Top 10 Cyber Attack Maps to See Digital Threats 2023
With the help of Bromium, we get to know that digital crime result has increased to 1.5 trillion dollars yearly in illegal earnings. In this article, we list the Cyber Attack Maps.
Now many of you might be thinking that what Bromium is? Let me tell you guys that it is a startup company that is basically based in Cupertino, California, and it simply works with virtualization technology, as it offers an advanced malware protection system.
There are many popular websites or web portals like GitHub, EA, and many more that face more extended, hi-tech strikes every day, all while dropping victim to the increasing trend of cybercrime.
Now here the question arises, that who is the attacker, where these attacks are coming from? What’s the top attacker gathering? Thus you can get the answer to all these questions by examining the accounts, then executing lookups for all possible information.
Yes, you will read about the DDoS attacks if you examine the account and about the attacks. Now you may think that what is DDoS? DDoS is a Distributed Denial of Service (DDoS) attack, and with this attack, an attacker simply tries to attempt to produce an online service unavailable by overwhelming it with traffics from various sources.
DDoS strikes target plenty of valuable resources, from banks to news websites, and offer significant difficulty for internet users so that they won’t able to reprint and access vital information. With these, Cyber Attack Maps you can see the DDoS attack packets, between the origin and destination.
Thus if you are overlooking a low to mid-size Distributed Denial of Service (DDoS) attack, then you can investigate the data logs and obtain the information you need to defend yourself from specific attacks. Although, with more significant attacks, manual lookups are time-consuming and quite weak as well.
Hence, the defender needs to have other plans so that they can fight cyber attacks efficiently. But, if you are not encountering a DDos attack, and want to learn about top digital attacks so that you can get some knowledge from the cybersecurity conflicts encompassing the world then you are in the right place.
But the question arises that where would you look about this information? Don’t worry, as you can simply try the internet service providers (ISP); it tells you to check out anti-DDOS providers. Therefore you can see what’s occurring right now by watching at digital attack maps, simply to see and track whereby cybersecurity operates globally.
Moreover, you can also witness cyber-attacks and how ill-disposed packs interact between countries. Therefore We are going to discuss the top 10 cyber attacks maps to see digital threats so that you can simply watch the classification of visual digital threat conflicts.
So, not without wasting much time let’s get started and simply explore the whole Cyber Attack Maps list that we have mentioned below.
Mục lục bài viết
10 Cyber Attack Maps
- Kaspersky Cyber Attack Map
- Norse Attack Map
- Arbor Networks
- Digital Attack Map
- Trend Micro
- Fortinet Threat Map
- FireEye
- DDoS & Cyber Attack Map
- Checkpoint Cyber Attack Map
- Akamai
At first, we have a Kaspersky cyberthreat, it is one of the most extensive maps among all the maps available on the internet. Thus it works at its best when it comes to the graphical interface. Moreover, It also seems amazingly smooth.
 Kaspersky Attack Map
Kaspersky Attack Map
Therefore it mainly implies internet devastation. When you open the map, it recognizes your current location and exhibits the states for your country, and not only that even it also includes top social attacks and viruses from the past week.
Here are
some activities detected by the Kaspersky map:-
- On-Access Scan
- On-Demand Scan
- Kaspersky Anti-spam
- Mail Anti-Virus
- Botnet activity detection
- Web Anti-Virus
- Intrusion Detection Scan
- Vulnerability Scan
 Norse Attack Map
Norse Attack Map
Next, we have a Norse attack map, it’s one of the well-known cyber-attack maps, and in general, it is a security firm that has its part of a query over the last few years.
Considering the data displayed on their map, Norse states that the attacks are “based on a small subset of live streams against the Norse honeypot foundation. Interestingly sufficient, companies can add their logo to the map when it is revealed at the office.
 Arbor Networks Map
Arbor Networks Map
We have Arbor networks in the third position, its one of the famous attacks on the list, this is a hybrid map that was created in part with Google ideas.
Moreover, the digital attack map traces DDoS attacks with data from Arbor’s ATLAS threat intelligence operation. Thus the new data is sourced from more than 300 ISP customers and 130Tbps of global traffic, hence, the map will visualize DDoS attacks and provide filtering by size and type.
 Digital Attack Map
Digital Attack Map
Digital Attack Map is a live map that simply shows the visualization data of DDoS attacks around the globe, and not only that even Digital Attack Map is also built through a collaboration between Google Ideas and Arbor Networks.
Moreover, this attack map simply helps you to filter the map with various options, so that you can simply identify the attacks by size like, Large, Unusual, and Combined.
Even you
can also identify them by attack type as well:-
- TCP Connection (filling
connections) - Duration
- Volumetric (eating bandwidth)
- Application
- Fragmentation (pieces of packets)
- Source & destination port
number
Hence, we all know very well that DDoS is a threat to the online market, as it can take down your online appearance, hurt the status, and damage you financially.
Therefore, If you are a business proprietor or web producer, then you may examine preserving your online assets from DDoS attacks by utilizing services like SUCURI, Cloudflare, and many more.
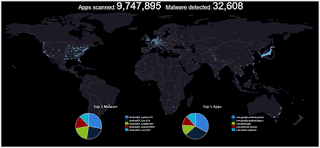 Trend Micro Map
Trend Micro Map
Next, we have Trend Micro on our list, it is a Botnet Connection Dashboard and is a more modest, stripped-down cyber attack map that traces C&C (Command and Control) servers managed by botnets across the globe.
However, the age of the data presented isn’t apparent, but the traditional data traces back 14 days.
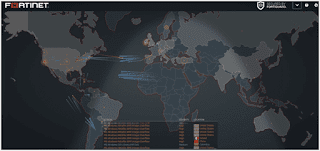 Fortinet Attack Map
Fortinet Attack Map
After Trend Micro, we have the Fortinet Threat Map, it looks comparable to the one from Norse and seems to show playback of recorded cases.
Hence, the attacks are represented, a rotating division of numerous stats arrives in the lower left part of the screen. Moreover, the most interesting thing about this map is Fortinet customers can simply have a map of their own, as per the documentation.
 FireEye Threat Map
FireEye Threat Map
FireEye is one of the well-known cyber attack maps available on the internet nowadays, as it generally allows you to get a unique summary of whole attacks with the following data.
- Top attacker by country
- Top attacker by country
Apart from all these things, FireEye is not as complex as the above maps, and it is really beneficial if you are studying for data in industry and country wise. Hence, if you are seeking to get any information regarding this subject then undoubtedly you should consider this map once.
 DDoS & Cyber Attack Map
DDoS & Cyber Attack Map
Here comes the DDoS & cyber-Attack Map, it is a global cybersecurity situational knowledge platform. Thus this threat Map implements highly contextualized visibility within a comprehensive warning landscape exercise that is tailored for every business’s particular vertical and geographic profile.
Moreover, it uses a variety of tools and methods to gather and examine threat data. Therefore we strongly concentrate on the abilities and potential of DDoS and cyber attacks, simply by picking out various indicators of an attack campaign.
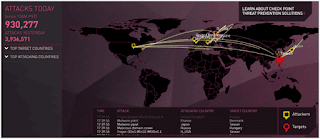 Checkpoint Cyber Attack Map
Checkpoint Cyber Attack Map
Now we have the Checkpoint Cyber Attack Map, this is one of the maps which provides the ThreatCloud cyber attack map from Checkpoint Software. Hence it shows historical data that is reset each day at midnight PST.
Moreover, the map is more visual than the one from Norse but yet has the same underlying construct. But there is one additional feature that is for watching the playback, the top critics and targets can be seen and observed historically, with monthly and weekly stats.
 Akamai Attack Map
Akamai Attack Map
At last, we have Akamai, if we talk about this cyber attack map the let me clarify that this map doesn’t have anything extra. However, Akami is one of the leading content delivery network (CDN) services providers available on the internet for media and cloud security solutions.
It offers a real-time web monitor that gives information about the network and attack traffic summary, and not only that even you can also filter by region as well. Moreover, apart from all these things, the network of Akami is available in over 130 countries within more than 1700 networks.
Conclusion
Nowadays, cyberattacks, along with spam and malware infections, are growing very rapidly, while the cyber attack maps that we’ve examined above won’t help you to mitigate these malicious threats, but the fact is that it will be surely useful to have a clear view of the top risks in business all around us.
While studying these digital attack maps, it’s
getting clear that no one in this hyper-connected business has ever been safe from
network threats, therefore it significant to know about the maps so that users
can easily know about the upcoming threats or attacks.
Thus if you are a part of any public or private cybersecurity team, then start with the basics like examine your attack surface by implementing security audits to overcome the vulnerabilities in your organization.
Hence examine these cyber attack maps, and it will surely help you to recognize the attacks, so, if you liked this post, then simply do not forget to share this post with your friends and on your social profiles.











