Reverse Engineering Software Top 10 Reverse Engineering Tools
So you want to be a reverse engineer? You can choose from many professions with reversing skills, like:
- malware analyst – work for AV to fight with malware & ransomware
- exploit developer – find 0day bugs in software
- game cheat developer – get fame & money developing cheats for Fortnite and CS 😀
- kernel developer – low-level hellhole for the toughest ones
Here is the list of the most popular reverse engineering tools used by professionals.
Mục lục bài viết
1. HIEW – An ultimate hex editor & deasembler
HIEW is more than a hex editor. It allows you to modify any binary file, but it also comes with a built-in disassembler for x86/x64/ARM code as well as support for Windows PE EXE formats and Linux ELF.

Website – http://www.hiew.ru/
2. x64dbg – The king is dead, long live the king!
This is a new king of Windows debuggers. OllyDbg days are long over. Meet the new standard in debugging software on the Windows platform. Separate versions for 32 & 64-bit software, plenty of plugins, visual themes, and ongoing upgrades.
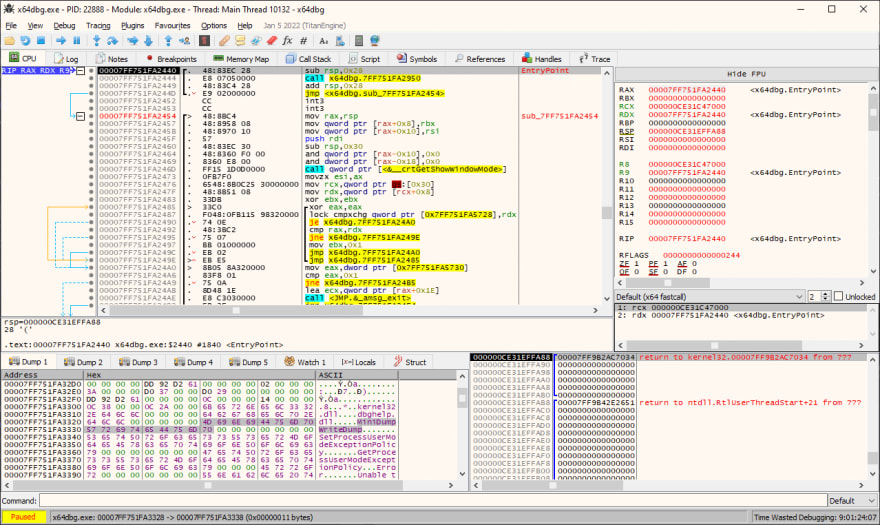
Website – https://x64dbg.com/
3. IDA – Love it or hate it
IDA is an all-in-one tool, it’s a disassembler for many formats of binary files (PE, ELF, MachO, etc.), with a built-in decompiler, hex editor, debugger.

Website – https://www.hex-rays.com/
4. dnSpy – .NET ultimate tool
This is the best reverse engineering tool for any .NET binaries and overall one of the best tools of the past decade. Great design, frequent updates, support for anything related to analyzing .NET code (decompiler, rebuilder, editor).
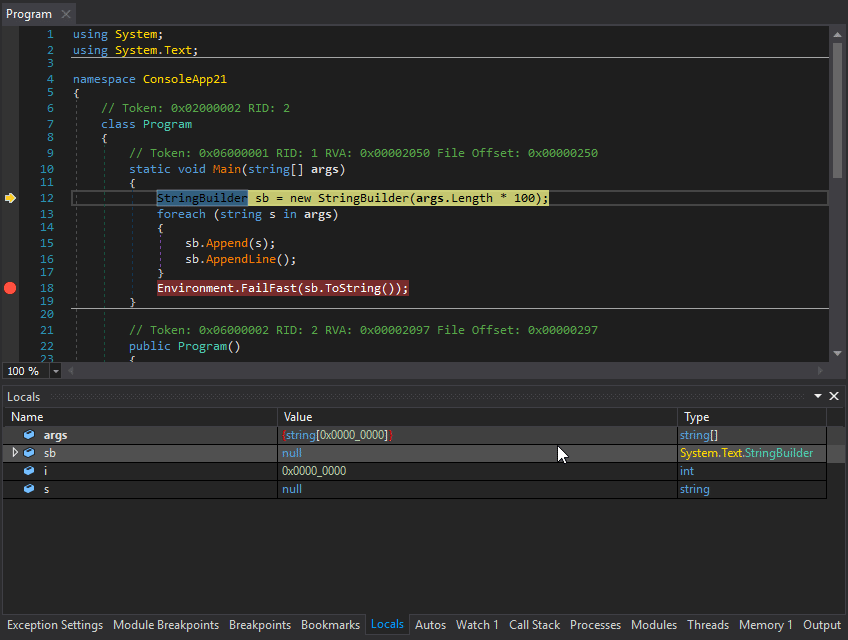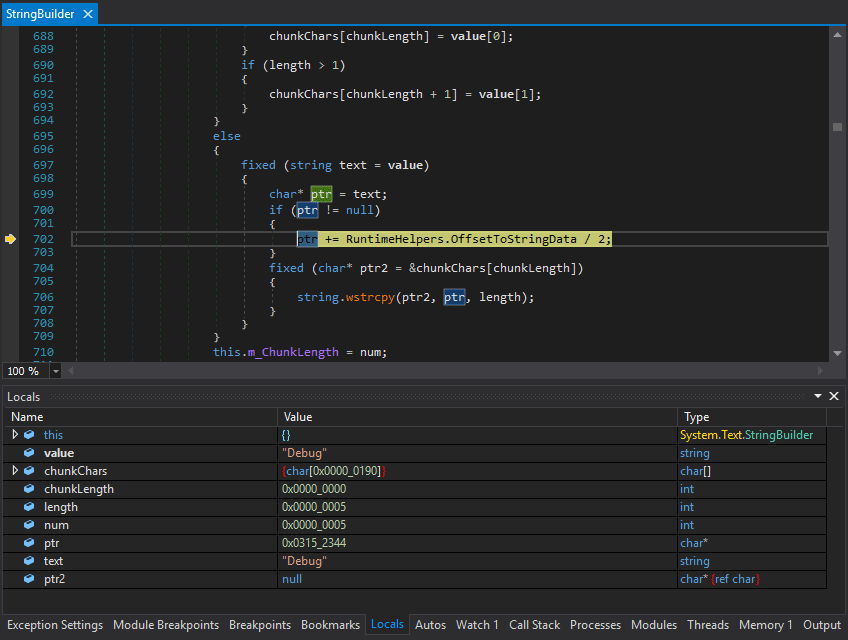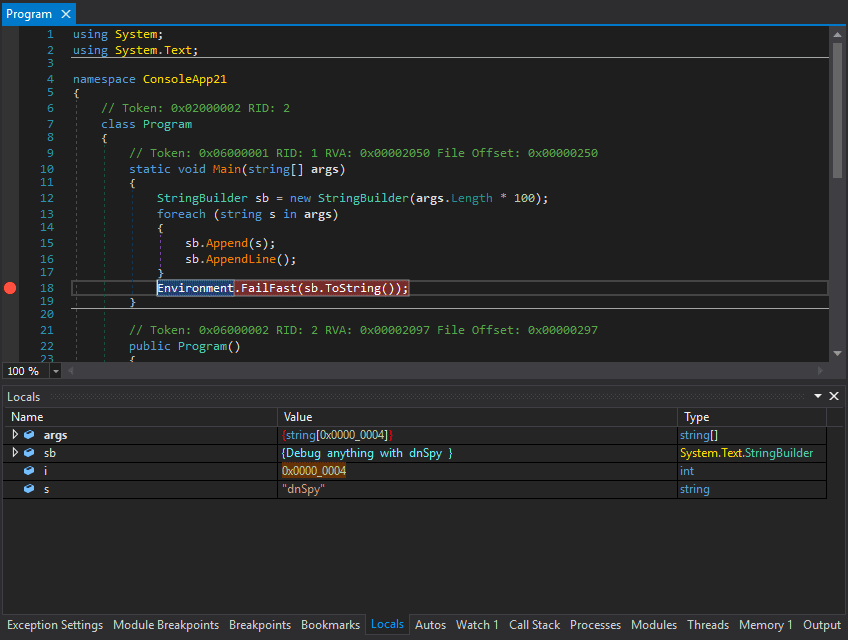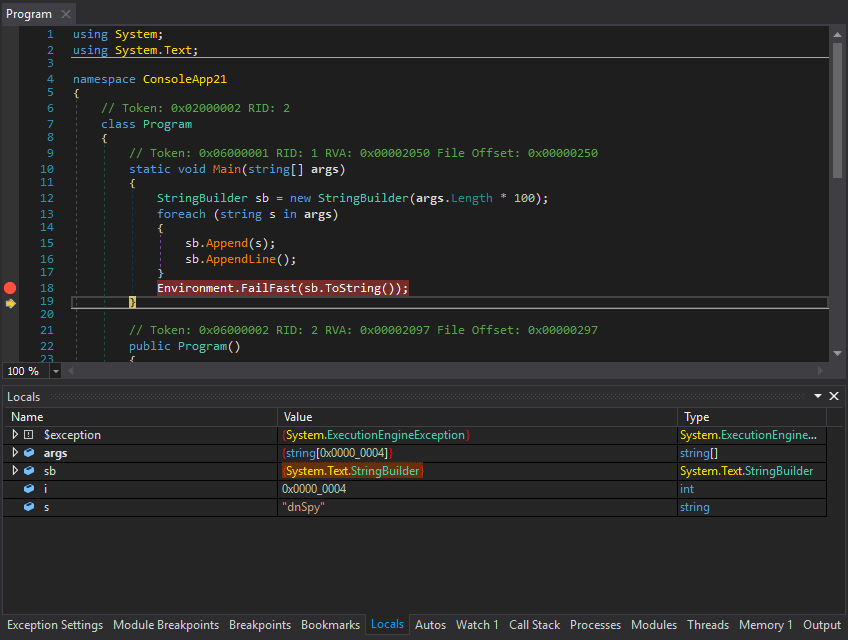
Website – https://github.com/0xd4d/dnSpy
5. Sandboxie – Run unknown code without a fear
Your reverse engineering job might require you to run some unknown, potentially dangerous code, like malware. You can do it in a virtual machine, but with this little tool, you can run it in a sandboxed process, without the fear of damaging your PC.
You can run a debugger in Sandboxie and debug malware. Any changes will be saved only to the sandbox environment.
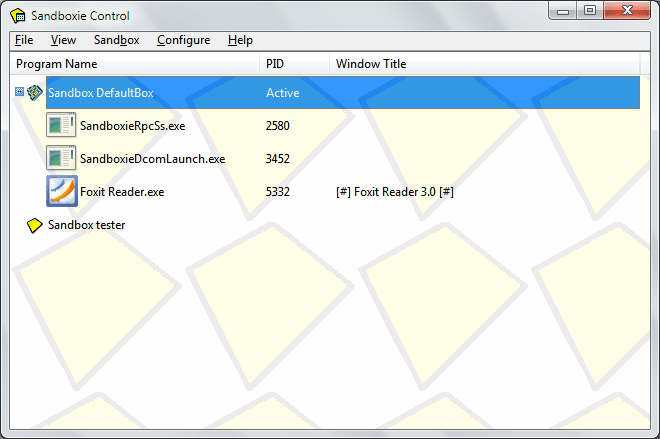
Website – https://github.com/sandboxie/sandboxie
6. Resource Hacker – Hack the planet!
With this little nifty utility, you can see what’s stored inside Windows PE executable resources. You can find many interesting things, like raw binary data, dialogs, bitmaps, strings, icons. It allows you to modify it or replace it with your own versions.

Website – http://www.angusj.com/resourcehacker/
7. DiE – Protections / obfuscators identifier
Sooner or later you will learn most of the closed source software comes protected against people like you and me. There are many different types of protections used to evade reverse engineering tools.
Detect it Easy can tell you exactly which one was used to protect the binary, so it can be easier to find a ready-to-use solution to remove it (for example – an unpacker or a deobfuscator).
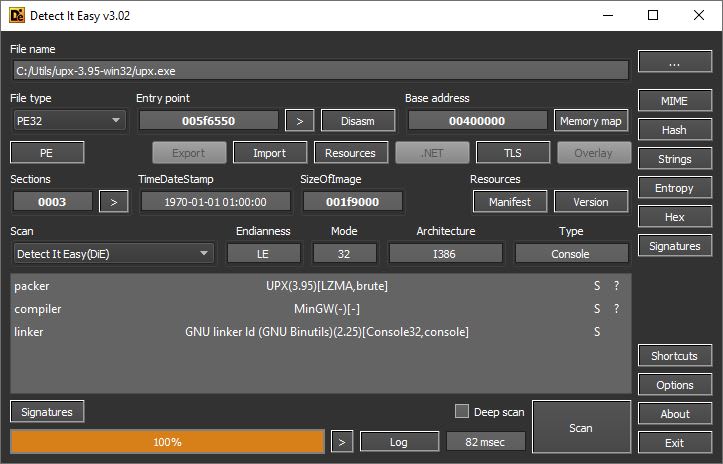
Website – http://ntinfo.biz/index.html
8. Bytecode Viewer – Java decompiler (also for Android apps)
Different application types require different tools. Java compiled binaries are stored in custom .jar archive package. You will need a dedicated tool to analyze it. Bytecode Viewer is a decompiler or four decompilers in one tool to let you see what’s going on inside Java and Android APK apps.
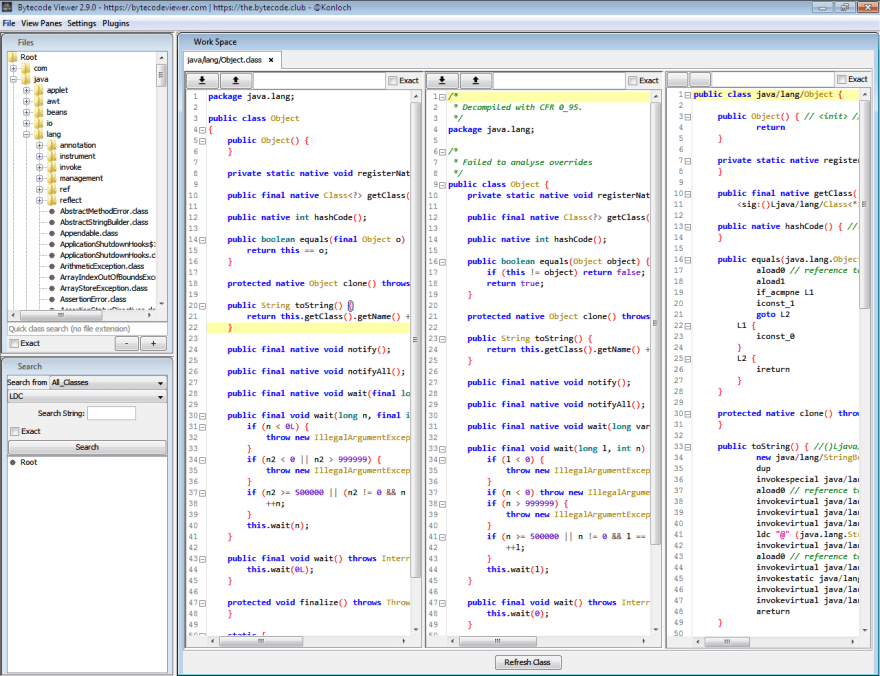
Website – https://bytecodeviewer.com/
9. Process Monitor – Monitor system changes
This is a lifesaver in many many cases. Process Monitor is an advanced monitoring tool for Windows that shows real-time file system, Registry, and process/thread activity.

Website – https://docs.microsoft.com/en-us/sysinternals/downloads/procmon
10. Wireshark – Network sniffer
See what applications send and receive from the Internet. Monitor network activity, find covert communication channels.
Website – https://www.wireshark.org/
Many more reversing tools, some rare ones
More complete list of reverse engineering tools with many alternative versions available in my article:
🔥 Reverse Engineering Tools Review











