no response and he decided to make a Twitter post about it. He also shared a video there where he illustrated how this Razer Synapse vulnerability works.
Video Source
Later on, on the same Twitter page, he announced that the company Razer contacted him back and they discussed professionally with him, by assuring him of remuneration for his efforts even if the bug has already been brought to the public’s attention.
Getting system privileges in Windows is dangerous as this will facilitate the exploitation of the targeted operating system and the running of any command that can also propagate malware, leading to the system’s entire takeover. Razer Synapse software is very popular as 100 million users over the world use it as it permits them to perform hardware configuration, buttons mapping, or macros set-up.
The technology enterprise assured the researcher who discovered this flaw of their immediate action on the topic.
I would like to update that I have been reached out by @Razer and ensured that their security team is working on a fix ASAP. Their manner of communication has been professional and I have even been offered a bounty even though publicly disclosing this issue.
Source











