What Is a Miner Virus and How Can You Remove It?
Because cryptojacking requires increasing processing power to mine cryptocurrencies like Bitcoin, miners are discovering new ways to wield that processing power. One such way is to borrow it from thousands of unwitting internet users.
Bitcoin became incredibly lucrative in 2017, when the price skyrocketed toward a walloping $20,000 per coin. In fact, personal devices were doing more cryptocurrency mining than anything else that year. Digital money had taken the internet by storm, and you’d better believe there were people who would find unscrupulous ways to profit from it.
A Bitcoin miner virus can be so aggressive that it drains your battery in no time, renders your computer unusable for long periods, and shortens the life of your device.
One result was the development of Bitcoin mining malware. Hackers developed ways to hijack processing power from machines used by people like you — which, when multiplied by the thousands, dramatically increases the chances of successful mining. The idea is that it’s a much cheaper alternative to shelling out thousands of dollars for dozens of ASIC miners (the traditional way to mine cryptocurrency).
Mục lục bài viết
How does cryptojacking affect you?
The individual who infects your computer with cryptocurrency mining malware is doing so only to make a buck. Strictly speaking, cryptojacking is not about accessing or sharing your private information.
But, cryptojackers are using your system resources without your knowledge or consent. A Bitcoin miner virus can be so aggressive that it drains your battery in no time, renders your computer unusable for long periods, and shortens the life of your device. Not only that, but your electricity bill goes up, and your productivity goes down. It’s safe to say that this constitutes a security breach.
It’s important to note that you will almost never run into cryptojacking operations targeting Bitcoin. Because Bitcoin requires huge processing power to mine, it’s not possible to do so using cryptojacking. But as the most well-known cryptocurrency, “Bitcoin” is sometimes used to refer to all types of digital currency. “Bitcoin miner virus” is a catch-all term in the same way.
Only smaller cryptocurrencies like Monero can rely on pedestrian hardware specs, meaning that they can be mined with cryptojacking malware. The untraceability of Monero transactions is another factor that makes Monero an ideal target for this brand of cybercrime. But regardless of the kind of mining operation that may have infected your system, you’ll want to put a stop to it right away with a strong antivirus tool.
AVG AntiVirus FREE will detect and block all kinds of malware infections, from cryptojacking to spyware to run-of-the-mill viruses. Download it today to get 24/7 online protection.
Different types of miner viruses
There are multiple ways you can get cryptojacked, and they differ in their traceability. Let’s take a look at two of the most common methods.
Browser-based miner virus
Website scripts are common ways for cryptojackers to take control of your computer. Because scripts are functions that run behind the scenes and have a certain amount of access to your computer, they are ideal for browser-based Bitcoin mining. Hackers have also been known to find backdoors in WordPress databases and will execute code there, as well.
All you have to do is visit a particular website without protection (or with out-of-date software), and an invisible script will tell your computer to start mining. This is usually true only for compromised websites, which is why it’s so important to make sure the websites you visit are safe. But even reputable sites have been known to sustain occasional attacks, as we will see. In the best-case scenario, the mining stops as soon as you leave the site or close the browser.
Victims of cryptojacking can expect the resources of their CPU to be pushed to their limit.
Email attachments and sketchy links are other ways that hackers can get your computer to run bad code. Make sure to double-check any email before clicking anything. Be wary of Facebook or other platforms asking for your password for no reason. Don’t believe every button that tells you that you need to update Firefox or Chrome, either. If it’s not coming from the browser’s official website, that button could install mining software onto your browser. And it probably won’t go away when you close your browser.
Victims of cryptojacking can expect the resources of their CPU to be pushed to their limit. Even GPU exploitation, where powerful video cards are tapped for their capacity, can occur. This translates to a slow-down in computer performance and an increased electricity bill. It doesn’t sound so bad compared to, say, identity theft. But it is still very much a security issue that you should protect yourself against.
Adware Bitcoin miners
Adware Bitcoin miners are another type of cryptojacking malware. Once they’ve infected your machine, adware bitcoin miners sit on your computer as installed programs or lines of code embedded in RAM, making them far more dangerous than some other forms of cryptojacking.
From deep within your system files, file-based adware can disable your antivirus. It can ensure that a copy of itself is always installed on your computer. It can even detect when you’ve got the task manager open and pause its activity accordingly. That means you would never see a CPU usage spike, and you would never see the name of the program sucking up all your resources.
Sometimes a miner virus appears as fileless malware: commands executed from the computer’s memory or essential OS operations. That makes it much, much harder to detect.
Fileless malware can be extremely difficult to detect and remove.
Using an individual’s computing power without their permission and draining the productivity and life of their hardware is bad enough. Burrowing into the inner workings of a machine, crippling its functionality, and hiding any trace of the malware is even worse and more invasive.
If you’ve recently downloaded a program that looked like the real thing but was actually “off-brand,” so to speak, you might have cryptocurrency malware installed. A specific example is Auto Refresh Plus, which disguises itself as a mandatory update to Mozilla Firefox. Once it’s installed, it begins mining cryptocurrency in the background while bombarding you with unwanted ads. You’ll need an anti-malware program to remove it from your system.
Notable cryptojackers
There are a couple of names you should know about if you want to stay abreast of the cryptojacking phenomenon. Coinhive was a service that tried to mine cryptocurrency for good uses, but ended up being misused. RoughTed, a totally separate phenomenon, is the umbrella term for a cybercrime campaign involving many different illicit activities. Let’s take a deeper look.
What is Coinhive?
Coinhive started as a legitimate alternative to advertising, generating revenue with your PC’s CPU resources while you were on a webpage. The idea was great — a script on the website would tell your computer to mine for the cryptocurrency Monero. In turn, the website wouldn’t need to host ads!
It had many potential applications. UNICEF Australia collected donations with the message “Give hope, just by being here” on a page with Coinhive running. As long as the page was open in a browser, the person’s computer would continuously mine for Monero, generating donations.
While the original intent behind Coinhive was to use only a portion of a person’s computing power, the result was that cryptojackers turned the knob to 11, slowing down the computer to the point of unusability.
What went wrong? A few bad actors used the tech for their own personal gain. Coinhive became prevalent on hacked websites. While the original intent behind Coinhive was to use only a portion of a person’s computing power, the result was that cryptojackers turned the knob to 11, slowing down the computer to the point of unusability.
Things got real for the UK’s National Health Service when they discovered that their BrowseAloud accessibility software, which uses a voice to read websites for the benefit of the blind, was hacked with Coinhive to mine Monero. Increased CPU usage aside, much more alarming was the security breach itself. The amount of private information which could’ve been leaked is staggering.
Ad-blockers and antivirus software had to keep up and block these scripts from running, and cryptojacking became a veritable security breach. It didn’t matter how it was being used; it was simply too easy for websites to mine without permission.
On top of that, services which sought to mine cryptocurrency ethically still failed to ask for permission, discouraging many who might have otherwise advocated for it. That happened with the peer-to-peer, file-sharing site The Pirate Bay, which replaced banner ads with Coinhive without telling anyone. Not only that, but The Pirate Bay configured Coinhive incorrectly, causing users to experience a massive spike in CPU usage upon visiting the site.
The Pirate Bay received plenty of backlash. With the technology being misused in so many different ways, cryptomining as an alternative to ads was dead in the water. Coinhive closed up shop in 2019.
What is RoughTed?
RoughTed is an organized cybercrime campaign that has changed the whole game of cybersecurity. Imagine malware that takes advantage of something we see every day on the internet: ads. If hackers could take advantage of third-party ad networks distributing ads throughout the internet, half of the work would be done for them. They’d have a vast, multi-pronged attack that was so spread out that it would not only hit a huge number of people, but it would also escape easy detection.
Unfortunately, you don’t have to imagine that, because it exists. It’s called malvertising. On websites all across the internet, ads are telling computers to mine for cryptocurrency.
How do you convince an ad network to distribute your shady ads?
-
Obfuscate. Write code that looks innocent. Programming languages are just that — languages. Malvertising campaigns are able to slip past certain filters by rewriting code.
-
Use shady networks. There are networks that display ads for The New York Times, and those that display ads for gambling sites or pornography sites. Which sites do you think care more about how their ad space affects their users? The NYT cannot risk their reputation, but as long as a gambling site can get an extra dime, who cares what kind of ad it shows?
-
Make the ads look legit. You might think there is a correlation between an ad’s appearance and what it’s doing behind the scenes. There is none. The ad could be for anything at all, look crisp and elegant, and still contain malicious code.
-
Hijack an existing ad network. Legitimate sites like The New York Times are not entirely immune. In fact, the NYT started unwittingly displaying malicious ads in 2016, all coming from a compromised ad network. RoughTed still has not been stopped, even as it makes Amazon’s Content Distribution Network do their work for them.
-
Redirect. Redirecting is how someone comes into contact with the malware in the first place. The ad runs a script that sends the user to a malicious server — but only if they are using outdated software. For many users, the malicious ad will do nothing harmful. That makes it harder to detect.
-
Keep redirecting. For the victims as well as the hosts, an endless amount of redirects (or a set of legitimate-looking ones) will help hide any shady activity.
That is how cryptojacking can spread throughout the internet. Unfortunately, cryptojacking is among the more moderate of RoughTed’s offenses. The campaign has also been known to compromise personal information and infect devices with sluggish malware. That’s why it’s important to know how to detect and prevent cryptojacking and other malware.
How to know if you’re infected
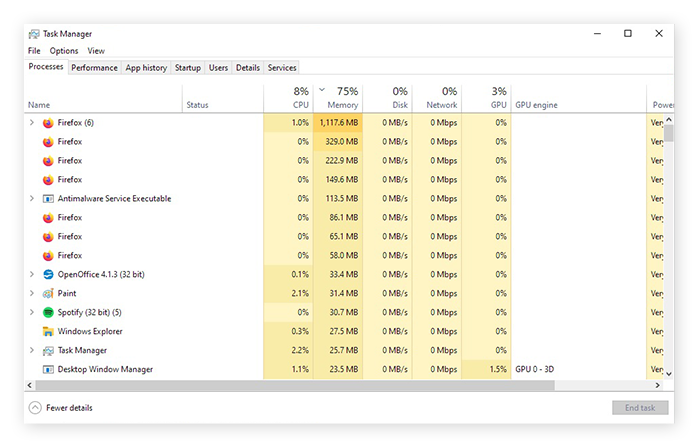
To find out if you’ve been infected, the first step is to check your CPU temperature — usually high CPU usage is a big red flag. With a cryptojacking infection, your computer works much more slowly than usual, and the fan sounds like a jet engine on take off. This is the cryptojacking software using all of your computer’s resources to mine the cryptocurrency. To know for sure, open Task Manager and look at the Performance tab, paying special attention to the CPU. If it’s hitting 80 or 90% without any programs open, something’s definitely wrong.
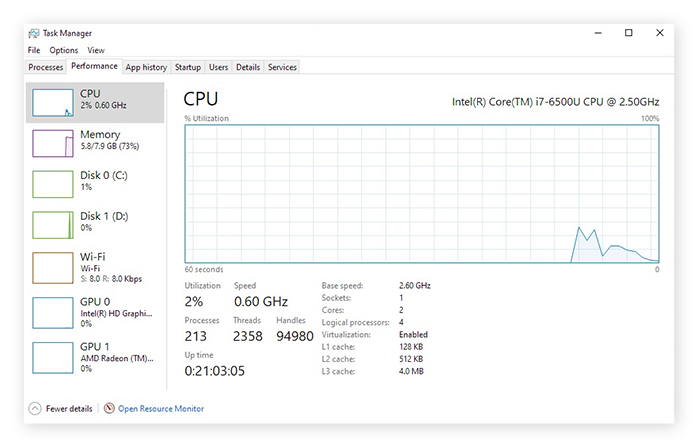
Additionally, you should know how to spot a Bitcoin miner. CPU and GPU overuse slows down system processing, sometimes to the point of overheating. Bitcoin mining malware detection isn’t just about removing a nuisance from your device; it’s about improving the lifespan of that device. Loapi Monero-mining Android malware caused enough overheating to break devices.
Covert cryptocurrency miners can present as adware, as well. Be sure to watch out for the typical signs that you’ve got adware. These include, as the name suggests, ads appearing where they shouldn’t and a web browser acting with a mind of its own, like installing new toolbars or visiting strange sites.
(While we’re on the subject, it’s also good to know how to tell if your phone has a virus, even though it’s highly unlikely that your phone has been jacked to mine cryptocurrency.)
How to remove a bitcoin miner virus
The process for how to get rid of a Bitcoin miner is largely the same as getting rid of other malware.
The first step is to run a trusted antivirus. AVG AntiVirus FREE is a top-notch cybersecurity tool that will help you remove malware and block future infections. We’ll show you the best way to use it to rid your computer of any pesky miner viruses. Let’s download and install AVG AntiVirus FREE to get started.
-
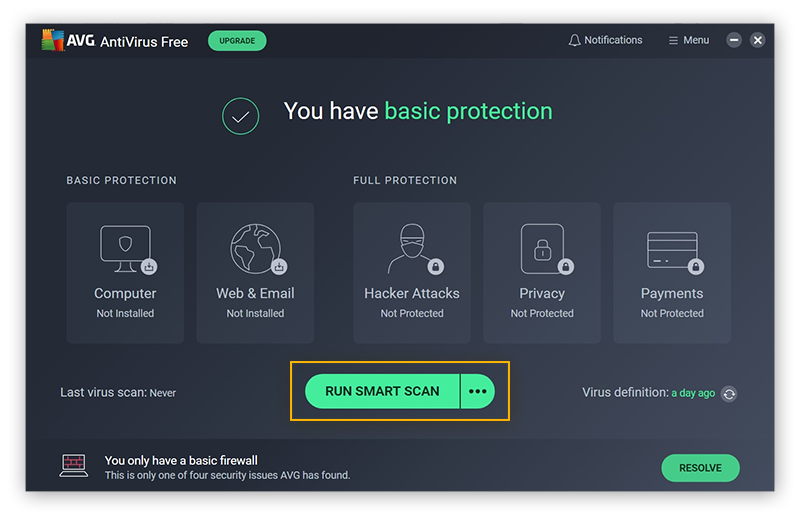
Open AVG AntiVirus FREE. You can click Run Smart Scan, but it might also be a good idea to try a different kind of scan, since miner viruses can hide so well. To run a different scan, click the three dots next to “Run Smart Scan.”
-
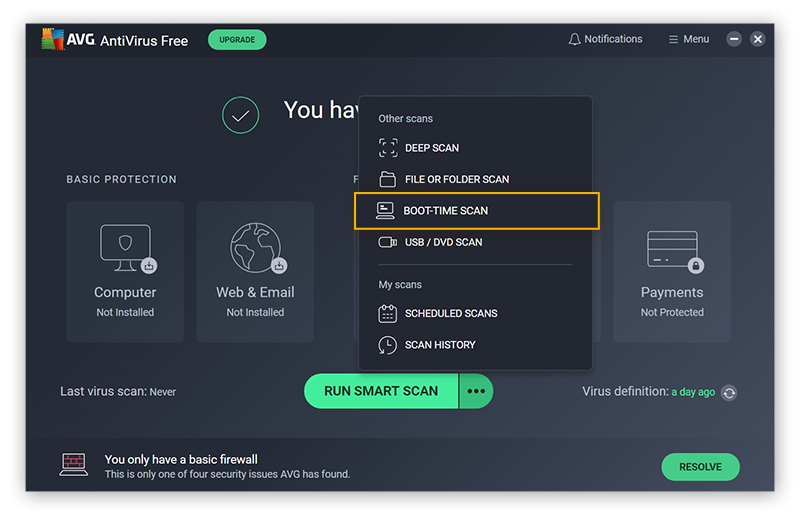
Choose Boot-time Scan. This deep scan will check for more hidden threats.
-
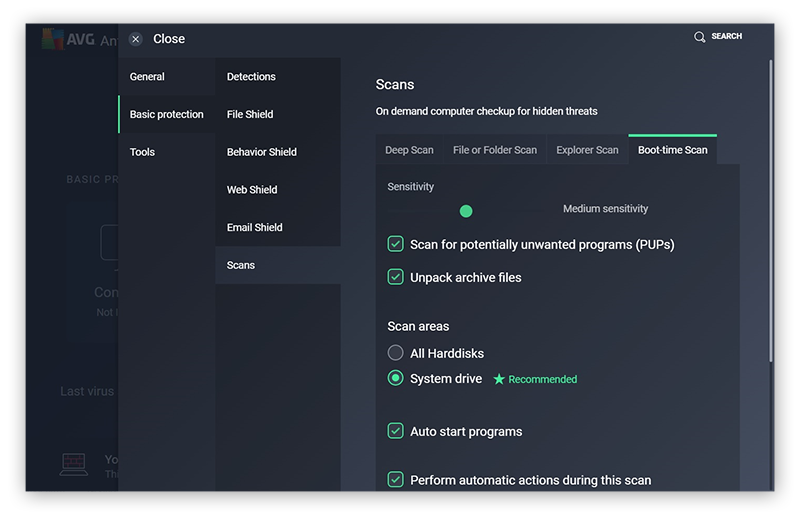
Review the options. Scroll down and confirm.
-
Click Run on Next PC Reboot to schedule boot-time scan.
-
Reboot your PC to perform the boot-time scan. If a miner virus or any other threat is discovered, you’ll be able to delete it right away.
-
AVG AntiVirus FREE will regularly scan your machine to keep you protected from any additional infections.
While we’re on the topic of good security habits, take a moment to clear your browsing and search history. These are files that your computer saves and displays when you visit a site, so it doesn’t have to download the same files again. And while you’re at it, delete your browser cookies, too. Browser cookies track your information, and you don’t want bad cookies eating their way into your hard drive.
How to defend against Coinhive and other miner viruses
The best defense against all types of malware is prevention. Here are a few simple actions you can take.
-
Avoid strange links. Don’t click strange-looking or misspelled URLs. When in doubt, you can google the URL and check the description on the results page to verify if the site is legit or not. Avoid clicking on shortened URLs from random places like YouTube comment sections.
-
Double-check emails before downloading attachments or clicking links. Take a look at the email address and determine if it’s fake or not. “[email protected]” is probably fake, because “Facebook” is misspelled. Typos or strange ways of writing are other signs of spoofed email. And always be wary of phishing emails that ask you to input your password or other personal info.
-
Use an anti-mining browser extension. Certain extensions like minerBlock can block websites from forcing your computer to mine cryptocurrency. Research an extension thoroughly before installing it, and make sure you have a strong antivirus to protect you in case any extensions or apps turn out to be malicious.
-
Check Task Manager periodically. In the Processes tab, you can see which processes are consuming the most resources. Internet browsers can get up there with their memory usage, especially if you’ve got tons of tabs open. But if there’s some unexplained activity, or if your CPU is showing 90% usage even though few tabs are open and other programs are closed, you should probably investigate further.
Protect yourself with strong antivirus software
AVG AntiVirus FREE is exceptionally robust security software. Not only will it protect your computer with real-time security updates, but it will also scan your machine for both malware and performance issues, catching malicious downloads before any infections have the chance to burrow in.
And with its all-new, refreshingly simple design, AVG AntiVirus FREE keeps you safe without bogging you down. Download and install it today to block all the types of malware discussed above, including sneaky fileless malware. Get 24/7 protection, completely free.











